
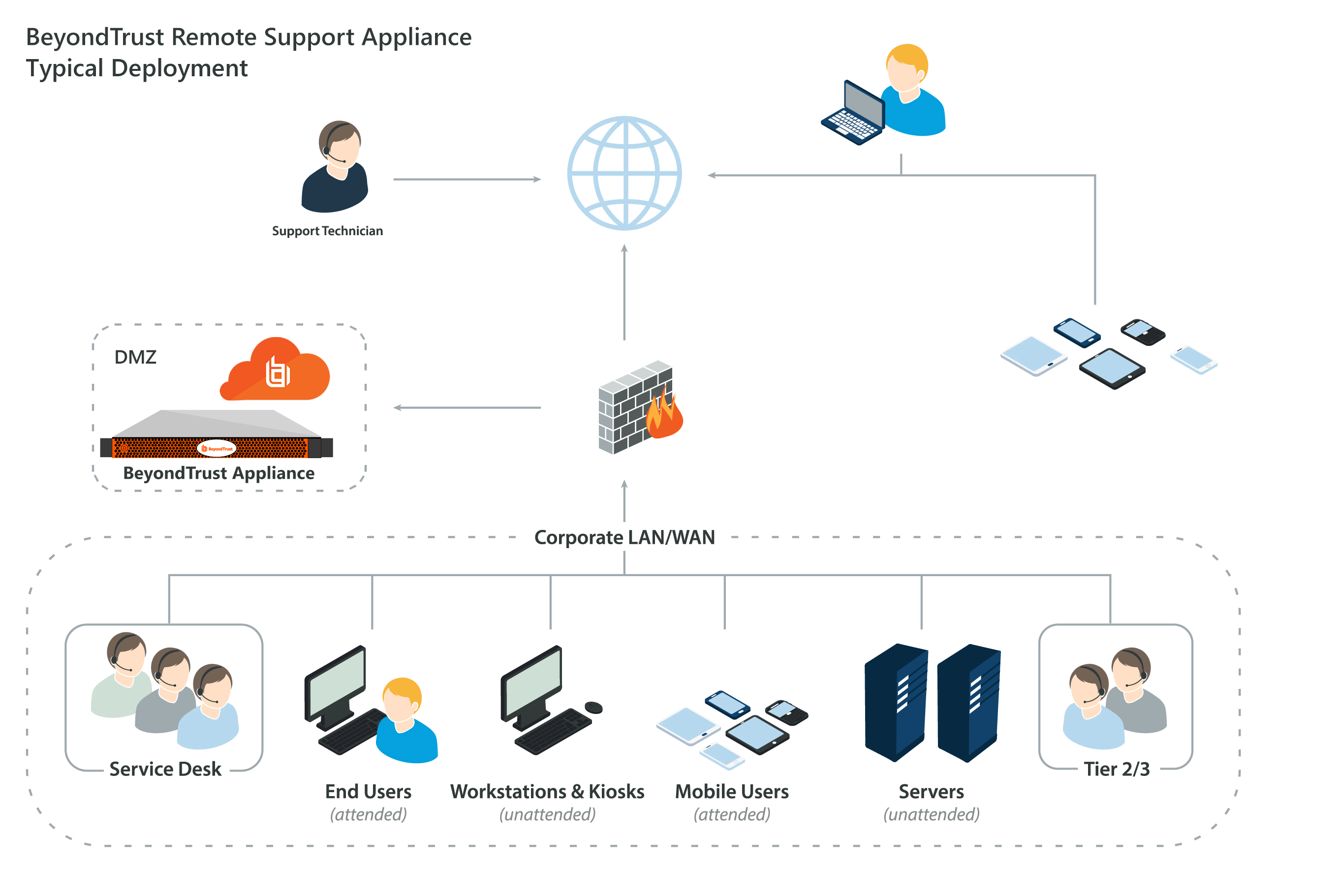
The Secure Remote Access Appliance in the Network. The architecture of the BeyondTrust application environment relies on the Secure Remote Access Appliance as a centralized routing point for all communications between application components. All BeyondTrust sessions between users and remote systems occur through the server components that run on the appliance.
Full Answer
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.
How to remote access a DVR?
There are a few basic things you will need in order to get started.
- Live Internet Connection. This can come from any internet service provider in your area. ...
- Router. A Router is a device which forwards the data between your network connections. ...
- Ethernet Cables. These are usually sold as CAT5 (Category 5) cables which are used to connect you to the internet. ...
- DVR with the ability to be remotely viewed. ...
