An emerging model of remote access provides the benefit of a tunnel for broad application support while retaining strong control over access to applications through the next-generation firewall security policy. This approach allows administrators to safely enable remote user activity and access on the network.
Full Answer
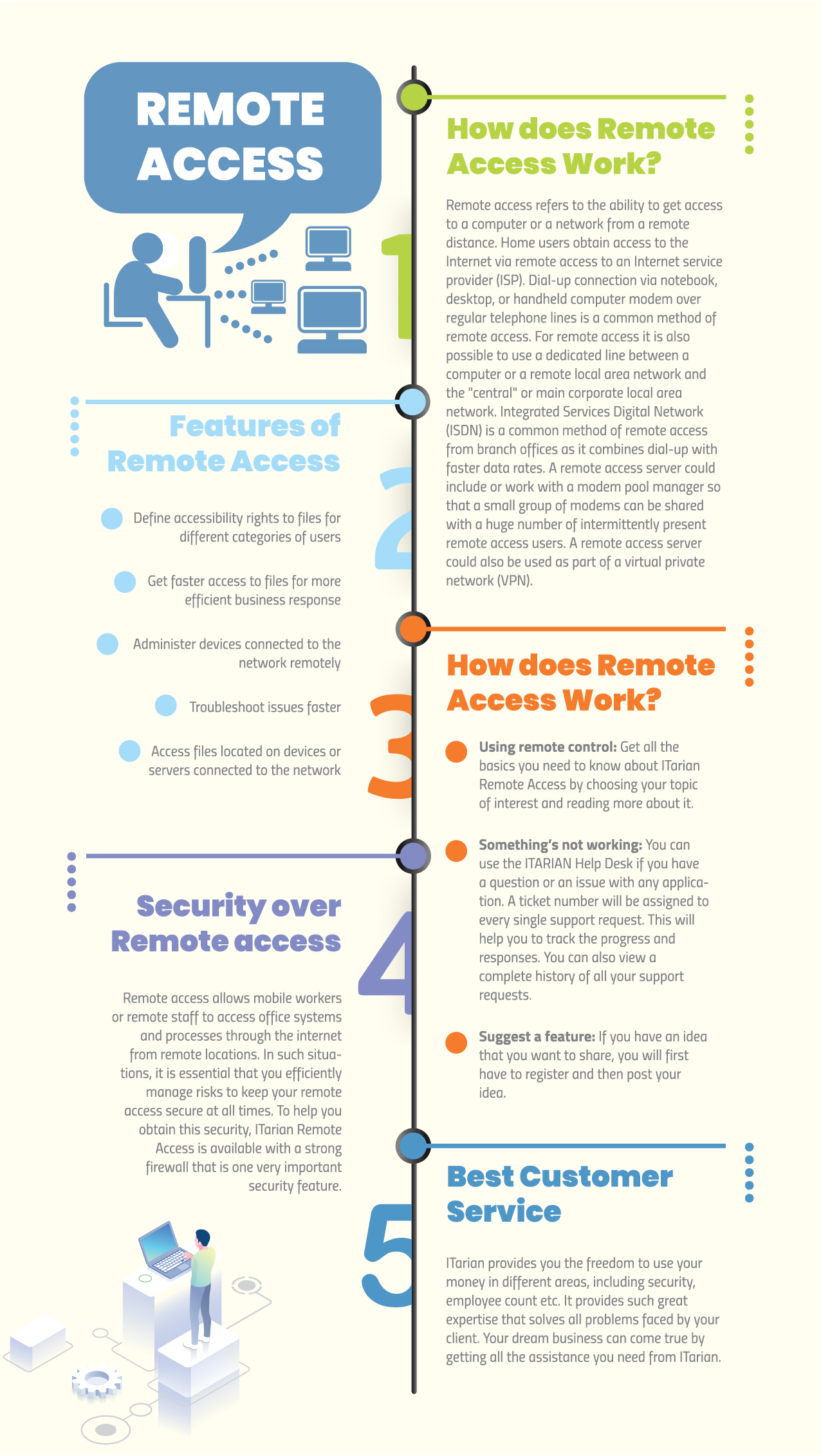
What is remote access?
Remote Access. Definition - What does Remote Access mean? Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location.
