RADIUS (Remote Authentication Dial-In User Service) is a client-server protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
What is radius and how does it work?
Essentially, RADIUS allows remote access servers to communicate with the central server to authenticate and authorize remote user access. With RADIUS, companies can store user profiles in a central database that can be shared across all remote servers.
Can I use my radius to authenticate remote users?
RADIUS Authentication With VPN for Secure Remote Access The solution to potential security lapses of VPN is simple – use your RADIUS for VPN authentication. Yes, you can use your organization’s RADIUS to authenticate remote users.
What are the different types of radius clients?
RADIUS clients are network access servers, such as wireless access points, virtual private network (VPN) servers, 802.1X-capable switches, and dial-up servers. RADIUS proxies, which forward connection request messages to RADIUS
What are the benefits of radius and VPN for remote access?
The benefits of using your RADIUS in conjunction with VPN for remote access are twofold: It’s more secure. After the VPN connects to your office access point, the users undergo RADIUS authentication for network and resource access. Doubling up on protection keeps your traffic safe at all stages of the process.

What is the difference between VPN and RADIUS?
The benefits of using your RADIUS in conjunction with VPN for remote access are twofold: It's more secure. After the VPN connects to your office access point, the users undergo RADIUS authentication for network and resource access. Doubling up on protection keeps your traffic safe at all stages of the process.
Is RADIUS an access control system?
Remote Access Dial In User Service (RADIUS) and Terminal Access Controller Access-Control System Plus (TACACS+) are two common security protocols used to provide centralized access into networks.
What features does RADIUS provide for remote access connections?
RADIUS contains three user management pieces—authentication, authorization, and accounting—which Livingston referred to as AAA. RADIUS authentication identifies a remote user by checking the user's identity against a user account database.
What is RADIUS server used for?
The RADIUS server collects identification information about all of its users' credentials. The server waits until it gets a request from a client or NAS, which can be devices or systems like wireless access points or virtual private networks (VPNs).
Is RADIUS still used?
RADIUS has evolved far beyond just the dial up networking use-cases it was originally created for. Today it is still used in the same way, carrying the authentication traffic from the network device to the authentication server.
What protocol does RADIUS use?
RADIUS is a client/server protocol that runs in the application layer, and can use either TCP or UDP. Network access servers, which control access to a network, usually contain a RADIUS client component that communicates with the RADIUS server.
What are three characteristics of RADIUS?
Question 5. What are three characteristics of RADIUS? Answers B, C, and E are correct. RADIUS is an open standard developed by the IETF; it uses UDP/IP and is only able to encrypt passwords. Answers A and D describe TACACS+; it is Cisco proprietary, uses TCP/IP, and encrypts all the data.
Does RADIUS use LDAP?
LDAP uses Transmission Control Protocol (TCP) in order to ensure reliable connection across the network. TCP ensures a connection, but does require more network overhead. RADIUS uses User Datagram Protocol (UDP), which minimizes network overhead but does not ensure a connection.
What is RADIUS server and how it works?
RADIUS servers receive user connection requests, authenticate the user, and then return the configuration information necessary for the client to deliver service to the user. A RADIUS server can act as a proxy client to other RADIUS servers or other kinds of authentication servers.
Is RADIUS a TCP or UDP?
UDPThe RADIUS protocol uses UDP packets. There are two UDP ports used as the destination port for RADIUS authentication packets (ports 1645 and 1812).
How does RADIUS work VPN?
The user tries to authenticate, either through a browser-based HTTPS connection to the device over port 4100, or through a connection using Mobile VPN with IPSec. The device reads the user name and password. The device creates a message called an Access-Request message and sends it to the RADIUS server.
Is RADIUS used with Active Directory?
The RADIUS server authenticates the user credentials and checks the user's access privileges against its central database, which can be in a flat-file format or stored on an external storage source such as SQL Server or Active Directory Server.
What is RADIUS system?
RADIUS (Remote Authentication Dial-In User Service) is a client-server protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
What is RADIUS wireless security?
At its most basic, RADIUS is an acronym for Remote Authentication Dial In User Service. The “Dial In” part of the name shows RADIUS's age: it's been around since 1991. Today, however, RADIUS is widely used to authenticate and authorize users to remote WiFi networks (and VPNs, network infrastructure gear, and more).
