
“Linux Secure Shell, or SSH, is a protocol used by Linux computers to access remote computers and execute commands securely. It is a replacement for rlogin and rsh. Thus, SSH provides encrypted and secure communications between untrusted hosts over an insecure or untrusted network.
How to configure Remote Desktop Connection between Linux and Windows machines?
However, if Linux with a graphical user interface (GUI) is installed on your machine, you can use the remote desktop protocol and configure remote desktop connection from Linux machines to Windows machines via RDP as well as configuring access from Windows machines to your Linux machines by using this protocol.
What are the requirements for a Secure Remote Desktop Protocol?
Before you can establish a secure remote desktop protocol with a remote machine, there are a few basic requirements to meet: The remote computer must be turned on at all times and have a network connection. The client and server applications need to be installed and enabled.
What is Remote Desktop Protocol and how does it work?
Remote desktop protocol is a popular network protocol that is widely used for connecting to computers remotely in Windows environments to manage them. This protocol can be used for connecting to physical and virtual machines that are running on Windows.
How can I secure a Linux machine on a remote site?
For more security, you can specify the allowed IP addresses or custom networks: Note: If a remote Linux machine on a remote site is in the local network behind the NAT and you need to access that machine via RDP from an external IP address, you can configure port forwarding or VPN connection on a router/firewall on a remote site.
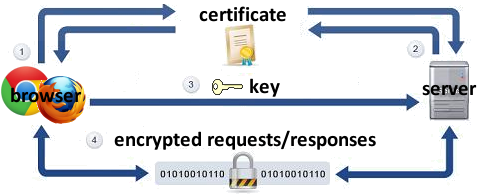
Which protocol is used for encrypted remote access to a server?
IPsec. Internet Protocol security (IPsec) can be used as a remote access tunneling protocol to encrypt traffic going over the Internet.
Is there RDP for Linux?
Install Remmina on Linux Remmina offers several types of connections, including RDP, which is used to connect to Windows-based computers, and VNC, which is used to connect to Linux machines. As you can see in the top-left corner above, Remmina's default setting is RDP.
What are some protocols that can be used for remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
Which protocol is secure remote login?
The Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and virtual network computing (VNC), but RDP is the most commonly used protocol.
What is the best RDP client for Linux?
The best remote desktop for Linux available right nowRemmina. Best remote desktop for Linux overall. ... TeamViewer. Best remote desktop for Linux for beginners. ... VNC Connect. A versatile provider of remote desktop for Linux. ... TightVNC. A remote desktop for Linux with excellent additional features. ... Chrome Remote Desktop.
Is RDP better than VNC?
There are several major differences between VNC and RDP: An administrator and a user on a device can both see the user's screen at the same time. This makes VNC ideal for handholding sessions such as remote customer support and educational demos. RDP is faster and ideal for virtualization.
What is remote access in Linux?
Ubuntu Linux provides remote desktop access. This provides two extremely useful features. Firstly it enables you or another person to view and interact with your desktop environment from another computer system either on the same network or over the internet.
Is SSH encrypted?
SSH encrypts and authenticates all connections. SSH provides IT and information security (infosec) professionals with a secure mechanism to manage SSH clients remotely. Rather than requiring password authentication to initialize a connection between an SSH client and server, SSH authenticates the devices themselves.
Is SSH A protocol?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
How do I install RDP on Linux?
How To Install XRDP (Remote Desktop) on Ubuntu 20.04Step 1 – Install Desktop Environment. By default, Ubuntu Server does not have an installed Desktop Environment. ... Step 2 – Installing XRDP on Ubuntu. ... Step 3 – Configuring Xrdp. ... Step 4 – Adjust Firewall. ... Step 5 – Connect to Remote Desktop.
How do I RDP from Linux to Windows?
Enter as follows:Server field: Use the full domain name of the computer you wish to Remote Desktop (RDP) into. ... User name and password: Replace username with your MCECS username, and put your MCECS password in the password field.Domain: The domain field should be set to “cecs” as shown.
How can I access Linux remotely?
