The firewall -oriented operating system pfSense has several VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
How to build your own firewall with pfSense?
How to build your own firewall with pfSense
- Install pfSense on your device. Download the installer from the pfSense website, taking care to get the version that matches your environment and preferred installation method.
- Console configuration. Once the system has rebooted, you’ll be prompted to set up basic networking. ...
- Initial configuration wizard. ...
- IPv6. ...
- Setting up local network services. ...
How to set up pfSense as OpenVPN client?
pfSense OpenVPN Setup Tutorial
- Downloading configuration bundle. The first step in the setup is downloading the OpenVPN configuration bundle. ...
- Creating a Certificate Authority on pfSense. Login with your credentials to the pfSense via a browser. ...
- Configuring OpenVPN on pfSense. ...
- Creating OpenVPN Interface. ...
- Configuring NAT. ...
- Setting WAN Routing. ...
- Confirming the OpenVPN configuration status. ...
How to setup failover in pfSense?
pfSense dual WAN failover configuration steps 1. Configure two WAN interfaces 2. Establish dual WAN group 3. Add firewall rules required for the dual WAN set-up 4. Reconfigure Squid Proxy service 5. Configure default gateway auto failover 6. Best practice: Configure DNS servers Configuring pfSense 2.3 dual WAN failover 1.
How to open the web configuration of pfSense?
To reach the GUI, follow this basic procedure:
- Connect a client computer to the same network as the LAN interface of the firewall. ...
- On the client computer, open a web browser such as Firefox, Safari, or Chrome and navigate to https://192.168.1.1. ...
- Enter the default credentials in the login page: username admin password pfsense

How to Configure IPsec VPN on pfSense?
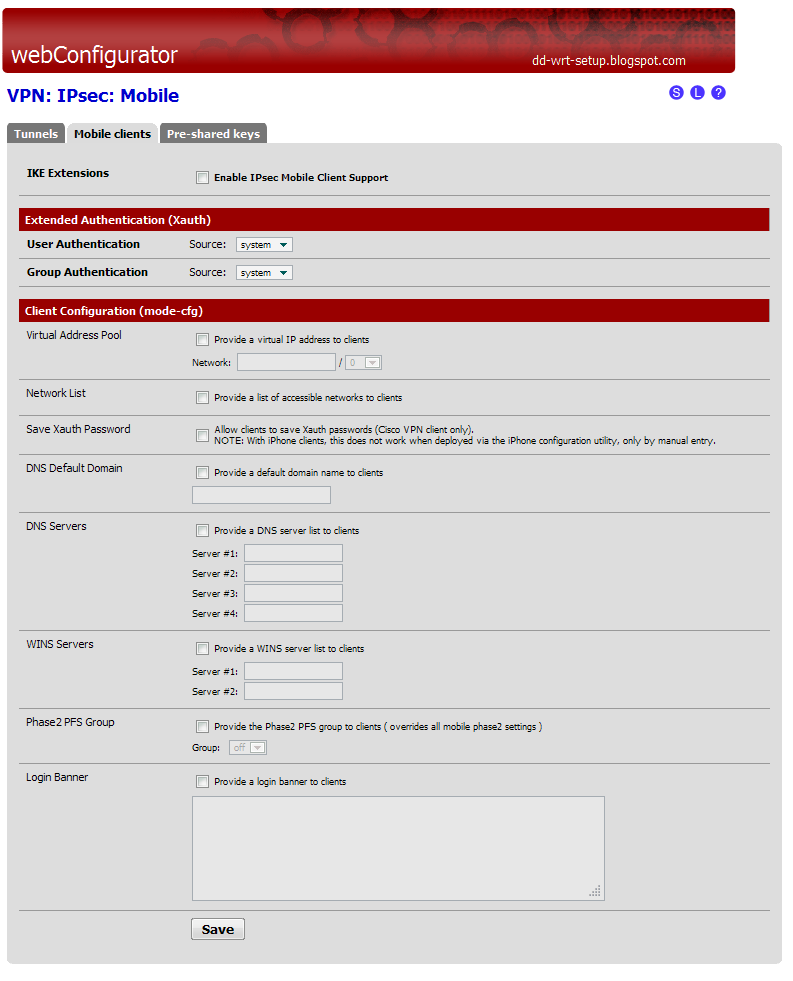
Setup IPsecNavigate to VPN > IPsec, Mobile Clients tab in the pfSense software GUI.Configure the settings as follows: Enable IPsec Mobile Client Support. Checked. User Authentication. Local Database (Not used, but the option must have something selected) Provide a virtual IP address to clients. Unchecked. ... Click Save.
How to Enable Mobile Support for your IPsec tunnel in pfSense?
Mobile Client SettingsNavigate to VPN > IPsec, Mobile Clients tab.Enable IPsec: Enable IPsec Mobile Client Support. Checked. ... Set the authentication options as follows: User Authentication. ... Set the Client Configuration options. ... Click Save.Click Create Phase 1 at the top of the screen if it appears.