What is the difference between RADIUS and Kerberos?
Kerberos is a protocol that assists in network authentication. This is used for validating clients/servers in a network using a cryptographic key....Difference between Kerberos and RADIUS :S.No.KerberosRADIUS1.It is called as Kerberos.It is short used for Remote Authentication Dial-In User Service.5 more rows•Dec 15, 2020
Is RADIUS a secure protocol?
RADIUS stands for Remote Authentication Dial-In User Service, is a security protocol used in the AAA framework to provide centralized authentication for users who want to gain access to the network.
What does a Radius server respond to?
RADIUS server responds with Accept, Reject, or Challenge.
What port is used for RADIUS?
The early deployment of RADIUS was done using UDP port number 1645, which conflicts with the "datametrics" service. Because of this conflict, RFC 2865 officially assigned port number 1812 for RADIUS. Most Cisco devices and applications offer support for either set of port numbers.
What does it mean when a NAS server rejects access request?
When the RADIUS server receives the Access-Request from the NAS, it searches a database for the username listed. If the username does not exist in the database, either a default profile is loaded or the RADIUS server immediately sends an Access-Reject message. This Access-Reject message can be accompanied by a text message indicating the reason for the refusal.
What is a rabid server?
RADIUS is a client/server protocol. The RADIUS client is typically a NAS and the RADIUS server is usually a daemon process running on a UNIX or Windows NT machine. The client passes user information to designated RADIUS servers and acts on the response that is returned. RADIUS servers receive user connection requests, authenticate the user, and then return the configuration information necessary for the client to deliver service to the user. A RADIUS server can act as a proxy client to other RADIUS servers or other kinds of authentication servers.
What is the purpose of the RADIUS accounting function?
The RADIUS accounting functions allow data to be sent at the start and end of sessions, indicating the amount of resources (such as time, packets, bytes, and so on) used during the session.
What is the UDP protocol for NAS?
Communication between a network access server (NAS) and a RADIUS server is based on the User Datagram Protocol (UDP). Generally, the RADIUS protocol is considered a connectionless service. Issues related to server availability, retransmission, and timeouts are handled by the RADIUS-enabled devices rather than the transmission protocol.
Why is Radius used?
It is used to authenticate access to internal and wireless networks and other integrated email services.
What Does Remote Authentication Dial-in User Service (RADIUS) Mean?
Remote Authentication Dial-In User Service (RADIUS) is a network protocol that provides security to networks against unauthorized access. RADIUS secures a network by enabling centralized authentication of dial-in users and authorizing their access to use a network service. It manages remote user authentication, authorization and accounting (AAA).
What is a radius?
It manages remote user authentication, authorization and accounting (AAA). RADIUS is used by many companies to enable roaming between Internet service providers (ISPs), providing a single global set of credentials to be used on any public network.
Who developed the Radius protocol?
RADIUS was originally developed by the American corporation Livingston Enterprises in 1991. It is a network protocol for managing access server authentication and accounting as defined in Request for Comments (RFC) 2865, which was later moved into the Internet Engineering Task Force standards.
What can a Radius server do?
Once users have been enrolled for a certificate, the RADIUS server can use that to verify the level of permissions they have. You can create and customize group security policies to segment users into different levels of resource access, control who has access to Wi-Fi, VPN, and other company resources.
What is the most secure authentication protocol for Radius?
The most secure iteration of RADIUS uses the EAP-TLS authentication protocol to authenticate users with digital certificates instead of credentials. Certificates eliminate the need for password-based authentication which in turn eliminates the security risks usually associated with passwords. You no longer have to worry about the threat of phishing or MITM attacks and you have complete transparency over who is using your network. Just like E2EE, certificates encrypt private data so a hacker wouldn’t be able to do anything if they get a hold of the certificate.
Why Use a VPN for Remote Access?
Virtual Private Networks (VPN) are designed to protect your online identity by connecting your device to a secure server rather than your typical ISP. The goal is to keep your private information private. VPNs encrypt web traffic so no one is able to see your data, whether it’s a hacker, corporation, or government.
Can a cybercriminal access sensitive information?