- Monitor. ...
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
How do I secure a remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What is a secure remote access protocol?
Like VPNs, remote access software uses solid encryption methods to protect you from threats outside of your network's walls and protection. It also uses multi-factor authentication to ensure that all access made on your network or device is authorized.
What is B Series appliance?
The BeyondTrust B Series Appliance helps support and security professionals improve productivity and security by enabling secure, controlled connections to any system or device. It enables the use of remote support in multiple areas of an organization in a way that is secure, integrated and manageable.
What allows for secure remote console access?
You can enable remote access (dial-up or VPN), Network Address Translation (NAT), both VPN and NAT, a secure connection between two private networks (site-to-site VPN), or you can do a custom configuration to select any combination of these, as shown in Figure 14.25.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Why is RDP insecure?
RDP itself is not a secure setup and therefore requires additional security measures to keep workstations and servers protected. Without proper security protocols in place, organizations face several potential risks, including the increased risk of cyberattacks.
What is BeyondTrust app?
BeyondTrust is the first remote support software vendor to enable secure remote control from mobile devices. BeyondTrust's mobile representative consoles for iOS and Android devices increase efficiency by allowing support technicians to stay productive while mobile, delivering remote support anytime and from any place.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
What are the secure methods the remote users can use to connect to the internal network to perform file operations?
VPNs are the most common form of remote access. They use authentication and encryption to establish a secure connection to a private network over the internet.
Which of the following describes the best way to make sure you are securely accessing the company network remotely?
You should use WPA2 or WPA3 encryption when remotely connecting to a network. WPA2 or WPA3 encryption are the encryption standards that will protect information sent over a wireless network.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
Can IoT services be hosted on premises?
IoT services that are hosted on-premises can benefit from optimized speeds. Performance speeds can increase if local users do not have to connect out to the internet to access apps that are hosted on-premises. The other option is ZTNA as a service, such as Zscaler Private Access.
Is Zscaler a cloud service?
The other option is ZTNA as a service, such as Zscaler Private Access. This is a cloud-hosted service, where customers leverage a vendor’s cloud infrastructure for policy enforcement. The enterprise simply purchases user licenses and deploys lightweight connectors that front-end applications in all environments; the vendor delivers the connectivity, capacity, and infrastructure needs. Access is established through brokered inside-out connections between user and application, effectively decoupling application access from network access while never exposing IPs to the internet.
What is Claroty SRA?
Claroty SRA provides a host of capabilities that enable secure, seamless connectivity to OT environments while retaining strict control over remote sessions.
What is an intuitive interface?
An intuitive interface that mirrors a user’s on-premises technology experience provides unmatched usability with no learning curve or need for extensive training.
Does Claroty need contact information?
Claroty needs the contact information you provide to us to contact you about our products and services. You may un subscribe from these communications at any time . For information on how to unsubscribe, as well as our privacy practices and commitment to protecting your privacy, please review our Privacy Policy.
Secure Remote Support with the BeyondTrust Box
With the BeyondTrust Appliance for remote support, every support session generates a detailed audit trail, including a full video recording of all remote support activity. By investing in the BeyondTrust Appliance, you eliminate the monthly fees of software-as-a-service, lowering total cost of ownership over time.
Secure Remote Support. No Monthly Fees
BeyondTrust offers the leading ownership model for remote support. Customers buy BeyondTrust once, then get support and upgrades for a yearly maintenance fee. Eliminating the monthly fees required by Software-as-a-Service enables a lower total cost of ownership.
How Does the BeyondTrust Appliance Work?
Firewalls are designed to block incoming traffic. That is why traditional remote desktop tools (RDP, VNC, pcAnywhere, Dameware and others) require firewall configuration changes in order to work over the internet.
Why use Sonicwall SMA?
“My organization uses SonicWall SMA to allow employees remote access to their corporate workstations from anywhere at any time. During the COVID-19 restrictions, this proved invaluable to our organization, as we were able to scale up the number of remote users very quickly and cost-effectively.”
What is SMA 100?
Best for small and medium businesses (50-100 employees), SMA 100 series deploys secure remote access solutions that enable policy-enforced access control to any user or device, anywhere. It can be deployed across on-prem, virtual and public cloud datacenters.
Avaya SAL & Government Solutions
Specifically for Avaya and heritage Nortel customers and partners, APITech offers a special line of products that addresses remote management, secure access, and modem challenges.
ION Secure Appliance 2.0
New version of ION Secure Appliances now supports a new Web Server to simplify system administration and user connectivity.
