How to hack an iPhone remotely?
To hack an iPhone remotely using Spyic takes a few steps. Here are the steps to follow: Step 1: Visit Spyic official website and sign up for an account. Ensure you subscribe to a plan that suits your iPhone hacking needs. Step 2: Provide information about the target user such as name, age, and OS.
How do hackers hack WiFi networks?
How Hackers Hack Wi-Fi 1 Sniffing. There are several ways how hackers can gain access to a public WiFi network and infiltrate connected devices to steal data. 2 Spoofing. You may have noticed that your smartphone or laptop automatically connects to networks that they have been connected to previously. 3 Wardriving. ... 4 Encryption Cracking. ...
How to crack WPA protected Wi-Fi passwords?
CloudCracker is an online password cracking tool for cracking WPA-protected Wi-Fi networks. This tool can also be used to crack different password hashes. Just upload the handshake file, enter the network name, and start the tool. This tool has a huge dictionary of around 300 million words to perform attacks.
How do I use wlan0mon?
wlan0 : First wireless network interface on the system. ( This is what we need.) Step 2: Stop the current processes which are using the WiFi interface. Step 3: To start the wlan0 in monitor mode. Step 4: To view all the Wifi networks around you. wlan0mon : Name of the interface (This name can be different on the different devices)
How to protect your wifi from being hacked?
Who discovered the new wifi hacking method?
Why is wifi hacking so popular?
Why is wifi safer?
What is EAPOL in LAN?
See 2 more
About this website
Is it possible to hack WiFi WPA2?
Yes,it is because nowadays it is not very secure. You can hack these Networks with apps like WPA Tester,Android Dumper. These Apps work on Android. If you want to hack it with a pc,Use Aircrack-ng,Wireshark.
Can iPhone hotspot be hacked?
In shocking new research, security specialist AirEye has shown how so-called Format String Bugs (at the heart of the aforementioned iPhone WiFi hack) can now be weaponized to turn the simple act of joining a WiFi hotspot into a security nightmare. And it can impact any device on any platform.
Can iPhone be hacked into remotely?
An iPhone can be hacked remotely through iOS vulnerabilities. However, it's more likely that it'll be hacked through malicious software or physical access, as programming-based hacking is the most difficult to carry out.
How do I find my WiFi WPA2 password on my iPhone?
To find your WiFi password on an iPhone, go to Settings > Apple ID > iCloud and turn Keychain on. On your Mac, go to System Preferences > Apple ID > iCloud and turn Keychain on. Finally, open Keychain Access, search for your WiFi network'sname, and check the box next to Show Password.
Can you hack mobile hotspot?
0:033:45How to Hack a Wireless Hotspot Using Your Android Phone - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd see if somebody is connecting. And then capture the handshake. Between that authorized user andMoreAnd see if somebody is connecting. And then capture the handshake. Between that authorized user and the router that you are trying to connect to or the mobile hotspot that you are trying to connect.
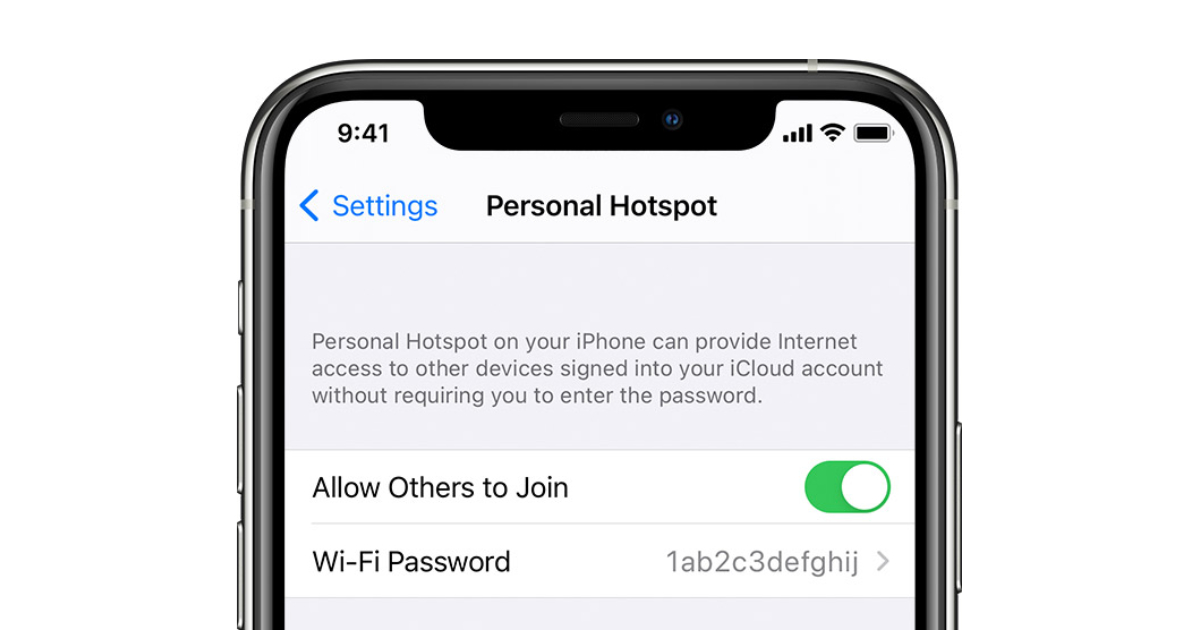
Can anyone connect to my iPhone hotspot?
