What are the different protocols used in VPN?
Protocols used in VPN PPTP - Point-to-point tunneling protocol L2Tp – Layers to Tunneling Protocol IPSec - Internet protocol security SSL – is not used as much as the ones above. Encryption 9.
How does a remote access client work?
A remote client uses the telecommunication infrastructure to create a temporary physical or virtual circuit to a port on the RAS. After the circuit is created, the connection parameters are set. If RAS and remote access clients are not located in a local telecommunication boundary, incremental long distance charges are incurred.
What are the different authentication protocols used for remote authentication?
Challenge Handshake Authentication Protocol (CHAP)<br />3. Microsoft CHAP (MS-CHAP) or MD5<br />4. Remote Authentication Dial-In User Service (RADIUS)<br />5. Extensible Authentication Protocol (EAP)<br /> 30.
What is a VPN PPT?
Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicate.
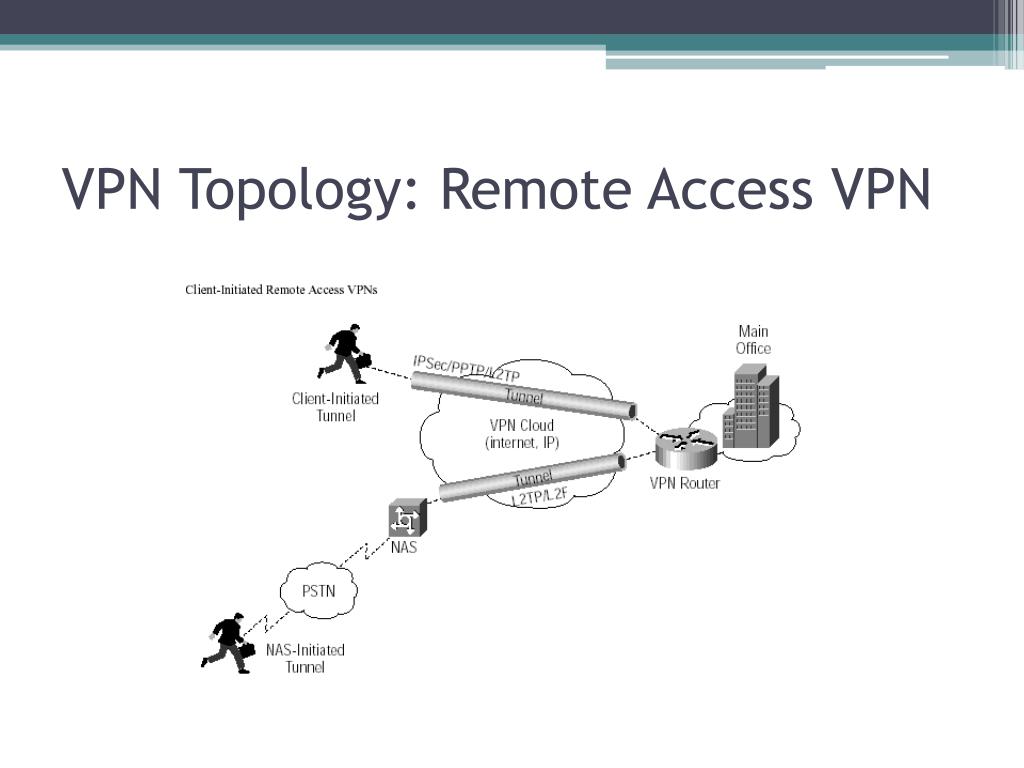
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What are the benefits of VPN?
Pros of VPN: What are the advantages of using a VPN?Secure Your Network. The benefits of using a VPN are vast. ... Hide Your Private Information. ... Prevent Data Throttling. ... Avoid Bandwidth Throttling. ... Get Access to Geo-blocked Services. ... Network Scalability. ... Reduce Support Costs.
What is VPN PDF?
A virtual private network (VPN) can be defined as a way to provide secure communication between members of a group through use of public telecommunication infrastructure, maintaining privacy through the use of a tunneling protocol and security procedures.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What are the advantages and disadvantages of VPN?
While not always ideal, the use of a VPN is often the most affordable and secure way to protect oneself online. VPN Disadvantages. Specific activities that require high bandwidth, such as gaming, might not be able to function using a VPN, but they are easily enabled and disabled.
What are four types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs....How Personal VPNs WorkInstall software from your VPN service provider onto your device. ... Connect to a server in your VPN provider's network.More items...•
Does VPN improve security?
Using a reliable virtual private network (VPN) can be a safe way to browse the internet. VPN security can protect from IP and encrypt internet history and is increasingly being used to prevent snooping on by government agencies.
What's a VPN connection?
A VPN, or Virtual Private Network, routes all of your internet activity through a secure, encrypted connection, which prevents others from seeing what you're doing online and from where you're doing it. Basically, a VPN provides an extra layer of security and privacy for all of your online activities.
How is VPN established?
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN).
What is VPN architecture?
