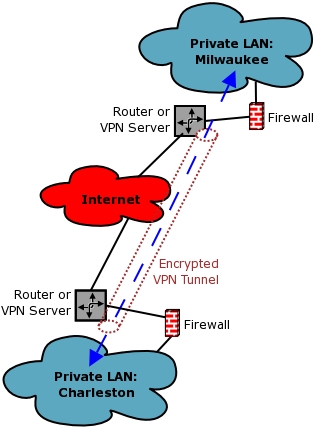
Some common remote access and virtual private network (VPN) tunneling protocols include:
- PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server,...
- IPsec. Internet Protocol security (IPsec) can be used as a remote access tunneling protocol to encrypt traffic going...
- PPTP. Point-to-Point Tunneling Protocol...
- PPTP. Point-to-Point Tunneling Protocol is one of the oldest VPN protocols in existence. ...
- L2TP/IPSec. Layer 2 Tunnel Protocol is a replacement of the PPTP VPN protocol. ...
- OpenVPN. ...
- SSTP. ...
- IKEv2.
What are the types of remote access protocols?
Remote Access Protocols. Some common remote access and virtual private network (VPN) tunneling protocols include: PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server, or between a dial-up client and an Internet Service Provider (ISP).
What are some examples of VPN tunneling protocols?
Some common remote access and virtual private network (VPN) tunneling protocols include: PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server, or between a dial-up client and an Internet Service Provider (ISP). IPsec.
What is a remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the secure VPN protocols?
Secure VPN protocols include the following: Internet Protocol Security ( IPsec) was initially developed by the Internet Engineering Task Force (IETF) for IPv6, which was required in all standards-compliant implementations of IPv6 before RFC 6434 made it only a recommendation.
What are VPN protocols?
A VPN protocol is a set of rules or instructions that will determine how your data routes between your computer (or other device) and the VPN server. VPN providers rely on protocols to ensure a stable and secure connection.
What are the 3 types of VPN?
VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What is remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What are 2 types of VPN?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
How many types of VPNs are there?
Virtual Private Network (VPN) is basically of 2 types: Remote Access VPN: Remote Access VPN permits a user to connect to a private network and access all its services and resources remotely. The connection between the user and the private network occurs through the Internet and the connection is secure and private.
Which type of VPN is best?
Many VPN experts recommend OpenVPN as the most secure protocol. It uses 256-bit encryption as a default but also offers other ciphers such as 3DES (triple data encryption standard), Blowfish, CAST-128, and AES (Advanced Encryption Standard).
What is VPN and its types?
VPN stands for Virtual Private Network (VPN), that allows a user to connect to a private network over the Internet securely and privately. VPN creates an encrypted connection that is called VPN tunnel, and all Internet traffic and communication is passed through this secure tunnel.
Which VPN is the best?
Get an in-depth look at the best VPNs of 2022ExpressVPN. The best VPN on the market. ... NordVPN. The big-name VPN is one of the very best. ... Surfshark. It's cheap, but performs like a premium product. ... Proton VPN. Privacy favorite keeps getting better. ... Private Internet Access. ... CyberGhost. ... Hotspot Shield. ... Hide.me.More items...•
What is the newest VPN protocol?
WireGuard. WireGuard is the newest VPN protocol on the block. Meant to be a replacement of IPSec, it is allegedly lighter and faster. Furthermore, it is open source, which means a reduced likelihood of security vulnerabilities.
What is site to site VPN?
Site-to-Site VPN. A site-to-site VPN, also referred to as router-to-router VPN, enables offices in multiple locations to safely connect with each other. Remote Access VPN. A remote access VPN allows a user to securely connect to a business or home network and access its resources from a remote location.
What port is OpenVPN on TCP?
SSTP VPN: Open port 1701 for both UDP/TCP. OpenVPN: Open port 53 for UDP and port 80 for TCP. L2TP VPN: Open port 1701 for both UDP/TCP.
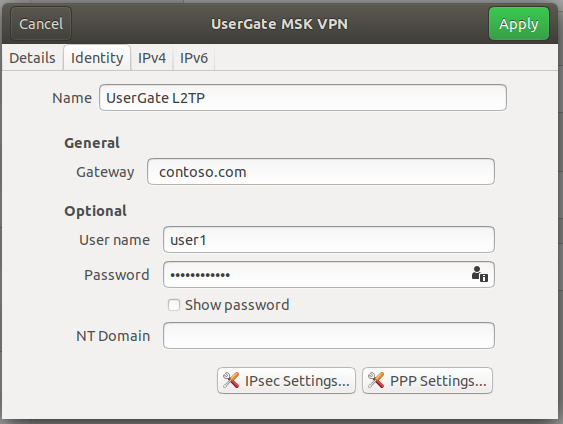
What is L2TP protocol?
L2TP – Layer 2 Tunneling Protocol. Since it does not provide strong authentication, L2TP is used with IPSec for security. Though it may conflict with some firewalls, it is a great alternative to the OpenVPN protocol because it supports all modern platforms, and can get around ISP/network limitations.
Why is VPN important?
VPN protocols are important. They provide safety and speed to your online communications. Whether your VPN is optimized for speed or security depends on the VPN protocol that you are currently using. These operate as tunnels through which your online traffic can pass through. Some tunnels are secure.
Which is the most secure VPN?
OpenVPN is the most secure VPN protocol. It offers the highest level of encryption and uses digital certificates for authentication. SSTP also comes with strong security, but it can only be used on Windows operating systems. Winner: OpenVPN.
Which is more secure, PPTP or OpenVPN?
If we talk about security, PPTP is far from secure. It is also the last VPN protocol you would want to use to stay safe online. IKEv2 and L2TP are more secure because they encapsulate your data twice. OpenVPN is the most secure VPN protocol.
What is a VPN Protocol?
A VPN protocol is the set of instructions/rules that outline how a connection should be made between your device and the VPN server. The protocol in some way determines the speed and may use encryption algorithms to help keep your data secure.
Commonly Used VPN Protocols
These are protocols most reputable VPN providers & best VPNs prefer to offer. They are very secure with fast speeds, stability, and they are not easily compromised.
Outdated VPN Protocols
These are protocols that most reputable VPN providers stopped offering due to their vulnerabilities. However, you can still get them on a majority of VPN providers.
Proprietary VPN Protocols
These are protocols that are owned and controlled by a given VPN provider. They are solely created and customized to be used within their VPN services.
Wrap Up
VPN protocols provide guidelines and specifications on how a VPN connection should be made. Depending on the protocol in use, a VPN connection can be faster, secure, or stable.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is VPN a security initiative?
Top VPN brands join security initiative. Ethics and VPN: the industry needs to aim higher. While VPNs have grown increasingly popular among users looking to protect their data and privacy online, using the right type of VPN can make all the difference when working remotely.
Is remote access VPN secure?
Since remote access VPNs are affordable and secure, organizations can feel more comfortable with letting their employees work from home or while traveling.
What is the protocol used to create a remote access server?
Some common remote access and virtual private network (VPN) tunneling protocols include: PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server, or between a dial-up client and an Internet Service Provider (ISP). IPsec.
What is VPN access?
A VPN allows a client to access a private network over a public network (such as the Internet). Remote access methods are useful for personnel that need access to the private network from remote locations.
What are the different authentication mechanisms?
The different authentication mechanisms that may be used with remote access services are: 1 PAP. Password Authentication Protocol. Passwords are sent in clear text so PAP is rarely used today. 2 CHAP. Challenge Handshake Authentication Protocol. CHAP uses a handshake process where the server challenges the client. The client then responds with appropriate authentication information. 3 MS-CHAP. Microsoft’s implementation of CHAP, which is used only by Microsoft clients. 4 MS-CHAPv2. An improvement over MS-CHAP. A significant improvement of MS-CHAPv2 over MS-CHAP is the ability to perform mutual authentication. 5 RADIUS. Remote Authentication Dial-In User Service. Radius provides a centralized method of authentication for multiple remote access services servers. RADIUS encrypts the password packets, but not the entire authentication process. 6 TACACS and XTACACS. Terminal Access Controller Access-Control System (TACACS) is a remote authentication protocol that was commonly used in UNIX networks. Extended TACACS (XTACACS) is an improvement over TACACS developed by Cisco Systems and is proprietary to Cisco systems. Neither of these are commonly used today with most organizations using either RADIUS or TACACS+. 7 TACACS+. Terminal Access Controller Access-Control System+ (TACACS) is an alternative to RADIUS and is proprietary to Cisco systems. A benefit of TACACS+ is that it can interact with Kerberos allowing it to work with a broader range of environments including Microsoft. Additionally, TACACS+ encrypts the entire authentication process (RADIUS encrypts only the password).
What port does Cisco VPN use?
TACACS+ has wider uses including as an authentication service for network devices. TACACS+ uses TCP port 49 .
What is L2TP tunneling?
Layer 2 Tunneling Protocol combines the strengths of Layer 2 Forwarding (L2F) and PPTP. L2TP is commonly used with IPsec for VPNs. Since NAT is not compatible with IPsec, L2TP/IPsec can’t go through a device running NAT. L2TP uses UDP port 1701. RADIUS.
What port does PPTP use?
PPTP. Point-to-Point Tunneling Protocol is a tunneling protocol used with VPNs that has some known vulnerabilities. PPTP uses TCP port 17 23. L2TP. Layer 2 Tunneling Protocol combines the strengths of Layer 2 Forwarding (L2F) and PPTP.
What is RAS in network?
Remote Access Services (RAS) are used to provide access to an internal network from an outside source . The previous section covered some of the protocols used for remote access connections, but this section covers different authentication mechanisms that can be used with RAS.
1. OpenVPN
While scouring the selection of different types of VPN protocols, you’ll stumble upon OpenVPN right away. Touted as the most popular protocol among VPN providers and users, this option is highly secure and works on multiple platforms, including Windows, macOS, Linux, Android, and iOS.
3. SSTP
Owned and controlled by Microsoft, The Secure Socket Tunneling Protocol is fully integrated with all Microsoft operating systems, going back to Windows Vista SP1. On the flip side, that means there is no access to the underlying code, as it’s not an open-source protocol.
4. IKEv2 VPN Protocol
Internet key exchange version 2 or IKEv2 is a tunneling protocol developed by Microsoft and Cisco that uses a secure key exchange. Similar to L2TP, it needs to be paired with IPSec for authentication and encryption.
5. PPTP
Although somewhat obsolete and typically not ranked among the three main VPN tunneling protocols, Point-to-Point Tunneling Protocol is still being used. Developed in 1985 by Microsoft for dial-up connections and integrated into Windows 95, it’s one of the oldest protocols, lacking some of the newer security features.
6. WireGuard
WireGuard is a state-of-the-art VPN protocol that uses a much simpler and smaller codebase and is easier to set up than most of its counterparts. In addition, WireGuard uses one of the newest encryption algorithms, ChaCha20, that offers faster speeds with fewer resources, allowing your battery to last longer.
What is VPN system?
VPN systems also may be classified by: the tunneling protocol used to tunnel the traffic. the tunnel's termination point location, e.g., on the customer edge or network-provider edge. the type of topology of connections, such as site-to-site or network-to-network. the levels of security provided.
What is VPN security?
The VPN security model provides: confidentiality such that even if the network traffic is sniffed at the packet level (see network sniffer and deep packet inspection ), an attacker would see only encrypted data. sender authentication to prevent unauthorized users from accessing the VPN.
How does a VPN work?
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN). From a user perspective, the resources available within the private network can be ...
What is VPN in computing?
A virtual private network ( VPN) extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across a VPN may therefore benefit from the functionality, security, ...
Why use VPN for applications?
Applications running across a VPN may therefore benefit from the functionality, security, and management of the private network. It provides access to resources that may be inaccessible on the public network, and is typically used for telecommuting workers. Encryption is a common, although not an inherent, part of a VPN connection.
What are the security features of VPN?
The VPN security model provides: 1 confidentiality such that even if the network traffic is sniffed at the packet level (see network sniffer and deep packet inspection ), an attacker would see only encrypted data 2 sender authentication to prevent unauthorized users from accessing the VPN 3 message integrity to detect any instances of tampering with transmitted messages.
What is PPVPN device?
A device at the edge of the customer's network which provides access to the PPVPN. Sometimes it is just a demarcation point between provider and customer responsibility. Other providers allow customers to configure it.
Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll ha...
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…