See more
How do I remotely control a Cisco switch?
0:2112:19Cisco router and switch configure remote access (telnet/ssh) - YouTubeYouTubeStart of suggested clipEnd of suggested clipFor telnet in the way we need to do that is we edit the vty lines Pete definitely BTY stands forMoreFor telnet in the way we need to do that is we edit the vty lines Pete definitely BTY stands for virtual terminal 0 to 15. And then we need to tell it we want set a password we'll set that to Cisco.
How do I configure my router for remote access?
All you need to do is type the router IP or default gateway address in the web browser. Next, enter your username and password. Now, once you are in the router's web portal, look for the Remote Management option. Some routers called it Remote Access and it's usually found under Advanced Settings.
What is the use of line Vty 0 4?
VTY is a virtual port and used to get Telnet or SSH access to the device. VTY is solely used for inbound connections to the device. These connections are all virtual with no hardware associated with them. The abstract “0 – 4” means that the device can allow 5 simultaneous virtual connections which may be Telnet or SSH.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I enable Remote Access?
Right-click on "Computer" and select "Properties". Select "Remote Settings". Select the radio button for "Allow remote connections to this computer". The default for which users can connect to this computer (in addition to the Remote Access Server) is the computer owner or administrator.
How do I access a virtual machine from the outside network?
1 AnswerChange the VM networking from NAT to Bridged.Check that the guest still has Internet connectivity after rebooting or ipconfig /renew .Configure the router to give the guest a fixed IP address. ... Determine which ports and protocols needed to connect with the guest.More items...•
What is the difference between Vty 0 4 and Vty 5 15?
VTY lines are usually used for creating out-of-band management sessions to devices. If a password is not supplied on a vty line, that line cannot be used for managing the device. In some cases administrators may decide to let junior staff to use lines 0 - 4 and senior staff to use lines 5 - 15.
How many Vty lines are there?
The virtual terminal or “VTY” lines are virtual lines that allow connecting to the device using telnet or Secure Shell (SSH). Cisco devices can have up to 16 VTY lines.
What does Vty stand for?
Virtual TeletypeWhat Does Virtual Teletype (VTY) Mean? Virtual teletype (VTY) is a command line interface (CLI) created in a router and used to facilitate a connection to the daemon via Telnet, a network protocol used in local area networks. To connect to a VTY, users must present a valid password.
What is the difference between VPN and remote access?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is remote access VPN Cisco?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network such as the Internet. Remote access VPNs for IPsec IKEv2. 8.4(1) Added IPsec IKEv2 support for the AnyConnect Secure Mobility Client.
How can I access my home router from anywhere?
To connect to your personal router remotely, go to your web browser on your phone. Type in your router's IP address. It's the same IP address you used when you were setting up the remote access. A log-in page will be displayed.
How can I access my home network remotely?
Check out the Remote Desktop utility. It takes a little configuration to set up: You have to add users to a “remote desktop” group, forward a port through your router's firewall to your target system, grab the router's IP address, and connect to your local system using Remote Desktop on your remote PC.
Step1. Define the authentication and authorization methods used
In this case, we’re defining a new group called VPN which will use the local database for authenticating and authorizing the user.
Step 3. Define the VPN client group profile
We are going to name the group VPNGROUP. This is the group name that will be entered in the VPN client. Enter the preshared secret here, and a POOL name, which defines what IPs that will be handed out to the VPN clients. Then assign the name of the ACL that will be used to define the encrypted traffic that will be allowed through the VPN.
Step 4. Create a the address Pool and the access-list used for traffic encryption
Setup the IP ranged to be assigned to the address pool. In this case the starting IP is 10.100.3.1 and the last IP that can be assigned is 10.100.3.254
Step 7. Lastly, assign the crypto map to the internet interface
We were unable to load Disqus Recommendations. If you are a moderator please see our troubleshooting guide.
What is Cisco IOS?
Cisco IOS software-based networking devices provide several features that can be used to implement basic security for command-line sessions using only the operating system running on the device. These features include the following:
What is Cisco support and documentation?
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password.
How to increase security on network?