You can set up Family Sharing so that your family can join your Personal Hotspot automatically—without needing to enter the password. Here's what to do: On your device with Personal Hotspot, go to Settings > Personal Hotspot > Family Sharing.
What is the best spyware for iPhone?
Top 10 BEST Phone Spy Apps For Android And iPhone In 2022Comparing Best Cell Phone Spying Apps.#1) mSpy.#2) Cocospy.#3) XNSPY.#4) uMobix.#5) Mobilespy.at.#6) Hoverwatch.#7) eyeZy.More items...•
Is my phone being remotely accessed?
How to Tell Someone Is Accessing Your Phone Remotely. Here are some signs that someone might have unauthorized access to your smartphone: Unknown apps are running in the background. Your phone has an increased closing time and is slower overall.
How do I know if my iPhone is linked to another device?
From the Devices section of your Apple ID account page, you can see all of the devices that you're currently signed in to with your Apple ID, including Android devices, consoles, and smart TVs: Sign in to appleid.apple.com,* then select Devices.
What is a WPA2 password for hotspot?
WPA2 password is the second generation protocol of Wi-Fi Protected Access. WPA2 password is used to protect your home Wi-Fi network from unauthorized access. Released in 2006, it has survived the test of time when it comes to network protection.
What's a WPA2 password on iPhone?
To password protect access to your Wi-Fi network you will need to supply your Airport device with a password. The WPA2 part is the type of security that will be used along with your password to prevent unauthorized access to your network.
How do I enable WPA2 on my iPhone?
Once in the settings pages, go to the wireless settings. You should be able to find a drop down menu for the security options. Change it to use WPA2 only, or WPA2/WPA3 if you have that option. Save the settings (the router may tell you it has to be restarted).
Can someone using my hotspot see my history?
Can Wi-Fi Owners see what you Search? To be precise, the answer to this question is “Yes”. You can be monitored by the owners of the Wi-Fi.
Can someone connect to my hotspot without password?
What this means is that when you create a hotspot on your Android smartphone, Android doesn't create a password to the hotspot and, as a result, anyone can connect to the network at will. If you are in a public place, someone can choose to use your expensive bandwidth and unapologetically use it up.
How can you tell if someone is using your hotspot?
How to see who is connected to your hotspot on Android?Swipe down from the top of the screen.Tap the gear-like icon to access the Settings menu.In the Settings menu, tap on Tethering & portable hotspot.Tap on Wi-Fi hotspot.See the number of connected users and their MAC addresses under Connected Users.
How do I make my hotspot secure?
Turn on your hotspot by going to Settings, Cellular and then Personal Hotspot, and tap the slider next to Allow Others to Join. There, you also can set up a password. If you have an older version of iOS, your phone will automatically terminate the hotspot connection when the device you're tethered to locks itself.
How To: Hack WiFi Passwords Using the Command Line (Windows 10)
This is confirming the files were successfully saved. If you have multiple networks you will see multiple files listed here. For this example, the file can be seen as “c:\WiFi-o2-WLAN02.xml”.