How do I set up remote access?
Remote access can be set up using a local area network (LAN), wide area network (WAN) or even a virtual private network (VPN) so that resources and systems can be accessed remotely. Remote access is also known as remote login. Remote access can be established via a line that runs between a computer and a company's local area network (LAN).
What are the different types of remote access networks?
This type of network uses encryption and tunneling to access a company's network. This can be a great choice for a relatively small organization. Other means of establishing remote access include the use of an integrated services digital network, wireless network, cable modem or digital subscriber line.
What is the best free Remote Access program?
Remote Utilities is a free remote access program with some really great features. It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.

What is remote access model?
Remote access model All read/write requests to a file are processed on the server. Upload/download model When a client opens a file, a copy of the file is transferred (downloaded) to the client. All the subsequent read/write operations are done on the local machine.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
What is remote server access?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are remote devices?
Remote Device means any device acceptable to us from time to time that provides for the capture of images from Items and for transmission through the clearing process.
What is a remote server example?
Remote Web Servers Opposite to the local server, remote server refers to a computer that is remotely located having a web server software, database and other resources to handle remote requests sent by the users of a website. A remote server may host single or multiple websites.
What is the difference between local server and remote server?
If you are referring to a Local Server, this means that you have a server setup on your current machine. When the server is Remote, this just means that it is on another computer.
What are the examples of remote assistance?
Examples include file transfer, remote print, chat, session recording, screen sharing, and more. By being able to remotely access a device to provide support, IT support teams, help desks, and managed service providers can resolve support tickets quicker.
Why is remote access important?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
What are the benefits of remote access?
Remote access can bring many benefits to a business, from lowering costs to increasing worker satisfaction and productivity.
Why is Citrix remote access important?
Remote access is great for teleworkers, contractors, those who work from home , or individuals displaced from their home office due to natural disaster or other circumstances. It is valuable for businesses to have a strategy for allowing remote access to their users. Employees may have the flexibility to work from home, or have a plan in place if they are not able to go into the office during a natural disaster. View Citrix Remote PC Access
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
What happens when an employee is displaced due to a business continuity disruption?
If an employee has been displaced due to a business continuity disruption, they can continue to be productive using a secure remote access connection.
Why is it important to have a bring your own device?
With remote access, data stays secure and workers can be productive at any location. By allowing employees to use their own device, businesses can exponentially lower the costs of purchasing and managing corporate-owned devices.
How does remote access benefit a business?
Remote access can bring many benefits to your business, from lowering costs to increasing worker satisfaction and productivity.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
How does secure remote access work?
Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
What is zero trust security?
A zero trust security posture reduces the threat surface and minimizes the threat windows during which attackers can inflict damage, helping to protect against everything from simple malware to advanced persistent threats.
Can you store credentials in endpoint?
Instead of requiring privileged users to know usernames and passwords for each endpoint, we can store those credentials securely. With Credential Injection, those credentials are retrieved and injected directly into a session.
Future of the VPN
"VPNs represent significant liabilities, hamper productivity and introduce latency," said Anurag Kahol, CTO of Bitglass, a data and threat protection company in Campbell, Calif. "They can be difficult to scale and can grant excessive access to internal resources."
Moving toward SASE
To take the place of perimeter-based security tools, enterprises are looking to cloud-based SASE frameworks to protect an increasingly disparate and cloud-based enterprise network. The ultimate goal of a SASE framework is to unify all networking and security tools into a single management dashboard to cut costs and increase agility.
Growing use of zero trust
Zero-trust strategies, which were already gaining traction pre-COVID-19, have seen an uptick as enterprises look to adopt the ZTNA framework to better address modern cybersecurity threats -- including identity- and credential-based attacks, as well as attackers gaining access through the cloud.
The post-pandemic security roadmap
While security is always a main concern, analysts stress consistent performance has equal importance as IT departments strategize for the future.
What is Zoho Assist?
Zoho Assist is yet another remote access tool that has a free edition for both personal and commercial use. You can share screens and files, and chat remotely with the other user through a unique session ID and password.
How to access remote computer?
There are a couple of ways to access the remote computer. If you logged in to your account in the host program, then you have permanent access which means you can visit the link below to log in to the same account in a web browser to access the other computer.