Connect to Linux Remotely Using SSH in PuTTYSelect Session > Host Name.Input the Linux computer's network name, or enter the IP address you noted earlier.Select SSH, then Open.When prompted to accept the certificate for the connection, do so.Enter the username and password to sign in to your Linux device.
How do I access a Linux server remotely?
How to Connect via SSHOpen the SSH terminal on your machine and run the following command: ssh your_username@host_ip_address. ... Type in your password and hit Enter. ... When you are connecting to a server for the very first time, it will ask you if you want to continue connecting.More items...•
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is LCP in PPP?
PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between host and PPP client. LCP allows PPP to support authentication negotiation, in addition to compression and encryption negotiation between the client and the server, using encryption control protocols (ECPs) and compression control protocols (CCPs). PPP can support multiple network protocols by using protocol-specific network control protocols (NPCs). Because it can run over numerous physical media types and features error-checking functionalities, PPP has almost entirely replaced SLIP.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is a SLIP in UNIX?
UNIX developed SLIP as a way of transmitting TCP/IP over serial connections. SLIP operates at both the data link and physical layers of the OSI model and continues to be used today in many network operating systems, as well as UNIX.
Can you use a RAS modem on a Windows server?
With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, dial-up only, or a combination of the two. RAS can only provide LAN access to remote users. It doesn’t let LAN users use the modem to, for example, dial their AOL account.
How to allow remote desktop access?
The first step is to allow connections to be made on the remote machine. To do this click System > Preferences > Remote Desktop. This will bring up a small window (see Figure 1) where you configure allowed connections. You want to take care of this set up as a poorly configured server could allow anyone onto your desktop.
How to remotely access a desktop?
This is, by far, the fastest and easiest method of remotely administering your desktop. Gaining remote access from one machine to another is simple and secure with SSH. You issue the ssh command from your local machine to connect to your remote machine and you can begin to run commands to remotely administer that machine. Typically, the command to connect to a remote machine will look like this:
What is remote desktop viewer?
Remote Desktop Viewer is a different beast. With this tool you are going to be administering using the remote machines complete desktop. For these types of connections to work the remote machine must have a server running allowing connections to be made. Fortunately this is very simple. And fortunately the necessary tools are installed by default in the more recent GNOME desktops. Let’s first take a look at how this is set up.
Can I remotely log into my Linux server?
The next best thing to being there is being able to log into your systems remotely. One of the great things about Linux is the variety of tools you can use to remotely administer your Linux desktop and server systems. From the command line to GUI tools, you can take control of it all right from the comfort of your very own desktop anywhere you ...
Can you use GUI tools on remote machine?
But what if you want (or need) to use GUI tools this way? You can. SSH has the capability of tunneling X protocols built in. This means you can run the GUI tools on the remote machine on your local machine. Why would you want to do this over remotely connecting to the desktop via VNC or Team Viewer? By only using the GUI tools you need you are not slowing down the administrative process by having to process an entire desktop via the network. It’s one tool at a time.
What is a Linux remote desktop?
Vinagre is another remote desktop client for Linux with lots of compelling features for accessing and controlling a remote system. This client is well integrated into the gnome environment. One of the best features of this remote desktop software is it supports VNC server and with multiple connections open simultaneously. It also supports many protocols like RDP, SSH, and VNC.
What is remote access plus?
Remote Access Plus is a remote desktop client software that is generally used by the corporates for easier control of the whole office by controlling the PCs. Users use this software mostly to troubleshoot problems as a team. Remote Access Plus allows video chat and voice calls over the software. The software is fast and secure. The software is not free at all but offers a free trial to its customers.
Can I use SSH on Linux?
Linux has the default SSH remote access tool to perform this sort of job, but as it’s done through the terminal, so many users do not feel comfortable using it. Besides using the terminal, you can also use GUI based remote desktop client for your Linux system.
Can I use Chrome Remote Desktop on Linux?
This list of remote desktop clients will remain incomplete if I don’t mention Chrome Remote Desktop tool. As Google Chrome browser can be used in all devices, including Linux, Windows, Android, macOS, and much more, thus it’s possible to run this free remote desktop software everywhere with less configuration.
