Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients.
Full Answer
What is a connection policy in radius?
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients.
What is radius and how does it work?
What Is RADIUS? Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that authorizes and authenticates users who access a remote network. A protocol is a collection of rules that control how something communicates or operates.
What are the different types of radius clients?
RADIUS clients are network access servers, such as wireless access points, virtual private network (VPN) servers, 802.1X-capable switches, and dial-up servers. RADIUS proxies, which forward connection request messages to RADIUS
What is a remote access policy?
A remote access policy defines the conditions, remote access permissions, and creates a profile for every remote connection made to the corporate network. Through remote access policies you can define the following: Grant or deny dial-in based on connection parameters such as type and time of the day

What is RADIUS in remote access?
RADIUS (Remote Authentication Dial-In User Service) is a client-server protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What features does RADIUS provide for remote access connections?
RADIUS contains three user management pieces—authentication, authorization, and accounting—which Livingston referred to as AAA. RADIUS authentication identifies a remote user by checking the user's identity against a user account database.
Is RADIUS secure over Internet?
Yes, you are right. Since we use EAP or PEAP authentication, the user password is absolutely secure even on the Internet.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
What is a access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What are three characteristics of RADIUS?
Question 5. What are three characteristics of RADIUS? Answers B, C, and E are correct. RADIUS is an open standard developed by the IETF; it uses UDP/IP and is only able to encrypt passwords. Answers A and D describe TACACS+; it is Cisco proprietary, uses TCP/IP, and encrypts all the data.
Is RADIUS still used?
RADIUS has evolved far beyond just the dial up networking use-cases it was originally created for. Today it is still used in the same way, carrying the authentication traffic from the network device to the authentication server.
Does RADIUS use LDAP?
LDAP uses Transmission Control Protocol (TCP) in order to ensure reliable connection across the network. TCP ensures a connection, but does require more network overhead. RADIUS uses User Datagram Protocol (UDP), which minimizes network overhead but does not ensure a connection.
Is RADIUS better than VPN?
The benefits of using your RADIUS in conjunction with VPN for remote access are twofold: It's more secure. After the VPN connects to your office access point, the users undergo RADIUS authentication for network and resource access. Doubling up on protection keeps your traffic safe at all stages of the process.
What protocol does RADIUS use?
RADIUS is a client/server protocol that runs in the application layer, and can use either TCP or UDP. Network access servers, which control access to a network, usually contain a RADIUS client component that communicates with the RADIUS server.
Does RADIUS encrypt all communication?
TACACS+ provides more control over the authorization of commands while in RADIUS, no external authorization of commands is supported. All the AAA packets are encrypted in TACACS+ while only the passwords are encrypted in RADIUS i.e more secure....Difference between TACACS+ and RADIUS.TACACS+RADIUSUsed for device administration.used for network access8 more rows•Oct 26, 2021
Why you must create a remote access policy for VPN connectivity?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
Why should an organization have a remote access policy even if IT already has an acceptable use policy AUP for employees?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What is a network access policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
What is required for a Radius server to be used with DirectAccess?
The RADIUS server must be configured with the necessary license and software and/or hardware distribution tokens to be used by DirectAccess with OTP. This process will be specific to each RADIUS vendor implementation.
What ports does a RADIUS server use?
The RADIUS server uses UDP ports for communication purposes, and each RADIUS vendor has its own default UDP ports for incoming and outgoing communication. For the RADIUS server to work with the Remote Access server, make sure that all firewalls in the environment are configured to allow UDP traffic between the DirectAccess and OTP servers over the required ports as needed.
What is a RADIUS authorization?
Authorization: RADIUS authorizes devices or users, allowing them to use specific services on the network. Accounting: RADIUS accounts for the number of resources used—such as packets, bytes, and the time expended—during the session.
How Does RADIUS Authentication and Authorization Work?
To authenticate a network, RADIUS uses a client/server model. The messages sent back and forth enable administrators to vet who has access to the connection by using a database containing approved user credentials.
What Is a RADIUS Server?
