What is remote access to computer?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
What is remote access (Rad)?
- Definition from Techopedia What Does Remote Access Mean? What Does Remote Access Mean? Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location.
What is secure remote access?
- Definition | VMware Glossary Secure remote access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization’s digital assets Skip to Main Content
What are the different ways to perform remote access?
Another method for performing remote access is by establishing a VPN, a network that usually uses the Internet to connect remote sites and users together. This type of network uses encryption and tunneling to access a company's network.
What is an access system?
What is remote access?
About this website
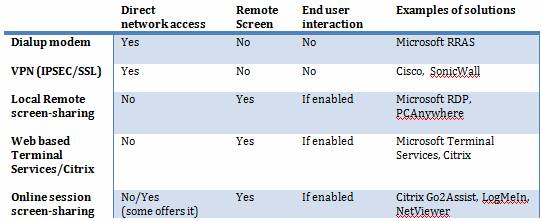
What's the meaning of remote access?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
What is remote access example?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
How do you take remote access?
How to use Remote DesktopMake sure you have Windows 11 Pro. To check this, select Start , and open Settings . ... When you're ready, select Start , and open Settings . Then, under System , select Remote Desktop, set Remote Desktop to On, and then select Confirm.Make note of the name of this PC under PC name.
Who uses remote access?
Technical support professionals can use remote access to connect to users' computers from remote locations to help them resolve issues with their systems or software. One common method of providing remote access is via a remote access virtual private network (VPN) connection.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
Can someone remotely access my computer?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
Can someone remotely access my computer when it's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
How do I set up remote access to my computer?
How to enable Remote DesktopOn the device you want to connect to, select Start and then click the Settings icon on the left.Select the System group followed by the Remote Desktop item.Use the slider to enable Remote Desktop.It is also recommended to keep the PC awake and discoverable to facilitate connections.More items...•
How can I remotely access another phone?
When you (or your customer) run the SOS app on the Android device it will display a session code that you will enter on your screen to remotely view that device. Users with devices running Android 8 or higher will be prompted to turn on accessibility in Android to allow remote access.
How do I control another computer remotely?
How Can I Remotely Access Another Computer For Free?the Start Window.Type in and enter remote settings into the Cortana search box.Select Allow Remote PC access to your computer.Click the Remote tab on the System Properties window.Click Allow remote desktop connection Manager to this computer.More items...•
How do I enable remote access to my server?
Windows 10: Allow Access to Use Remote DesktopClick the Start menu from your desktop, and then click Control Panel.Click System and Security once the Control Panel opens.Click Allow remote access, located under the System tab.Click Select Users, located in the Remote Desktop section of the Remote tab.More items...•
How can I remotely access my computer for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
Presentation - Security Concerns with Remote Access
Remote Access Security General remote access security SP 800-46, Security for Telecommuting and Broadband Communications Use virtual private networks
NIST SP 800-46 | NIST
Resource. Guideline/Tool. Details. Resource Identifier: NIST SP 800-46 Guidance/Tool Name: NIST SP 800-46, Revision 2, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security Relevant Core Classification: Specific Subcategory: PR.AC-P3 Contributor: National Institute of Standards and Technology (NIST) Contributor GitHub Username: @kboeckl
Security for Enterprise Telework, Remote Access, and Bring Your Own ...
Today, many people are teleworking (also known as telecommuting), which is the ability of an organization's employees, contractors, business partners, vendors, and other users to perform work from locations other than the organization's facilities. Teleworkers use various client devices, such as desktop and laptop computers, smartphones, and tablets, to read and send email, access websites ...
Security for Enterprise Telework, Remote Access, and Bring Your Own ...
Abstract Today, many people are teleworking (also known as telecommuting), which is the ability of an organization's employees, contractors, business partners, vendors, and other users to perform work from locations other than the organization's facilities.
What is an access system?
Access by users (or information systems) communicating external to an information system security perimeter. Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network.
What is remote access?
Definition (s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Source (s):
What Does Remote Access Mean?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
Techopedia Explains Remote Access
Remote access can be established via a line that runs between a computer and a company's local area network (LAN). A connection can also be established between a company's LAN and a remote LAN using a dedicated line. This type of line provides faster speeds but has the drawback of being more expensive.
What is RDP software?
RDP is a program by Microsoft that provides a user with a graphical interface to connect with another computer via a network connection. The user utilizes the RDP client software while the other person’s computer runs the RDP software.
What are the best practices for remote access?
Some best practices include endpoint protection, complex passwords, multi-factor authentication, updating your software, and limiting the number of users who can use the service.
Why is it important to remember that your computer will be exposed to at least one other user?
When engaging in remote access, regardless of the protocol, it is important to remember that your computer will be exposed to at least one other user. Because files can be transferred from one computer to another, the possibilities for the transfer of malware exist, as well as unacceptable access by an intruder.
What is a VNC?
Virtual network computing (VNC) Remote Desktop Protocol (RDP) Some remote access methods involve limited access or sharing of resources, but VPNs, VNCs, and RDPs allow users to both gain access to and have full control over another person’s computer via a remote network.
What is VPN access?
A VPN provides users with the ability to send and receive data between devices or via a private network that is extended over a public network. To gain access to another’s computer, both have to be connected to the same VPN and running the same access software.
What is remote access protocol?
Once both are connected to the remote access network, a protocol governed by access software interfaces that user's device with another user's device. The protocol gives one device the ability to access the functions of the target computer or server. This allows the keyboard, trackpad, touchscreen, ...
Why do we need remote access?
Remote computer access is often used to enable people to access important files and software on another user’s computer. With remote access, a user can monitor, maintain, and control devices as long as they are connected to the same network. This opens up the possibility to troubleshoot issues without being in the same physical location as ...
How does TeamViewer work?
Here’s how it works. You’ll need to create an account, and then download and install TeamViewer software onto both your home computer and your remote computer or device. TeamViewer can be installed on Windows, Mac OS, Linux, and Chrome OS. It also has apps for Windows Phone, Blackberry, iOS, and Android. LogMeIn.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
Is Firefox a trademark?
Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.
Can hackers use RDP?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
Is there a third party remote access program?
For instance, there are Windows-only and Mac-only programs if your computers and devices all use the same operating system.
How does secure remote access work?
Enabling remote access means walking a tightrope between usability and cybersecurity. Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What are the options for secure remote access?
Multiple solutions go into a comprehensive secure remote access package—and each one delivers vital functionality that reflects the way companies use their networks today. These features work together to protect users, data, and network assets in a distinct way.
Next-gen remote access solutions for a secure digital workspace
Learn how remote access solutions can secure digital workspaces and enhance the user experience.
Citrix solutions for secure remote access
Citrix secure access solutions take several forms to give companies a balanced selection of options based on their specific requirements. Whatever level of engagement with remote work these businesses have, there is a secure remote access solution for the situation.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
Redefining secure remote access with zero trust network access
In response to today’s needs, IT teams leverage zero trust network access (ZTNA) as a new framework for enabling secure remote access to off-network users. ZTNA is a term defined by Gartner, and the technology is also known as a software-defined perimeter (SDP).
Why a ZTNA approach to secure remote access is more effective than VPN
When it comes to secure remote access, digital transformation has changed everything. As noted above, VPNs are no longer adequate for keeping up with today’s advanced threats and the volume of users connecting to private applications off-network.
What is an access system?
Access by users (or information systems) communicating external to an information system security perimeter. Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network.
What is remote access?
Definition (s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Source (s):