How to connect to a host browser?
To connect to the host browser, sign on to Chrome Remote Desktop through another web browser using the same Google credentials or using a temporary access code generated by the host computer.
How to enable remote desktop access to a computer?
To enable connections to a computer with Windows Remote Desktop, you must open the System Properties settings (accessible via Settings (W11) or Control Panel) and allow remote connections via a particular Windows user.
How does remote utility work?
It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.
What is the other program in a host?
The other program, called Viewer, is installed for the client to connect to the host. Once the host computer has produced an ID, the client should enter it from the Connect by ID option in the Connection menu to establish a remote connection to the other computer.
What is the easiest program to use for remote access?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support.
What Does Remote Access Mean?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
Techopedia Explains Remote Access
Remote access can be established via a line that runs between a computer and a company's local area network (LAN). A connection can also be established between a company's LAN and a remote LAN using a dedicated line. This type of line provides faster speeds but has the drawback of being more expensive.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
How does isolation fail?
This approach typically fails over time if it's implemented as a purely technology approach without processes and training to validate and sustain the defenses. It's easy to fall into a firewall and forget trap by defining the problem as static and technical.
What is the zero trust transformation?
One helpful perspective on the zero trust transformation of access control is that it shifts from a static two-step process of authentication and authorization, to a dynamic three-step process called known, trusted, allowed:
What is a secure access?
Secure: Explicitly validate the trust of users and devices during access requests, using all available data and telemetry. This configuration makes it more difficult for attackers to impersonate legitimate users without being detected. Also, the access control strategy should focus on eliminating unauthorized escalation of privilege, for example, granting a privilege that can be used to get higher privileges. For more information on protecting privileged access, see Securing privileged access.
What is consistent security?
Consistent: Ensure that security assurances are applied consistently and seamlessly across the environment. This standard improves the user experience and removes opportunities for attackers to sneak in through weaknesses in a disjointed or highly complex access control implementation. You should have a single access control strategy that uses the fewest number of policy engines to avoid configuration inconsistencies and configuration drift.
What is enterprise access model?
The enterprise access model is a comprehensive access model based on zero trust. This model addresses all types of access by internal and external users, services, applications, and privileged accounts with administrative access to systems.
What is zero trust?
Zero trust principles help establish and continuously improve security assurances, while maintaining flexibility to keep pace with this new world. Most zero trust journeys start with access control and focus on identity as a preferred and primary control while they continue to embrace network security technology as a key element. Network technology and the security perimeter tactic are still present in a modern access control model, but they aren't the dominant and preferred approach in a complete access control strategy.
Why is it important to have zero trust?
To fulfill the zero trust principle of explicit validation, it's critical to make an informed decision. The zero trust policy engine should have access to diverse data on the users and devices in order to make sound security decisions. This diversity helps to identify these aspects with greater confidence:
What is enterprise access model?
The enterprise access model supersedes and replaces the legacy tier model that was focused on containing unauthorized escalation of privilege in an on-premises Windows Server Active Directory environment.
What is an enterprise IT?
The enterprise IT organization manages and supports the workloads and the infrastructure they are hosted on, whether it's on-premises, on Azure, or a third-party cloud provider, creating a management plane. Providing consistent access control to these systems across the enterprise requires a control plane based on centralized enterprise identity system (s), often supplemented by network access control for older systems like operational technology (OT) devices.
Why is the DevOps split important?
This split ensures focus for protecting business critical systems and administrative roles that have high intrinsic business value, but limited technical control. Additionally, this split better accommodates developers and DevOps models vs. focusing too heavily on classic infrastructure roles.
What is tier 0?
Tier 0 expands to become the control plane and addresses all aspects of access control, including networking where it is the only/best access control option, such as legacy OT options
What is the primary store of business value that an organization must protect?
The primary stores of business value that an organization must protect are in the Data/Workload plane: The applications and data typically store a large percentage of an organization's: Business processes in applications and workloads. Intellectual property in data and applications.
Who manages privileged access pathways?
Finally, these systems must be managed and maintained by IT staff, developers, or others in the organizations , creating privileged access pathways. Because of the high level of control they provide over business critical assets in the organization, these pathways must be stringently protected against compromise.