Hi The real fact is that the person that you allowed to remotely connect to your computer is a criminal. When you gave permission for the criminals to access your computer, they are not removing any virus, or fixing the computer, they are actually stealing all of the personal information on your hard drive.
Full Answer
How do I enable remote access to my computer?
Click Show settings to enable. As needed, add users who can connect remotely by clicking Select users that can remotely access this PC . Members of the Administrators group automatically have access. Make note of the name of this PC under How to connect to this PC. You'll need this to configure the clients.
Why should I allow remote connections to my PC?
When you allow remote connections to your PC, you can use another device to connect to your PC and have access to all of your apps, files, and network resources as if you were sitting at your desk.
What are the chances of my computer being remotely accessed?
The chances of your specific computer being remotely accessed, while not impossible, are very low. You can take steps to help prevent intrusions. Thanks! ↑ Yaffet Meshesha. Computer Specialist. Expert Interview. 22 September 2020. ↑ Yaffet Meshesha. Computer Specialist. Expert Interview. 22 September 2020. ↑ Yaffet Meshesha. Computer Specialist.
How do I know if my computer has remote access programs?
Look for remote access programs in your list of running programs. Now that Task Manager or Activity Monitor is open, check the list of currently-running programs, as well as any programs that look unfamiliar or suspicious. These programs are popular remote access programs that may have been installed without your permission:
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
How do I remove remote access from my computer?
Open System and Security. Choose System in the right panel. Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab. Click Don't Allow Connections to This Computer and then click OK.
Can someone remote into my computer without me knowing?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
How can I tell who is accessing my Remote Desktop?
Click Remote Client Status to navigate to the remote client activity and status user interface in the Remote Access Management Console. You will see the list of users who are connected to the Remote Access server and detailed statistics about them. Click the first row in the list that corresponds to a client.
How do you know if your PC is being monitored?
How to Check If Your Computer Is Being MonitoredLook for Suspicious Processes. Suspicious processes may indicate that your computer is being monitored. ... Run Antivirus Software. Antivirus software can reveal whether or not your computer is being monitored. ... Evaluate Ports. Another tip is to evaluate your network's ports.
How can I tell if my computer is being monitored at work?
Here are the methods to tell if your employer is monitoring your computer:Search for Suspicious Apps in Application Manager. ... Search for Suspicious Background Processes. ... Check Data Usage for Suspicious Activity. ... Search for Suspicious Programs. ... Check the Firewall Settings.
How can I tell if my computer is being monitored at work 2022?
Right-click on the Taskbar and select Task Manager. On the Process tab, find a program that potentially monitoring the computer. You might want to check out a top monitoring software to help you determine the name. If you found one exact same name, it means you are being monitored.
How do I know if someone is using Teamviewer on my computer?
To check, click on the up arrow in the bottom right hand corner of your screen. Look for the teamviewer icon depicted in the picture below in the blue circle. Click on the small icon and you should see the teamviewer window appear.
How can I see what devices are connected to my computer?
0:221:07Find Out Which USB Devices Have Been Connected to Your PCYouTubeStart of suggested clipEnd of suggested clipUp select your view by and select category field and then select hardware and sound. And now youMoreUp select your view by and select category field and then select hardware and sound. And now you want to select devices and printers up at the top.
How do you check if laptop has been tampered?
Under Windows Logs, right-click on System, choose Filter Current Log, find the Event Sources dropdown menu, select Power-Troubleshooter and click OK. This should present you with a list of all the times your laptop was woken up.
How to stop someone from accessing my computer?
This includes removing any Ethernet cables and turning off your Wi-Fi connections.
How to install antivirus on another computer?
If you don't have an antivirus, download an installer on another computer and transfer it to your computer via USB. Install the antivirus and then run a scan with it.
What to do if your computer is compromised?
Change all of your passwords . If your computer was compromised, then there’s a possibility that all of your passwords have been recorded with a keylogger. If you’re sure the infection is gone, change the passwords for all of your various accounts. You should avoid using the same password for multiple services.
Why is public Wi-Fi so dangerous?