How to Hack WPA WiFi Password - WPA2 Software Finder - SecPoint
How to Hack WPA WiFi Password. State of the art Wi-Fi Pen Testing Portable Penetrator Software you can recover WPA WiFi Password. Find out if your WPA WPA2 WiFi password is wide open to attackers.
Why should we know how to hack into an iPhone?
Why should we know how to hack into an iPhone? Sometimes, it becomes really important to keep an eye on children, employees, or other loved ones. To access information out of their smartphones, you have to take the abrasive step of hacking. It is the best way to keep track of your kids’ activities on their smartphones. By doing this, you keep updated on what your children or employees are up to.
What is the most popular hacker app for iPhones?
mSpy is the most popular hacker application for iPhones due to its wide range of features. It is recommended by various social media portals for its excellent monitoring capabilities. You are not required to look at other applications while using mSpy.
What is the most expensive hacking app?
SpyEra tracks essential information like messages, chats, and location and monitors activities such as Skype, multimedia files, and other installed apps. It sends an alert if the target device owner changes SIM cards. The only drawback of SpyEra is that it is the most expensive hacking app on this list.
Does Spymaster Pro need jailbreak?
It gives a sense of authority regarding controlling the device. There is no need for jailbreak as well as of installing the application on the target device. It tracks messages, videos, apps, location, and various other things in order to keep an eye on each and every activity of your kids, spouse, employee, etc.
Is Xnspy a good hacker app?
Xnspy is a good iPhone hacker app that comes at an inexpensive price. Its features are kind of similar to other hacking apps as mentioned above. It costs a way too less than other leading applications. Its user interface is quite friendly which makes it easier to access Xnspy on any device.
How to hack an iPhone?
Here are the steps to follow: Step 1: Visit Spyic official website and sign up for an account. Ensure you subscribe to a plan that suits your iPhone hacking needs. Step 2: Provide information about the target user such as name, age, and OS. Step 3: Enter the iCloud credentials of the target iPhone and verify it.
What is the best app to hack an iPhone?
It uses the latest technology to track an iPhone via its iCloud backup. Spyic is the best hacking app for iPhone with the ability to hack an iPhone remotely. A
What is the best iPhone hacking app?
Spyic is the best iPhone hacking app. The app works in total stealth since no physical access to the target iPhone is necessary. If you have been looking for the best iPhone hacking app, it is Spyic . The app is regarded as a leader in the phone surveillance industry.
What is spyic app?
As a trusted and powerful remote hacking app for iPhones, Spyic is a distinguished app. The app has gained the trust of millions of users across the world. This app functions as a professional phone surveillance app.
Can you hack an iPhone remotely?
Sometimes, it is important to keep an eye on children, employees, or other loved ones. To access information out of their smartphones , you have to hack an iPhone remotely.
Does Spyic require jailbreaking?
The app does not require jailbreaking the target iPhone for the app to work. Jailbreaking an iPhone compromises its security. What’s more, Spyic doesn’t gather or store personal data on its server.
Can you restrict apps on Spyic?
For instance, you can restrict the use of certain apps if you so wish. So, with Spyic, you get total access to all installed apps on the target iPhone.
How to spy on a phone?
Step 1: Create a Neatspy account. Step 2: Enter the target user’s Apple ID and password into the control panel. Step 3: Go to the Neatspy dashboard. Now you have complete access to the target phone and you can use any of the listed features to control it or spy on it. Sign up for free or the live demo here >>.
What is the best hacking software for iPhone?
Part 2: How to Hack Into Someone’s iPhone. Spyic is yet another one of the best iPhone hacking software in the market. It doesn’t have the same reliability as Neatspy, however, it comes with some impressive features.
What is the most powerful iPhone hacker app?
FlexiSPY is one of the most powerful iPhone password hacker apps in the market. One of the reasons it’s considered to be the most powerful app in the market is because of the advanced features that it gives you access to, such as:
Can you hack an iPhone without jailbreaking it?
Furthermore, with Neatspy, you can hack an iPhone remotely without having to jailbreak it or install any software. All you have to do is gain access to the target user’s iCloud credentials, and you can hack their iPhone.
Is XNSPY a hacker app?
