Full Answer
What is remote access trojan (RAT)?
What is Remote Access Trojan (RAT)? A remote access Trojan (RAT) is a malware program that opens a backdoor, enabling administrative control over the victim’s computer. RATs are typically downloaded together with a seemingly legitimate program, like a game, or are sent to the target as an email attachment.
Was a remote access Trojan installed in two npm packages?
The security team behind the " npm " repository for JavaScript libraries removed two npm packages this Monday for containing malicious code that installed a remote access trojan (RAT) on the computers of developers working on JavaScript projects.
Why is JavaScript so hard to detect in antivirus?
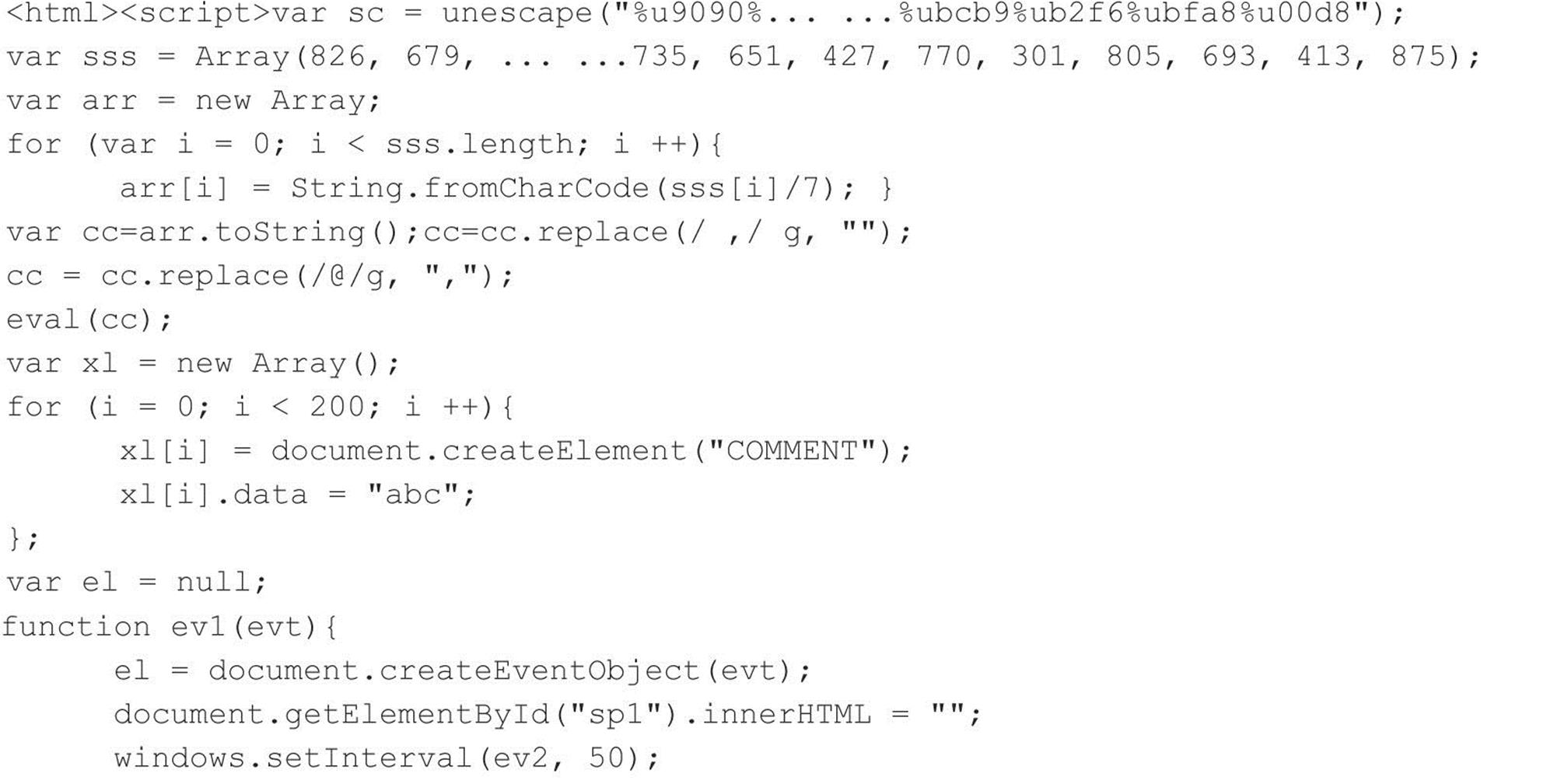
Also, because JavaScript code can be obfuscated, it easily bypasses antivirus detection, allowing it to filter through undetected. The attackers in this case are most likely familiar with their targets.

What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
Can malware writers name processes?
For most applications and processes, you can identify any suspicious content in this window, but malware writers name processes to make them look official. If you find any suspicious executables and processes, search online to determine if the process could be a RAT or other type of malware.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is a jsoutprox?
JsOutProx is a fully functional JavaScript remote access trojan (RAT) first discovered in December of 2019. The tactics, techniques, and procedures (TTPS) of the attackers behind JsOutprox indicate that these are experienced and sophisticated threat actors.
How long does it take to decrypt JavaScript?
A decryptor must be used to figure out what this threat does. Depending on resources, it may take several hours to decrypt the script. In the end, however, it becomes more readable. Figure 3.
Is there any historical data for myabiggeojs.myftp?
Other than this, no other historical campaigns nor historical data could be found for either the domain or IP address used in this attack. It could be surmised that the attacker may be switching back and forth between hosts and DDNS aliases to thwart further analysis. Regarding the 151.106.60 [.]163 IP address, only myabiggeojs.myftp [.]biz:9895 URLs were associated.
Can a RAT be executed in JavaScript?
One of the first things we noticed is that this RAT can be executed both as a JavaScript file on the command line, or as a . HTA file inside a window (in this case, inside mshta.exe). If it is inside a window, the threat tries to hide the window by resizing it to a height of zero pixels and a width of 0 pixels. Moreover, it gets moved to outside of the user’s viewable desktop for further evasion.
Can a screen capture be used to monitor what the user is seeing?
Its ’capture’ function can take a screenshot of the user’s desktop in order to monitor what the user is seeing. The plugin also allows the attacker to operate the infected machine using a virtual keyboard and mouse. Previously, attackers could execute shell commands and file manager functionality such as copy and execute. With this new plugin however, the attacker is virtually sitting in front of the infected machine. Interestingly enough, the screenshell plugin also lumps in the option to execute either .HTA files or java (.jar) files, as seen in the screenshot below.
Is Jsoutprox obfuscated?
JsOutProx also incorporates heavily obfuscated code and the use of Powershell to further along their endeavours. This playbook highlights updates not noted elsewhere for this relatively new malware family, as well as obeservations from FortiGuard Labs on the reuse of the infrastructure in other historical campaigns.
What is DB JSON?
The name of the two packages was jdb.js and db-json.js ., and both were created by the same author and described themselves as tools to help developers work with JSON files typically generated by database applications.
Is RAT malware considered a serious incident?
Since infections with any type of RAT-like malware are considered severe incidents, in security alerts on Monday, the npm security team advised web developers to consider their systems as fully compromised, if they installed any of the two packages.