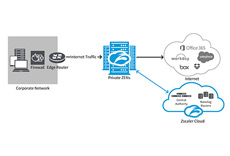
Zscaler Privileged Remote Access is a cloud- delivered zero trust access solution that enables fast, secure, and reliable connectivity to OT and IIoT devices from field locations, the factory floor—or anywhere.
Full Answer
What is secure remote access for OT systems enabled by Zscaler?
Secure remote access for OT systems enabled by Zscaler Private Access is a ZTNA service that takes a user- and application-centric approach to OT security.
What is Zscaler Private Access?
No ability to provide application segmentation Zscaler Private Access (ZPA) is a cloud service from Zscaler that provides seamless, zero trust access to private applications running on public cloud or within the data center. With ZPA, applications are never exposed to the internet, making them completely invisible to unauthorized users.
What are the benefits of ZPA integration with Zscaler digital experience?
ZPA integration with Zscaler Digital Experience provides full visibility into traffic, for faster troubleshooting and improved user experience. Authorized users have access to specific private apps without the need to access the network, reducing the risk of lateral movement and the spread of ransomware.
What is privileged remote access and how does it work?
Privileged Remote Access enables security professionals to control, monitor, and manage privileged access to critical systems. Privileged Remote Access eliminates the need for privileged users to remember or share credentials for the systems they need to access. Passwords can be stored in the on-appliance vault.

What is privileged remote access?
Privileged remote access is about ensuring employees, third-party vendors, and other insiders don't have free access to systems while accessing the network remotely. You're able to define who has permissions, when they have it, and the appropriate level of access each role needs to complete their work.
What is zscaler remote access?
The Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network.
Is Zscaler private access a VPN?
Zscaler Private Access: A VPN alternative that delivers a zero trust model. Zscaler Private Access (ZPA) is a cloud-delivered, zero trust network access (ZTNA) service that provides secure access to all private applications, without the need for a remote access VPN.
What is the difference between Zscaler and VPN?
ZPA is an easier to deploy, more cost-effective, and more secure alternative to VPNs. Unlike VPNs, which require users to connect to your network to access your enterprise applications, ZPA allows you to give users policy-based secure access only to the internal apps they need to get their work done.
Is zscaler a firewall?
Zscaler Cloud Firewall enables fast, secure on- and off-network connections and local internet breakouts for all your user traffic, without any hardware or software to manage.
What is remote access in VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How does zscaler VPN Work?
Zscaler Private Access (ZPA) is a cloud service from Zscaler that provides seamless, zero trust access to private applications running on the public cloud or within the data center. With ZPA, applications are never exposed to the internet, making them completely invisible to unauthorized users.
How do I enable remote Assistance on zscaler?
To enable remote assistance:Log in to the ZPA Admin Portal.Select the Help menu ( ), then Remote Assistance.In the Remote Assistance window that appears: Select All to enable read-only admin access for Zscaler Support engineers. Select None to disable read-only admin access for Zscaler Support engineers.
What is Zscaler private access?
Secure remote access for OT systems enabled by Zscaler Private Access is a ZTNA service that takes a user- and application-centric approach to OT security. Whether a user is an employee, contractor, or third-party partner, ZPA ensures that only authorized users have access to specific ICS systems or applications without ever providing access to the OT network. Rather than relying on physical or virtual appliances, ZPA uses lightweight infrastructure-agnostic software like docker containers or virtual machines, paired with browser access capabilities, to seamlessly connect all types of users to OT systems and applications via inside-out connections that are stitched together within the Zscaler Zero Trust Exchange.
What is ZPA browser access?
With ZPA browser access service, third-party partners and users gain secure access to OT systems without the need for a client. Partners no longer need to jump through hoops to securely access OT systems—they simply use their own device to effortlessly access them over the internet. The outcome is highly controlled third-party access that allows users to connect to OT systems from any device, any location, at any time.
How does ZTNA eliminate attack surface?
After: ZTNA solutions eliminate this attack surface by making the OT systems invisible. The best defense against unpatchable OT systems is to maintain the best possible air gap between IT and OT.
Can a user leverage a browser to gain access to authorized ICS systems?
After: Regardless of the device or location, a user can simply leverage a browser to gain access to authorized ICS systems.
What is ZPA service?
With ZPA, applications are never exposed to the internet , making them completely invisible to unauthorized users. The service enables the applications to connect to users via inside-out connectivity versus extending the network to them. Users are never placed on the network.
What is ZPA API?
ZPA API and ML enhancements simplify zero trust for IT by automatically creating access policies for discovered apps and generating auto-segmentation of app workloads.
What company uses ZPA?
NOV, a 150-year-old oil and gas company , uses ZPA to enable zero trust for more than 7,000 apps and 10,000 users. Growmark, a U.S.-based agricultural supply cooperative, enabled zero trust access to SAP and cloud apps with Zscaler’s ZTNA technology.
Is ZPA segmentation difficult?
With ZPA, enterprises no longer need to perform complex network segmentation. Admins have the granular control to decide who can access what, even down to the individual application and user level.
How to adopt modern least privilege access?
To adopt modern least-privilege access, organizations need to re-evaluate a FW approach to network segmentation and opt for a more granular approach that enables user-to-app segmentation.
What is least-privileged access?
As cyberattacks and the exposed attack surface have increased, the need to enable zero trust, based on the principle of least-privileged access, has become a priority for many organizations. But what does least-privileged access really mean?
What is ZTNA access?
ZTNA gives surgical like connections from identified and verified users to authorized applications, making lateral movement impossible. This greatly reduces attack surface. ZTNA enable zero trust access both to remote users and on-premise users so access policies are universals regardless of the user’s access location. All while users never are placed on the corporate network.
What is the least privilege?
Least-privileged access – is the idea that any given user should be granted the minimum level of access necessary to perform their assigned function. Least-privileged access may be known by a few names such as the principle of minimal privilege (POMP) or the principle of least authority (POLA), but what is consistent across all terms is ...
Where does least privilege access start?
Least-privileged access starts at the base layer of “are your users who they say they are”.
Does ZPA use Azure AD?
So if you have an active AD account with CSM Bakery, and you launch ZPA to connect, then we authenticate you with our active directory. If you don’t have an active directory account, you can’t get in.
What is privileged remote access?
Privileged Remote Access gives you the ability to centrally secure and manage access across all of your environments, even sensitive systems in the Cloud.
What is advanced web access?
Advanced Web Access can be configured to work across any solution that leverages a web interface for management including; Amazon Web Services, Google Cloud, VMware vSphere, Citrix XenServer, Microsoft Hyper-V, Microsoft Azure, IBM Softlayer, and Rackspace.
What is zero trust security?
A zero trust security posture reduces the threat surface and minimizes the threat windows during which attackers can inflict damage, helping to protect against everything from simple malware to advanced persistent threats.