After you have protected access to user EXEC mode and privileged EXEC mode by configuring passwords for them you can further increase the level of security on your networking device by configuring usernames to limit access to CLI sessions to your networking device to specific users.
What command to use to configure password for privileged EXEC mode?
Cisco recommends that you use the enable secret command, instead of the enable password command to configure a password for privileged EXEC mode. The password created by the enable secret command is encrypted with the more secure MD5 algorithm.
What to do if you cannot establish a remote CLI session?
If you cannot establish a remote CLI session with the networking device, and you have saved the misconfigured local CLI session password to the startup configuration, or you have lost the local CLI session password, you must perform a password recovery procedure. Password recovery procedures are device specific. You must locate the document that describes the procedure for your type of networking device. See the "Technical Assistance" section for more Cisco support information for your networking device.
Can a network device be configured to use AAA?
Your networking device must not be configured to use any local or remote authentication, authorization, and accounting (AAA) security features. This document describes only the non-AAA security features that can be configured locally on the networking device.
Can you use the enable password command in Cisco?
Cisco no longer recommends that you use the enable password command to configure a password for privileged EXEC mode. The password that you enter with the enable password command is stored as plain text in the configuration file of the networking device. You can encrypt the password for the enable password command in the configuration file of the networking device using the service password-encryption command. However the encryption level used by the service password-encryption command can be decrypted using tools available on the Internet.
Problem
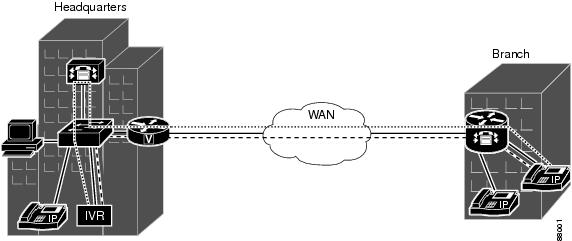
Having the ability to remotely administer network devices, means I don’t have to get my lazy carcass out of my chair and start fishing console cables out of my bag, also it saves on shoe leather, and travelling time.
Cisco Router – Restricting Telnet and SSH Access via Access List
You can lock down access further to remote management, by allowing or denying access from an ACL.
Schedule a Router Reload
1. From the top let’s create a user, and setup the RSA key, (skip this step if you have already done this).
How many steps are required to enable SSH on Cisco router?
There are four steps required to enable SSH support on a Cisco IOS router:
Why isn't the connect button enabled?
The Connect button is not enabled if you do not enter the host name and username. This screenshot shows that the login banner is displayed when Secure Shell connects to the router. Then, the login banner password prompt displays. The PuTTY client does not require the username to initiate the SSH connection to the router.
Can you test SSH for outbound reverse telnets?
If you need outbound SSH terminal-line authentication, you can configure and test SSH for outbound reverse Telnets through Carter , which acts as a comm server to Philly.
Configuration
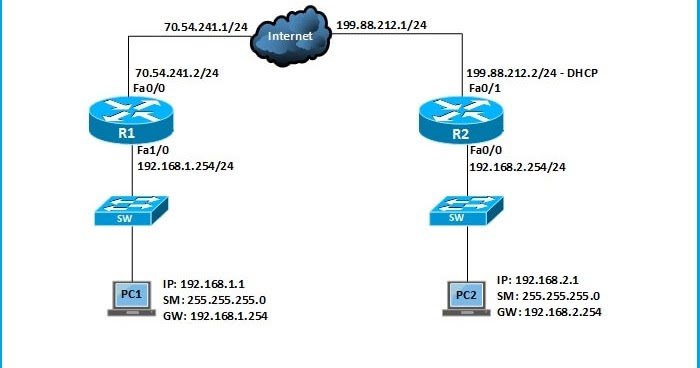
We will configure SSH on R1 so that we can access it from any other device. R2 will be used as a SSH client.
SSH Server
the name of the RSA keypair will be the hostname and domain name of the router. Let’s configure a hostname:
SSH Client
The most common SSH client is probably putty. The only thing you have to do is to select the SSH protocol, enter the IP address and leave the default port at 22: