Why you should not use telnet?
Telnet is inherently insecure. Credential information (usernames and passwords) submitted through telnet is not encrypted and is therefore vulnerable to identity theft. However, users can establish an Secure Shell connection instead to prevent this type of intrusion.
Why telnet should not be used for remote server monitoring?
Telnet Is Insecure If you're using Telnet, someone can easily intercept the connection and will be able to see any credentials you send using a "man-in-the-middle attack." This is an example of the different cultures that Arpanet, the original network that became the internet, was developed under.
Why do you think Telnet is not a safe way to connect to a remote machine what is the safer way to do so?
Telnet is not a secure protocol and is unencrypted. By monitoring a user's connection, anyone can access a person's username, password and other private information that is typed over the Telnet session in plaintext. With this information, access can be gained to the user's device.
What replaced Telnet?
In the early years of computing, telnet was used to connect to the command line on remote systems. SSH has replaced telnet for remote access needs, and these days when you hear about telnet , it is usually when somebody is using the client as a generic network troubleshooting tool.
Is Telnet a vulnerability?
Vulnerabilities in Telnet Detection is a Low risk vulnerability that is one of the most frequently found on networks around the world. This issue has been around since at least 1990 but has proven either difficult to detect, difficult to resolve or prone to being overlooked entirely.
Why is Telnet still being used?
Telnet is still the natural connectivity tool for RF Terminals, Bar Code scanners, and other data collection devices. The type of data transferred between a telnet client and server is simple text and mall graphics, making the protocol nimble, lightweight, fast and reliable.
What is difference between SSH1 and SSH2?
The difference between SSH1 and SSH2 is they are two entirely different protocols. SSH1 and SSH2 encrypt at different parts of the packets, and SSH1 uses server and host keys to authenticate systems where SSH2 only uses host keys.
What is the difference between Telnet and SSH?
Telnet transfers the data in simple plain text. On other hand SSH uses Encrypted format to send data and also uses a secure channel. No authentication or privileges are provided for user's authentication. As SSH is more secure so it uses public key encryption for authentication.
How to enable telnet?
Option 1: Enable Telnet using GUI. To activate the Telnet command using the GUI: 1. Open the Programs and Features options in Control Panel: 2. Click the Turn Windows features on or off setting: 3. Locate the Telnet Client option on the list, select it and click OK to install the feature: 4.
How to check if telnet is activated?
To check if Telnet is already activated, open your command line, and run telnet: If the command prompt does not recognize the command, there are two possible ways to enable the Telnet client in Windows.
What is telnet protocol?
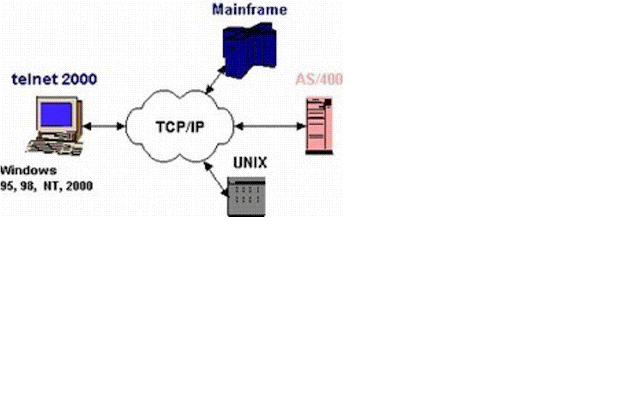
Telnet is a client-server protocol predating the TCP protocol. The network protocol allows a user to log into another computer within the same network through a TCP/IP connection. A client machine running the Telnet client connects to a CLI on a remote device, most commonly a dedicated platform.
Why is telnet vulnerable to cyber attacks?
Telnet is vulnerable to cybersecurity attacks because it lacks encryption methods compared to the more modern SSH. However, it is still helpful for tasks that do not involve transmitting sensitive information. This article teaches you what Telnet is as well as how to use Telnet on Windows to test for open ports. Prerequisites.
Is telnet secure?
The Telnet communication protocol provides a way to establish a direct connection with a remote host. Although not a secure option for most tasks, there are use cases where Telnet is a viable option. For further reading, check out the more secure option and learn how to use SSH to connect to a remote server in Linux or Windows.
What is telnet connection?
Since Telnet connections are practically standard TCP connections, the client can be employed to use or test other services that rely on TCP as a transport protocol. For example, with a simple request, you can check the functionality of an HTTP server or (as mentioned earlier) the status of an e-mail server.
What is telnet protocol?
Telnet is a client-server protocol based on character-oriented data exchange over TCP connections. Telnet enables remote control of computers via text-based inputs and outputs. For this reason, a client-server connection is established as a default via the TCP protocol and port 23, where the remote-controlled device acts as a server ...
When was telnet developed?
This protocol can also be used to manage applications that do not have a graphical interface. As early as 1969 (during the nine months of work on ARPANET ), the development of Telnet (Teletype Network) was practically completed.
Is telnet disabled in Windows 8?
Telnet is also disabled by default on Windows 8. Attempting to access the client or establish a connection will result in you receiving the same error message as Windows 7 users receive, stating that the Telnet command is either misspelled or cannot be found.
Is telnet a server?
Administration of networks and servers. Telnet has always been a practical protocol for network and server administrators. The ability to remotely manage devices on the network is ideal for administration tasks, especially because the protocol is supported by almost all devices.
Is Telnet safe for remote connections?
However, Telnet is still a suitable solution for devices with limited operating systems that do not enable SSH server operation.
What was the original network that became the internet?
This is an example of the different cultures that Arpanet, the original network that became the internet, was developed under. As a US government research project in the late 1960s and early 1970s, Arpanet was experimental and had no ambitions to become the massive global network that the modern internet is today.
Can you use telnet instead of ssh?
But you shouldn't, because it's not safe for your digital privacy.
Is telnet secure?
The main problem with Telnet is that it isn't secure. All of the text sent between computers using Telnet is in plain text. This includes usernames and passwords as well . If you're using Telnet, someone can easily intercept the connection and will be able to see any credentials you send using a " man-in-the-middle attack ."
Is SSH a Telnet?
Even as useful as SSH is, like Telnet, the main technical assumptions of its development meant that the later network deploy ments expose its deficiencies . SSH assumes the use of wired, always-on connections. Try closing your laptop lid when you're connected and see what happens. Your SSH connection will freeze.
Can you use SSH and Mosh?
With SSH and Mosh, you can ditch Telnet entirely, keeping your login information safe while you access remote computers. To ensure your privacy online, you should be aware of the limitations of every technology or software that you use. Even SSH isn't an exception.
Enable Cisco Telnet
Would you like to learn how to enable Cisco Telnet remote access using the command-line? In this tutorial, we are going to show you all the steps required to configure the Telnet remote access on a Cisco Switch 2960 or 3750 using the command-line.
Cisco Switch Playlist
On this page, we offer quick access to a list of videos related to Cisco Switch.
Telnet on Windows 10
Telnet isn’t obsolete. It still works but not a lot of people use it. There are GUI clients that use Telnet, and that make it infinitely easier to use but despite that, you will find there are better remote access solutions available. That said, you can still enable and use Telnet on Windows 10.
Confirm Telnet installation
To check if Telnet is installed on your system, or to confirm that the installation was successful, follow these steps.
How to use Telnet on Windows 10
The Telnet client is a command line tool. It won’t install as a GUI app and you will use it via Command Prompt. You must be familiar with commands for connecting to a remote system. Open Command Prompt with admin rights.
Why is telnet important?
The biggest benefit of enabling Telnet or SSH protocol is that there is no need to make a console connection to the router. This way, you can easily access and manage the router over the local network via telnet. Follow the steps below to configure Telnet on the router.
How to configure telnet on Cisco router?
Step 1. After adding a Cisco Router, Switch, and PC on the Packet Tracer workspace, cabling all devices. Step 2. Double-click Cisco Router1 to open the CLI prompt and type No to skip the initial configuration and press Enter. Step 3.
What is the disadvantage of telnet?
The only disadvantage of Telnet is security. It sends data over the network without encrypting it, allowing spies to access data such as user names and passwords.