If compromised, cybercriminals may have access to sensitive information. Enabling secure VPN Authentication can be the difference-maker in your network security. SecureW2 allows organizations to equip all their devices with Digital Certificates for secure VPN Authentication and our RADIUS supports token-based VPN, ...
Is Radius a VPN?
Cloud RADIUS is especially a great solution for VPN security. Check out our solutions page to see if we can get you set up with a state-of-the-art VPN solution that ensures your companies resources stay private. Learn about this author.
Can you use a VPN with a Radius?
The solution to potential security lapses of VPN is simple – use your RADIUS for VPN authentication. Yes, you can use your organization’s RADIUS to authenticate remote users. By configuring the VPN to connect to your office access point, the remote device can be “virtually” present ...
Why are colocated servers important?
Colocated servers with backup systems and data are used by businesses to ensure that in the event of a disaster, recovery time is minimised.
What is cloud phone system?
The Cloud-based phone system is a fully flexible business phone system that is hosted in the cloud and allows access via an internet connection. Cloud phones have the same functionality as a conventional phone system plus answer/make calls from any phone handset, laptop, desktop, or smartphone (softphone) – from anywhere.
Why is it necessary to adjust the radius timeout?
To ensure there is time to validate users’ credentials, perform two-step verification, receive responses, and respond to RADIUS messages , it is necessary to adjust the RADIUS timeout value.
What is a connection request policy?
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients.
What is NPS in a remote authentication?
When you deploy Network Policy Server (NPS) as a Remote Authentication Dial-In User Service (RADIUS) server, NPS performs authentication, authorization, and accounting for connection requests for the local domain and for domains that trust the local domain.
How to see TS gateway authorization policy?
Open the Policies menu in the left column and select Connection Request Policies. You should see a policy called TS GATEWAY AUTHORIZATION POLICY that was created when RD Gateway was configured. This policy forwards RADIUS requests to the Multi-Factor Authentication Server.
How to add a new client to a rabid server?
Right-click RADIUS Clients under RADIUS Clients and Servers in the left column and select New.
Do I need a working RDS?
You must have a working Remote Desktop Services (RDS) infrastructure and Azure MFA infrastructure in place If you do not , then you can follow the steps Installing and Configuring Remote Desktop Services (RDS) and Implementing Azure Multi-Factor Authentication (MFA) Server On-premises with High Availability (HA)
What is set-remoteaccessradius?
The Set-RemoteAccessRadius cmdlet edits the properties associated with an external RADIUS server being used for VPN authentication, accounting for DirectAccess (DA) and VPN, and one-time password (OTP) authentication for DA.
What is a ra server?
A RADIUS server configuration for Accounting and OTP are global in nature, such as applying the entire Remote Access (RA) deployment. A RADIUS server configuration for VPN applies only to a specific VPN server, and all servers in a load balancing cluster, or if multi-site is deployed, to all VPN servers at a site.
What happens if a server is not specified in a multisite deployment?
If an entry point is not specified in a multi-site deployment, then the entry point to which the server on which the cmdlet is run belongs is used. The server could also be represented by using the ComputerName parameter.
What is required for a Radius server to be used with DirectAccess?
The RADIUS server must be configured with the necessary license and software and/or hardware distribution tokens to be used by DirectAccess with OTP. This process will be specific to each RADIUS vendor implementation.
What ports does a RADIUS server use?
The RADIUS server uses UDP ports for communication purposes, and each RADIUS vendor has its own default UDP ports for incoming and outgoing communication. For the RADIUS server to work with the Remote Access server, make sure that all firewalls in the environment are configured to allow UDP traffic between the DirectAccess and OTP servers over the required ports as needed.
What is a RADIUS server?
The RADIUS server supports a variety of methods to authenticate a user. When it is provided with the user name and original password given by the user, it can support PPP, Password Authentication Protocol (PAP), or Challenge Handshake Authentication Protocol (CHAP), UNIX login, and other authentication mechanisms.
How is a RADIUS server authenticated?
Transactions between the client and RADIUS server are authenticated through the use of a shared secret, which is never sent over the network. In addition, any user passwords are sent encrypted between the client and RADIUS server. This eliminates the possibility that someone snooping on an unsecured network could determine a user's password.
What does RST mean in TCP?