VPN uses authentication methods, encryption algorithms, and other precautions to ensure that data sent between the two endpoints of its connection remains secure. VPN runs on the network layer of the TCP/IP layered communications stack model. Specifically, VPN uses the IP Security Architecture (IPSec) open framework.
How do I access a VPN server remotely?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
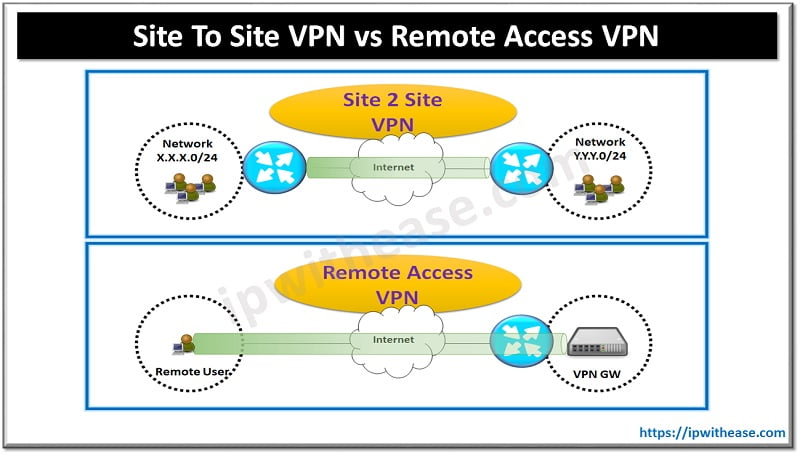
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Does VPN allow you to access a computer remotely?
In order to fully secure a remote desktop, a VPN is the best option. With a VPN like Access Server, you have secure access to the network, and then the VPN server has least a privilege access policy setup that would limit an employee to using a remote desktop to connect only to his or her computer's IP address.
Can you be tracked if you use VPN?
However, if you use a poor quality VPN, you could still be tracked. A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish.
What is VPN security?
VPN Security: Firewall A well-designed VPN uses several methods for keeping your connection and data secure: Firewalls Encryption IPSec AAA Server You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through. 10.
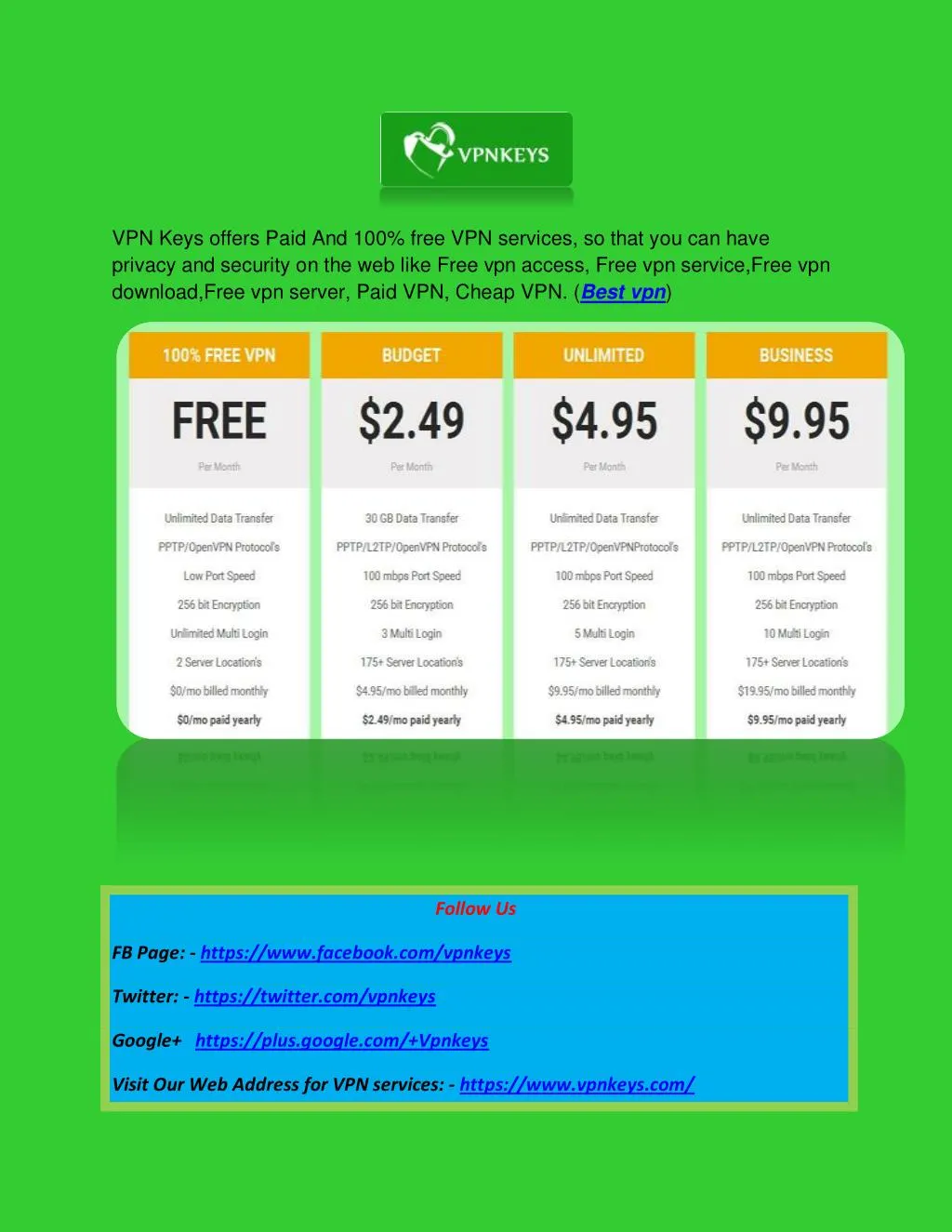
What is a VPN?