XNSPY is an extremely basic iPhone hacker app. However, it can give you access to some basic features such as reading text messages, checking call logs, internet browser history, location tracking, etc. Furthermore, jailbreaking the target iPhone is necessary for this as well.
Is Neatspy a good hacker?
Neatspy is the most authentic and trustworthy iPhone hacking software in the market . You don’t need to even physically access the target iPhone to hack it. Neatspy saves all of the target user’s information in your control panel. As such, even if the target user deletes certain pictures or messages, you still have access to them.
Can you hack someone's iPhone?
Hacking someone’s iPhone can give you access to a lot of information. It can tell you who they are in contact with, where they go and at what times, what they view online, etc. However, most people seem to be under the impression that hacking someone’s iPhone requires a lot of coding skills.
How to change the wlan0?
Step 1: ifconfig (interface configuration) : To view or change the configuration of the network interfaces on your system. wlan0 : First wireless network interface on the system. ( This is what we need.) Step 2: Stop the current processes which are using the WiFi interface. Step 3: To start the wlan0 in monitor mode.
How to stop a process when you have found the target network?
Press Ctrl+C to stop the process when you have found the target network.
What is the best way to hack an iPhone?
mSpy is a the best cell phone spy tool which can also be sued to hack an iPhone. It tracks iPhone activities from your iPhone/Android/PC and tells you what's going on. It can spy on any iOS device without physically accessing it. All you need is the iCloud account details of the target user to start hacking their iPhone from another iPhone easily.
How to create an iPhone spy account?
Head over to the mSpy iPhone Spy App official website. You’ll need to choose your plan and create a password in order to create an account.
What is the Hike Messenger app?
Hike Messenger Tracking: A popular social media app Hike is available to users globally. This app can be used for sharing texts and photos. mSpy iPhone Spy App App can be used to spy all Hike chats.
What is the spy app for Skype?
Skype Messenger Spy: The process to monitor all Skype conversations including multimedia files transferred over the devices got way simpler with mSpy iPhone Spy App.
Can you spy on someone on the phone?
You can track their whereabouts, know where they go for work, which other people they meet when-- You can spy on whom they call and what they say over the phone.
What is wireless hacking?
Wireless hacking tools are designed to help secure and attack these wireless networks. Some are designed to help gain access to the network password and the network itself. Others provide information about the structure and traffic flowing over the network, informing later attacks.
How to get unauthorized access to a network?
To get unauthorized access to a network, one needs to crack these security protocols. Many tools can crack Wi-Fi encryption. These tools can either take advantage of WEP weaknesses or use brute force password guessing attacks on WPA/WPA2/WPA3.
What is the best tool to crack WEP?
These are the popular tools used for wireless password cracking and network troubleshooting. 1. Aircrack-ng. Aircrack-ng is one of the most popular wireless password cracking tools that you can use for 802.11a/b/g WEP and WPA cracking.
What is wireless network?
Wireless networks are based on IEEE 802.11 standards defined by the Institute of Electrical and Electronics Engineers (IEEE ) for ad hoc networks or infrastructure networks. Infrastructure networks have one or more access points that coordinate the traffic between the nodes.
What is wireless monitoring and troubleshooting tool?
Wireless monitoring and troubleshooting tools are basically for network admins and programmers working on Wi-Fi-based software.
What is Airgeddon security?
To accomplish this, it integrates several existing tools and provides a single command-line interface for all of them. This helps to reduce the complexity of performing Wi-Fi security audits because Airgeddon’s CLI walks you through the process and handles interactions with all of the underlying tools.
What is an airjack?
AirJack is a Wi-Fi 802.11 packet injection tool. This wireless cracking tool is very useful in injecting forged packets and taking a network down via a denial of service attack. This tool can also be used for a man-in-the-middle attack on the network.
Why do hackers hack public hotspots?
Hackers exploit our need to remain online and hack public Wi-Fi hotspots so that they can gain access to hundreds of devices simultaneously. This increases their chances of finding whatever they are looking for.
How can hackers hack a WiFi network?
The most common practice that hackers use is called sniffing. This method allows hackers to hijack any packet of data that is being transmitted between a device and a router.
How to crack/hack wireless networks?