TCP provides immediate indication of a crashed, or not running, server by a reset (RST). You can determine when a server crashes and returns to service if you use long-lived TCP connections. UDP cannot tell the difference between a server that is down, a slow server, and a non-existent server.
What is NAS in a router?
A network access server (NAS) operates as a client of RADIUS. The client is responsible for passing user information to designated RADIUS servers, and then acting on the response that is returned. RADIUS servers are responsible for receiving user connection requests, authenticating the user, and returning all configuration information necessary for the client to deliver service to the user. The RADIUS servers can act as proxy clients to other kinds of authentication servers.
What is a radian?
RADIUS is an access server that uses AAA protocol. It is a system of distributed security that secures remote access to networks and network services against unauthorized access. RADIUS comprises three components:
When did Cisco release the RADIUS protocol?
Cisco has supported the RADIUS protocol since Cisco IOS® Software Release 11.1 in February 1996. Cisco continues to enhance the RADIUS Client with new features and capabilities, supporting RADIUS as a standard.
Is Radius useful for router management?
RADIUS does not allow users to control which commands can be executed on a router and which cannot. Therefore, RADIUS is not as useful for router management or as flexible for terminal services.
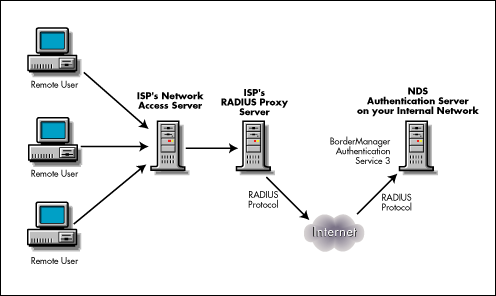
How Does Radius Work?
Radius Authentication Methods
- After a user provides their login credentials, the RADIUS server uses one of the following authentication methods: 1. Password Authentication Protocol (PAP): This relies on a RADIUS client forwarding a user ID and password to the RADIUS authentication server. If the credentials prove to be correct, the client allows the remote user’s connection. 2. Challenge Handshake Aut…
How Is Radius used?
- RADIUS is often used in situations where a remote worker needs to access a company’s network and data centers. It ensures that only authenticated, authorized users are granted access with minimal disruptions to the employee’s productivity. Additionally, RADIUS is an important part of the zero trust security framework in which all users are assumed ...
Radius Benefits
- RADIUS provides a central platform for user and system authentication, which makes managing user access a much easier task. The centralized nature of RADIUS also makes it easy for multiple IT administrators to manage the same network. Plus, the fact that each user has unique credentials in a RADIUS environment eliminates the need for routine password updates. This mi…
Radius Challenges
- RADIUS is typically implemented on-premise, which can make it difficult and time-consuming to set up and maintain. However, there are cloud-based options that can make implementation and maintenance easier. Additionally, there are many different configuration options that can make it difficult to set up a new RADIUS server and integrate it into an existing environment. These road…
Introduction
- The Remote Authentication Dial-In User Service (RADIUS) protocol was developed by Livingston Enterprises, Inc., as an access server authentication and accounting protocol. The RADIUS specification RFC 2865 obsoletes RFC 2138. The RADIUS accounting standard RFC 2866 obsoletes RFC 2139.
Prerequisites
- Requirements
There are no specific prerequisites for this document. - Components Used
This document is not restricted to specific software and hardware versions.
Background Information
- Communication between a network access server (NAS) and a RADIUS server is based on the User Datagram Protocol (UDP). Generally, the RADIUS protocol is considered a connectionless service. Issues related to server availability, retransmission, and timeouts are handled by the RADIUS-enabled devices rather than the transmission protocol. RADIUS is a client/server proto…
Authentication and Authorization
- The RADIUS server can support a variety of methods to authenticate a user. When it is provided with the username and original password given by the user, it can support PPP, PAP or CHAP, UNIX login, and other authentication mechanisms. Typically, a user login consists of a query (Access-Request) from the NAS to the RADIUS server and a corresponding response (Access-…
Accounting
- The accounting features of the RADIUS protocol can be used independently of RADIUS authentication or authorization. The RADIUS accounting functions allow data to be sent at the start and end of sessions, indicating the amount of resources (such as time, packets, bytes, and so on) used during the session. An Internet service provider (ISP) might use RADIUS access co…
Related Information