Is RealVNC a Windows client?
RealVNC is also a multi-platform, reliable, and easy to use remote access client for Linux, Windows and much more . It offers a unique technology based on VNC screen sharing with add-on products like VNC connect and VNC viewer.
Can an administrator access a server using SSH?
Actually, the administrator doesn’t need anything else except Terminal for installing, controlling, checking or accessing the system. But if you need a GUI tool for accessing a remote desktop, then X11 Window Forwarding is one of the best options available for you.
Is NoMachine a good remote desktop client?
NoMachine is a fast, secure, cross-platform and high-quality remote desktop client based on NX protocol. This protocol can perform really good and gives local speed responsiveness just like you are sitting in front of your computer.
What is remote desktop protocol?
Accessing a remote desktop computer is made possible by the remote desktop protocol ( RDP ), a proprietary protocol developed by Microsoft. It gives a user a graphical interface to connect to another/remote computer over a network connection . FreeRDP is a free implementation of the RDP.
How does RDP work?
RDP works in a client/server model, where the remote computer must have RDP server software installed and running, and a user employs RDP client software to connect to it , to manage the remote desktop computer.
What is XRDP server?
XRDP is a free and open source, simple remote desktop protocol server based on FreeRDP and rdesktop. It uses the remote desktop protocol to present a GUI to the user. It can be used to access Linux desktops in conjunction with x11vnc.
Is FreeNX a SSH server?
FreeNX is an open source, fast and versatile remote access system. It is a secure (SSH based) client /server system , and it’s core libraries are provided by NoMachine. Unfortunately, at the time of this writing, the link to the FreeNX website did not work, but we have provided links to the distro-specific web pages:
Is XRDP good for Linux?
Although, XRDP is good project, it needs a number of fixes such as taking over an existing desktop session, running on Red Hat- based Linux distributions and more. The developers also need to improve its documentation.
What is the protocol used to connect to a remote machine?
There are many ways to establish a connection with a remote machine depending on the operating system you are running, but the two most used protocols are: Secure Shell (SSH) for Linux-based machines. Remote Desktop Protocol (RDP) for Windows-based machines.
How to enable remote access in Windows 7?
Enabling Remote Access in Windows 7, 8, 10 and Windows Server Versions. Step 1: Allow Remote Connections. Step 2: Add Users to the List of Remote Users. How to Use the Remove Desktop Connection Client.
What is SSH?
Secure Shell, sometimes referred to as Secure Socket Shell, is a protocol which allows you to connect securely to a remote computer or a server by using a text-based interface.
What is needed to accept SSH connections?
In order to accept SSH connections, a machine needs to have the server-side part of the SSH software toolkit.
How to get remote desktop on Windows 7?
You can find it in a couple of different ways: For Windows 7, click on Start -> All Programs, go to the ‘Accessories’ folder and click on Remote Desktop Connection.
What is the component of SSH?
On the server’s side, there is a component called an SSH daemon that is constantly listening to a specific TCP/IP port for possible client connection requests. Once a client initiates a connection, the SSH daemon will respond with the software and the protocol versions it supports and the two will exchange their identification data. If the provided credentials are correct, SSH creates a new session for the appropriate environment.
What is SSH client?
An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
What is the most secure file transfer protocol?
The SFTP (SSH File Transfer Protocol) is probably the most widely used secure file transfer protocol today. It runs over SSH, and is currently documented in
How is SSH encrypted?
Once a connection has been established between the SSH client and server, the data that is transmitted is encrypted according to the parameters negotiated in the setup. During the negotiation the client and server agree on the symmetric encryption algorithm to be used and generate the encryption key that will be used. The traffic between the communicating parties is protected with industry standard strong encryption algorithms (such as AES (Advanced Encryption Standard)), and the SSH protocol also includes a mechanism that ensures the integrity of the transmitted data by using standard hash algoritms (such as SHA-2 (Standard Hashing Algorithm)).
Why is SSH key important?
We have found that large organizations have way more SSH keys than they imagine, and managing SSH keys has become very important. SSH keys grant access as user names and passwords do. They require a similar provisioning and termination processes.