Try to avoid public Wi-Fi spots. Public Wi-Fi spots are risky because you have zero control over the network. You can't know if someone else using the spot is monitoring traffic to and from your computer. By doing this, they could gain access to your open browser session or worse. You can mitigate this risk by using a VPN whenever you are connected to a public Wi-Fi spot, which will encrypt your transfers.
What to do if you can't get rid of intrusion?
If you're still experiencing intrusions, or are concerned that you may still be infected, the only way to be sure is to completely wipe your system and reinstall your operating system.
Why does my computer turn on without my input?
If your computer appears to turn on without your input when you're not using it, it is likely waking from Sleep mode to install updates .
How to find out what is running on my computer?
Open your Task Manager or Activity Monitor. These utilities can help you determine what is currently running on your computer.
How to allow remote access to PC?
The simplest way to allow access to your PC from a remote device is using the Remote Desktop options under Settings. Since this functionality was added in the Windows 10 Fall Creators update (1709), a separate downloadable app is also available that provides similar functionality for earlier versions of Windows. You can also use the legacy way of enabling Remote Desktop, however this method provides less functionality and validation.
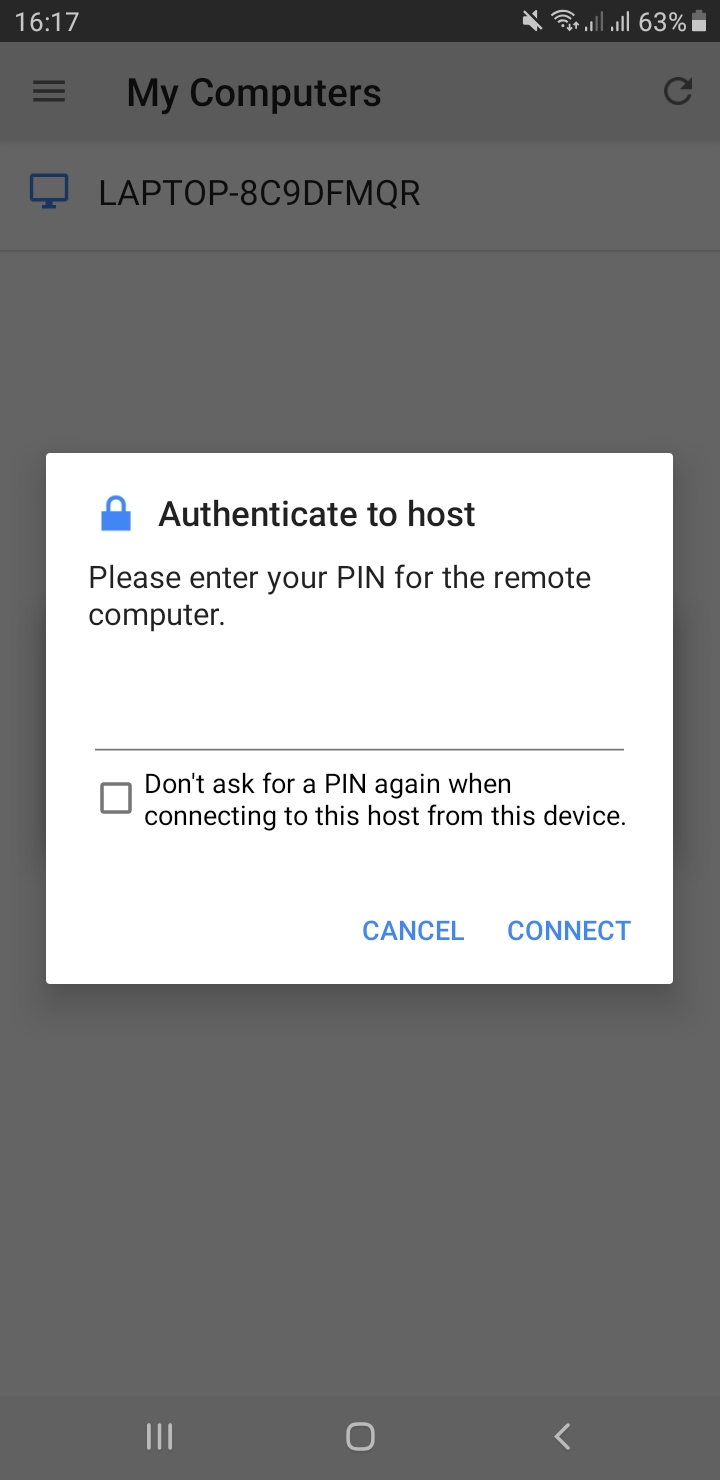
How to connect to a remote computer?