A RADIUS server bases its operation on the User Datagram Protocol (UDP), and it is typically a daemon application that runs on a Windows or UNIX machine. A daemon is a program that runs as a background process. The RADIUS server collects identification information about all of its users’ credentials. The server waits until it gets a request from a client or NAS, which can be devices or systems like wireless access points or virtual private networks (VPNs).
How Does RADIUS Accounting Work?
RADIUS accounting is used apart from the authorization and authentication processes and enables data to be sent at the close of the session . This data outlines elements such as the data packets that were sent, how long the session lasted, and how much data was sent.
What is a supplicant in a NAS?
A program designed to make login requests, called a supplicant, carries the user’s credentials to the NAS. This may include the user’s network address, username, and password.
What is an authorization attribute?
When access is accepted, it is done according to authorization attributes, which are conditions that govern how the user will have access. Some of these may include how long the user can be connected, the kind of protocol to be used, or the Internet Protocol (IP) address the user will have during the session.
Why is Radius a scalable solution?
RADIUS is a scalable solution because it can be implemented in a variety of different networks.
What is the Default RADIUS Authentication Port?
By default, the RADIUS server uses UDP 1812 for authentication and authorization and 1813 for accounting as defined by the IETF, but can also use 1645 and 1646.
What is RADIUS?
Remote Access Dial-In User Service, or RADIUS, is a client-server mechanism that secures the connection between users and clients and ensures that only approved users can access the network. It is a networking protocol that offers users a centralized means of authentication and authorization.
Why is Radius important?
RADIUS is imperative for securely authenticating users for network access.
When was the Radius invented?
The earliest RADIUS was developed by Livingston Enterprises in 1991. It was designed to replace dial-in services used then so that the internet would be more accessible to the average person.
Do you need a PKI for EAP TLS?
If you want to use EAP-TLS, you will need a PKI. A Public Key Infrastructure (PKI) enables organizations to issue and manage x.509 digital certificates that can encrypt connections between end user devices and RADIUS servers. Certificates are encrypted themselves, so even if a malicious actor could obtain one, they wouldn’t be able to authenticate. On the contrary, other personal identifiers can be intercepted and used to fake identity – such as the recent case of purchased Slack cookies being used to infiltrate Electronic Arts.
Is a Radius server wise?
It’s easy to see already why using a RADIUS server is a wise move. However, setting an on-prem RADIUS server up takes time, money, and other resources. So, how can you weave a RADIUS server into your infrastructure in the most economical way possible?
Does RADIUS Use LDAP?
Yes, RADIUS can use the LDAP protocol to communicate with servers designed for LDAP communication. Active Directory (AD) is a widely-used platform that uses LDAP for authentication purposes. However, AD is notorious for its lack of flexibility when it comes to cloud computing services. Luckily, SecureW2’s Cloud RADIUS makes it easy for AD-domain admins to bridge the gap from on-prem to cloud.
Why is it necessary to adjust the radius timeout?
To ensure there is time to validate users’ credentials, perform two-step verification, receive responses, and respond to RADIUS messages , it is necessary to adjust the RADIUS timeout value.
What is a connection request policy?
Connection request policies are sets of conditions and settings that allow network administrators to designate which Remote Authentication Dial-In User Service (RADIUS) servers perform the authentication and authorization of connection requests that the server running Network Policy Server (NPS) receives from RADIUS clients.
What is NPS in a remote authentication?
When you deploy Network Policy Server (NPS) as a Remote Authentication Dial-In User Service (RADIUS) server, NPS performs authentication, authorization, and accounting for connection requests for the local domain and for domains that trust the local domain.
How to see TS gateway authorization policy?
Open the Policies menu in the left column and select Connection Request Policies. You should see a policy called TS GATEWAY AUTHORIZATION POLICY that was created when RD Gateway was configured. This policy forwards RADIUS requests to the Multi-Factor Authentication Server.
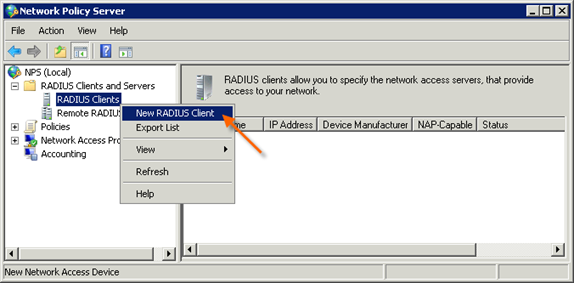
How to add a new client to a rabid server?