Virtual Private Network is a type of private network that uses public telecommunicaton, such as the Internet, instead of leased lines to communicate. Read more.
What is VPN network?
What is VPN Virtual Private Network is a type of private network that uses public telecommunication, such as the Internet, instead of leased lines to communicate. Became popular as more employees worked in remote locations. Terminologies to understand how VPNs work. 4. Types of VPN’s Remote-Access VPN Site-to-Site VPN (Intranet-based) ...
What are the advantages of VPN?
11. VPN Advantages Multiple telephone lines and banks of modems at the central site are not required. A reduction in the overall telecommunication infrastructure – as the ISP provides the bulk of the network. Reduced cost of management, maintenance of equipment and technical support. Simplifies network topology by eliminating modem pools and a private network infrastructure. VPN functionality is already present in some IT equipment.
Is VPN good for corporate networking?
16. Conclusion As we have gone through all possible details we conclude that VPN is the best option for the corporate networking. As many companies need to have access to Internet and hence security is also the main concern. VPN provides best possible combination of security and private network capabilities with adequate cost – saving to the companies who are presently working with leased lines.
What is remote access VPN?
the Remote Access VPN Design Guidesupports the remote user with secure remote access (RA). this guide covers the deployment of RA VPN services to either the primary internet edge firewall or to a standalone RA VPN-specific device.
How to create a VPN admin?
Step 1: in Policy Elements > Authorization and Permissions > Network Access > Authorization Profiles, click Create. Step 2: in the Name box, enter a name for the authorization profile. (example: VPN-Administrator) Step 3: click the RADIUS Attributes tab, and then in the RAdius Attribute row click Select.
What is a AAA server?
As networks scale in the number of devices to maintain, it poses an operational burden to maintain local user accounts on every device. A centralized authentication, authorization, and accounting (AAA) service reduces operational tasks per device and provides an audit log of user access for security compliance and root cause analysis. When AAA is enabled for access control, all management access to the network infrastructure devices (ssh and httPs) is controlled by AAA. the AAA server used in this architecture is the cisco secure Acs. configuration of cisco secure Acs is discussed in the device Management using Acs design guide.
Does Cisco Asa firewall have a prompt?
user authorization on the cisco AsA firewall does not automatically present the user with the enable prompt if they have a privilege level of 15, unlike cisco ios devices.
What is VPN in PPT?
Virtual%20Private%20Network- Virtual Private Network VPN In the most basic definition, VPN is a connection which allows 2 computers or networks to communicate with each other across a public network. | PowerPoint PPT presentation | free to view
What is the growth rate of VPN?
Virtual Private Network (VPN) Market to set Phenomenal Growth- The VPN service segment is witnessing a growth rate of over 11% in the market from 2020 to 2026. The growing need to manage multiservice traffic and provide flexible connectivity & portability across corporate sites will support the segment growth. VPN services alert enterprise administration when vulnerabilities are detected, ensuring secure end-to-end connectivity across the network infrastructure.| PowerPoint PPT presentation | free to view
What is the best way to bypass firewalls?
VPN Is the Best Solution to Bypass Proxies and Firewalls- It is often noticed that every week there’s significant news about encryption, leaked information, snooping, or other computerized protection concerns. A large number of these articles talk about the significance of augmenting the security of your Internet Link, such as utilizing a VPN (Virtual Private Network) when you’re on open café Wi-Fi, however, they’re frequently light on the subtleties.| PowerPoint PPT presentation | free to view
What is PowerShow.com?
PowerShow.com is a leading presentation/slideshow sharing website. Whether your application is business, how-to, education, medicine, school, church, sales, marketing, online training or just for fun, PowerShow.com is a great resource. And, best of all, most of its cool features are free and easy to use.
Is Shazam a VPN?
virtual private network free- Welcome to VPN Shazam, Get the best free VPN package for android and pc. We offer a simple and easy-to-use free VPN (Virtual Private Network) that lets you enjoy fast and stable connections anywhere.| PowerPoint PPT presentation | free to view