To connect to a remote PC, that computer must be turned on, it must have a network connection, Remote Desktop must be enabled, you must have network access to the remote computer (this could be through the Internet), and you must have permission to connect. For permission to connect, you must be on the list of users. Before you start a connection, it's a good idea to look up the name of the computer you're connecting to and to make sure Remote Desktop connections are allowed through its firewall.
How to remotely connect to Windows 10?
Windows 10 Fall Creator Update (1709) or later 1 On the device you want to connect to, select Start and then click the Settings icon on the left. 2 Select the System group followed by the Remote Desktop item. 3 Use the slider to enable Remote Desktop. 4 It is also recommended to keep the PC awake and discoverable to facilitate connections. Click Show settings to enable. 5 As needed, add users who can connect remotely by clicking Select users that can remotely access this PC .#N#Members of the Administrators group automatically have access. 6 Make note of the name of this PC under How to connect to this PC. You'll need this to configure the clients.
Should I enable Remote Desktop?
If you only want to access your PC when you are physically using it, you don't need to enable Remote Desktop. Enabling Remote Desktop opens a port on your PC that is visible to your local network. You should only enable Remote Desktop in trusted networks, such as your home. You also don't want to enable Remote Desktop on any PC where access is tightly controlled.
How to run JRT as administrator?
Run the tool by double-clicking it. If you are using Windows Vista, 7, or 8; instead of double-clicking, right-mouse click JRT.exe and select "Run as Administrator". The tool will open and start scanning your system. Please be patient as this can take a while to complete depending on your system's specifications.
Can I use the programs below to clean, remove adware and remove malware?
You can use the programs below to clean, remove adware and remove malware. Though I doubt the criminals installed any, it would be a good idea
Can you rerun MBAM?
Rerun MBAM and be sure to allow it to remove that one threat that it found .
How to tell if a computer is a scam?
This then leads to the scam’s hook. While accessing your machine several things may happen: 1 The scammer installs malware. 2 The scammer “discovers” that in order to fix your (non existent) problem you’ll need to purchase something and at this point, they ask for your payment information. 3 You’re quoted a high price for this “service”. 4 Your payment information may be used not only for that quoted fee, but for other purchases you haven’t authorized.
Why doesn't Microsoft call people?
Microsoft doesn’t call people because of errors on their computers. Neither do ISPs, security companies, or pretty much anyone else who might have some role of internet authority. To quote Admiral Akbar: “It’s a trap!”. In recent years (yes, years) I’ve been getting lots of reports of this scam and its variants.
How to know if a scammer is gone?
Assume the worst. Revert to a system image backup taken before the access was granted. If you don’t have such a backup, then backup your data , reformat, and reinstall Windows. This is the only way to know that whatever the scammer might have left on your machine is truly gone.
What to do if you are concerned about a real problem?
If you’re concerned that there is a real problem, do the research yourself, or contact the technical resources that you trust and ask them about it.
What does it mean when someone says your computer is crashing?
They claim that they’ve detected that your computer is causing many errors on the internet or that there are “problems with your account”. To prove that there’s something wrong, they ask if your computer has been crashing recently. Or they have you open up the event viewer and point out the many, many errors listed there.
Is Microsoft a scam?
The scam is very simple: someone calls you claiming to be from Microsoft or your ISP or your anti-malware provider, or some other authoritative company. Of course, they are not . Microsoft, your ISP or any of the other companies these scammers claim to be from are not involved in any way.
Is Logmein a scam?
Important: Sites like logmein.com and other remote-access services are not involved in the scam. They’re just web services that the scammer uses as a vehicle for accessing your machine. This then leads to the scam’s hook. While accessing your machine several things may happen: The scammer installs malware.