When we talk about cracking or hacking wireless networks, we’re basically talking about cracking WEP/WPA keys. If you forgot your Wi-Fi password, you could either reset your router or crack your wireless network.
How Hackers Hack Android Smartphones?
It does not take much of an effort for a hacker to spy on your Android device. All they need to do is send an SMS or an MMS to your phone, which can crack its security when you open it.
How does a hacker do a wardriving?
Wardriving, or access point mapping, is done by spotting and exploiting wireless local area networks while driving around in a car. Hackers do this by carrying a laptop, a wireless Ethernet card, and an antenna to boost the signal.
What is the second type of WiFi security breach?
The second type of breach is usually the outcome of insufficient WiFi security measures and weak passwords that a user sets on their accounts. Leaving a device unlocked also falls in such breaches.
What is the tool that you can use to get your neighbors' wifi password?
Nmap. Ophcrack. These are the tools that one may use to get the wifi password of neighbors. This may be because they lost their WiFi password and are wondering about ways to access their neighbor’s WiFi network. Cracking wireless network keys isn’t a piece of cake, and it takes time and patience.
What happens when someone connects to your hotspot?
When someone connects to your Hotspot, in all likelihood the device that he or she uses will be configured via your Hotspot (i.e. DHCP) and you can use this sceneario to:
What do you use to monitor someone's hotspot?
For monitoring on others device whenever anyone connect to your hotspot, you need to use “ Sniffer”.
What is MITMA hacking?
MITMA (Man in the middle attack): This is one of the methods of hacking a smartphone through a hotspot . Basically if the hacker hosts the hotspot he/she can easily snoop your data while you use their data . They will have access to whatever your surf and login using that hotspot , as the information is passed through their phones they record and decrypt the packets very easily. They can even swap images , redirect you to other websites , install malware , etc
What does Wireshark do?
If you use Wireshark on computer, it will gives you more details. It will also shows which website others are currently using packet capture method. Actually Wireshark is packet tracing and sniffing tool.
What to do if you find suspicious sites?
If you find anything suspicious such as frequent redirection to unknown sites , disconnect from that network immediately!
Can a hacker hack a phone?
It depends on what type of device the hacker is using , if it is a laptop then it is possible for him to him hack into your phone . If he is also using a cell phone then the chances of him hacking your phone are very slim .
Can you connect a hotspot to a phone?
Electronically, you can’t really. There is no connection between the data moving through the hotspot and the phone’s own interface.
What is a link to a virus?
Any link to or advocacy of virus, spyware, malware, or phishing sites. Any other inappropriate content or behavior as defined by the Terms of Use or Code of Conduct. Any image, link, or discussion related to child pornography, child nudity, or other child abuse or exploitation.
Is it good to check your hotspot settings?
It's good to know everything is fine now and no other issues or consequences happen. It's good to check your hotspot settings and other network related as well as your Bluetooth to avoid being controlled externally. it could cost you somehow though if he is using your bandwidth continuously.
Is it good to check your hotspot settings and other network related as well as your Bluetooth to avoid being controlled?
It's good to check your hotspot settings and other network related as well as your Bluetooth to avoid being controlled externally.
How to protect your wifi from being hacked?
So users are highly advised to protect their WiFi networks with a secure password such as making the use of numbers, characters and some special characters as they are difficult to crack. which will save your wifi from being hacked
Who discovered the new wifi hacking method?
This new wifi hacking method was accidentally discovered by Jens Steube (lead developer in popular password-cracking tool Hashcat) while he was analyzing the newly-launched WPA3 protocol.
Why is wifi hacking so popular?
Wifi password hacking has become popular as people are always in search of the free internet. But due to the advancement of technology, hacking wifi, and cracking passwords have become a difficult task to do. The reason the newer wifi protocols have become safer is due to the implementation of WPA/WPA2 (wifi protected access) protocols.
Why is wifi safer?
The reason the newer wifi protocols have become safer is due to the implementation of WPA/WPA2 (wifi protected access) protocols. They made modern routers more secure and less prone to hacking.
What is EAPOL in LAN?
According to Steube (security researcher), previous wifi hacking methods requires someone to log into the network so that attackers can capture EAPOL (Extensible Authentication Protocol (EAP) over LAN ) which is a network authentication protocol used in IEEE 802.1X.