How does SSH work?
The protocol works in the client-server model, which means that the connection is established by the SSH client connecting to the SSH server. The SSH client drives the connection setup process and uses public key cryptography to verify the identity of the SSH server . After the setup phase ...
What is SSH protocol?
The SSH protocol (also referred to as Secure Shell) is a method for secure remote login from one computer to another. It provides several alternative options for strong authentication, and it protects the communications security and integrity with strong encryption. It is a secure alternative to the non-protected login protocols (such as telnet, ...
What is public key authentication?
The keys used for authentication are called SSH keys. Public key authentication is also used with smartcards, such as the CAC and PIV cards used by US government. The main use of key-based authentication is to enable secure automation. Automated secure shell file transfers are used to seamlessly integrate applications and also for automated systems ...
What is the most common authentication method?
There are several options that can be used for user authentication. The most common ones are passwords and public key authentication. The public key authentication method is primarily used for automation and sometimes by system administrators for single sign-on.
How to allow remote desktop access to my computer?
Right click My Computer and in the context menu, select Properties. In the System Properties, hit Advanced system settings. In the System Properties window, select the Remote tab and click Allow connections from computers running any version of Remote Desktop. Hit OK to save settings. Notice that Windows Firewall will be tuned automatically to allow inbound connections (TCP port 3389 by default).
How to connect to a remote desktop using RDP?
In the opened window, enter the name of your remote desktop Linux to Windows connection and select RDP as the protocol. In the Basic tab, enter the IP address of the remote host ( 192.168.101.21 in this case), the username (user must be allowed to connect remotely on the target host) and the password of the selected user. Below in the Resolution section, expand the drop-down menu and select the custom resolution, for example, 800x600. When you have configured all necessary connection options, hit Save.
How to connect to Ubuntu Linux?
To connect to your Ubuntu Linux machine, you need to install and configure a remote desktop server on your Linux machine. Xrdp and XFCE must be installed for this purpose. If for some reason you cannot use RDP for Ubuntu, consider using VNC, which is the protocol alternative to RDP.
How to install Remmina on Ubuntu?
How to install Remmina in the GUI. Click the button in the left bottom corner of the Ubuntu Desktop to open the Main Menu (Show Applications). Type rdp in the search bar. You can see that Remmina has been found as the remote desktop client. Click Remmina on this screen.
What is RDP in Ubuntu?
There are three the most used network protocols to manage Ubuntu remotely: SSH (Secure Shell) RDP (Remote Desktop Protocol ) VNC (Virtual Network Computing)
What resolution is used for RDP?
Make sure that a user on a Windows machine has permissions to use RDP. The RDP session is established. However, by default, resolution is about 640x480, and that is too low. You can set the custom resolution for your Ubuntu RDP session when using Remmina for connecting to remote Windows or Linux machines.
How to check if remote desktop is enabled?
Run CMD and execute the ipconfig command to check the IP address of your Windows system on which you have enabled remote desktop connections. In this example, the IP address of the Windows machine is 192.168.101.21.
What is SRTP encryption?
SRTP uses cryptography to provide encryption, message authentication, and integrity, and replay attack protection of the RTP data in both unicast and multicast applications.
Which type of HTTPS is used to secure web connections?
HTTPS which relies on SSL/TLS, is used to secure web connections.
What is FTP over SSH?
The use of FTP over an SSH channel. A protocol for securely uploading and downloading files to and from a remote host.
Why is SSL deprecated?
SSL uses public-key encryption methods to exchange symmetric keys. All versions of SSL have been deprecated due to security issues.
How to make LDAP secure?
directory information. You can make LDAP traffic secure by using it with SSL/TLS by using a certificate.
Can SSH be used in lieu of Telnet?
SSH can be used in lieu of Telnet (which is insecure).
Can FTP client be used for FTPS?
Users are using a variety of FTP client software to connect, however the analyst wants to keep the same port and protocol, while still allowing unencrypted connections, so they could use FTPS.

Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client ...
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll have to set up a PPP session be…
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…