Right-click RADIUS Clients under RADIUS Clients and Servers in the left column and select New.
How long between requests when server is identified as unavailable?
In the Number of seconds between requests when server is identified as unavailable field, change the default value of 30 seconds to a value that is equal to or greater than the value you specified in the previous step.
Do I need a working RDS?
You must have a working Remote Desktop Services (RDS) infrastructure and Azure MFA infrastructure in place If you do not , then you can follow the steps Installing and Configuring Remote Desktop Services (RDS) and Implementing Azure Multi-Factor Authentication (MFA) Server On-premises with High Availability (HA)
What is remote access policy?
Remote access policies are an ordered set of rules that define how connections are either authorized or rejected. For each rule, there are one or more conditions, a set of profile settings, and a remote access permission setting. If a connection is authorized, the remote access policy profile specifies a set of connection restrictions. The dial-in properties of the user account also provide a set of restrictions. Where applicable, user account connection restrictions override the remote access policy profile connection restrictions.
How to verify remote access server?
1. Either use the Rqc.exe notification component or create a notification component that provides verification to the remote access server that the remote access client computer complies with network policy requirements. 2. Create a validation script that authorizes the client configuration.
How to enable EAP authentication?
Follow these steps to enable EAP authentication:#N#1.#N#Select Start | Administrative Tools | Internet Authentication Service.#N#2.#N#The IAS management console is displayed. Click to highlight Remote Access Policies in the left column.#N#3.#N#In the right column, select Connections to Microsoft Routing and Remote Access Server .#N#4.#N#Select Action | Properties from the menu, or right-click and select Properties from the context menu. #N#5.#N#The Properties dialog box is displayed. Click the Edit Profile button .#N#6.#N#The Edit Dial-in Profile dialog box is displayed. Select the Authentication tab.#N#7.#N#The authentication methods supported by IAS are displayed, as shown in Figure 5.14. You can enable or disable the non-EAP authentication methods here. You can also change the order in which the selected EAP types are negotiated by moving them up or down in the list, using the Move Up and Move Down buttons.#N#Sign in to download full-size image#N#Figure 5.14. Authentication Methods#N#8.#N#Click the EAP Methods button. A list of the currently enabled EAP types is displayed.#N#9.#N#Click Add and select MD5-Challenge from the list.#N#10.#N#Click OK, then click OK in the EAP types list.#N#11.#N#Click OK to exit the Edit Profile dialog box.#N#12.#N#Click OK to exit the Properties dialog box.
How to enable EAP on IAS?
To enable EAP authentication on an IAS server, you create a Remote Access Policy that allows EAP authentication, or you modify an existing policy. Exercise 5.07 demonstrates how to modify a policy to allow the use of MD5 CHAP authentication through EAP.
How to delete VPN policy?
You can delete the other policies if you require only VPN connections to your ISA firewall. Right-click on Connections to other access servers, and click Delete. Repeat with Connections to Microsoft Routing and Remote Access server.
How to enable PPP multilink?
The nature of multilink requires dialing to multiple devices or endpoints. To enable Multilink on a remote access client, you must enable multiple device dialing on the client system through the Network and Dial-up Connections folder. Again, if unlimited connectivity is not available, the nature of Multilink presents cost prohibitive problems due to the lack of provisions to link and unlink extra physical connections on an as-needed basis.
What is network access quarantine?
Network Access Quarantine Control controls client access after initial authentication has been completed. The client uses an installed notification component (Rqc.exe) to communicate system compliance information to the Remote Access Server’s listening component (Rqs.exe) after testing the client with a specially configured script known as the Connection Manager profile. Two attributes (MS-Quarantine-IP Filter and MS-Quarantine-Session-Timeout) filter IP traffic between the remote access client and the remote access server until the dient system passes the configuration requirements or the timeout period is reached.