Does pfSense support IKEv2?
To make Windows 10 clients work, we need to add support to the following algorithms on the server-end. With these two slightly weaker algorithms added, the Windows 10 built-in VPN client will be able to connect to the pfSense IKEv2 VPN server.
Can I use pfSense as a VPN?
pfSense® software offers several VPN options: IPsec, OpenVPN, WireGuard and L2TP. This section provides an overview of VPN usage, the pros and cons of each type of VPN, and how to decide which is the best fit for a particular environment.
What is IPsec mobile client support?
The WatchGuard IPSec Mobile VPN Client is installed on a mobile client computer, whether the user travels or works from home. The user connects with a standard Internet connection and activates the Mobile VPN client to get access to protected network resources.
What is IKEv2 Mobike?
IKEv2 Mobility and Multi-homing Protocol (MOBIKE) allows the IP addresses associated with IKEv2 and tunnel mode IPSec Security Associations (SA) to change. A mobile Virtual Private Network (VPN) client could use MOBIKE to keep the connection with the VPN gateway active while moving from one address to another.
Does pfSense use Strongswan?
PfSense firewall uses an open source tool Strongswan which provides the IPsec VPN functionality. Both phases of IPsec (Key sharing and encryption) is implemented by Strongswan tool on Linux/Unix platforms.
What is IPsec identifier?
The L2TP/IPsec client on Android has the ability to set a custom identifier, which allows L2TP/IPsec to function with the server on pfSense® software using Pre-Shared Keys. Clients on other operating systems do not allow for this, which makes them incompatible with current versions of pfSense software.
At which layer of the TCP IP model does IPsec operate?
What is IPsec? IPsec helps keep private data secure when it is transmitted over a public network. More specifically, IPsec is a group of protocols that are used together to set up secure connections between devices at layer 3 of the OSI model (the network layer).
Is pfSense OpenVPN free?
Secure Remote Network Access Using OpenVPN VPNs provide strong security by encrypting all of the traffic sent between the network and the remote client. Since pfSense is open source and available for free this project won't cost you anything to complete.
Is WireGuard better than OpenVPN?
WireGuard offers a more reliable connection for mobile users than OpenVPN because it handles network changes better. OpenVPN adds a data overhead of up to 20%, whereas WireGuard uses just 4% more data (compared with not using a VPN). VPN services need to include mitigations to ensure user privacy when using WireGuard.
Does pfSense support WireGuard?
WireGuard is available as an experimental add-on package on pfSense Plus 21.05, pfSense CE 2.5. 2, and later versions.
Does pfSense support WireGuard?
WireGuard is available as an experimental add-on package on pfSense Plus 21.05, pfSense CE 2.5. 2, and later versions.
What is IPsec in pfSense?
IPsec on pfSense® software offers numerous configuration options which influence the performance and security of IPsec connections. For most users performance is the most important factor.
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
What to do before configuring IPsec?
Before configuring the IPsec portion, setup the L2TP server as described in L2TP Server Configuration and add users, firewall rules, etc, as covered there.
Is StrongSwan IPsec compatible with Windows?
As warned at the start of the chapter, the Windows client, among others, and the strongSwan IPsec daemon are not always compatible, leading to failure in many cases. We strongly recommend using another solution such as IKEv2 instead of L2TP/IPsec.
How to add P2 to IPsec?
On the IPsec VPN tunnels page (where you should be right now), for our P1 entry we just created, we click successively on the “Show Phase 2 Entries (0)”, then on “+ Add P2”.
What encryption algorithm should I use for AES?
Encryption Algorithm: if both parties support AES-GCM, we recommend the use of AES256-GCM or AES128-GCM; this will provide a good level of encryption and will be compatible with the cryptographic acceleration offered by AES-NI. Otherwise, ideally choose AES with a key length of 256 bits. Finally, we keep SHA256 for hash function and 14 or 16 for the value of the Diffie-Hellman group (DH group – used for key exchange).
Is PPTP support removed from PfSense?
PPTP Support is removed from pfSense 2.3 or something so how can you use it?
Is PfSense free?
The pfSense Book is free of charge!
Does PfSense allow access to local network?
Though you should only do so if your ISP requires it for example. pfSense doesn't allow me to access my local network when connected to remote organization via vpn. pfSense has no part in that decision. Your client either sends the traffic over the VPN or tries to use it's local connection.
Does PfSense use VPN?
pfSense has no part in that decision. Your client either sends the traffic over the VPN or tries to use it's local connection.
How does VPN work?
How it works. The goal is to offer a VPN solution for travelling or teleworking users allowing them to have secure access to the company’s LAN. These users can use a computer or a smartphone to connect. In all cases, they will use an OpenVPN client.
What is the default port for a local port?
Local port: we keep the default value (1194).
How to add a certificate to a symlink?
Go in the “Certificates” tab, then click on the “+ Add/Sign” button at the bottom right of the list of existing certificates.
Is OpenVPN compatible with Mac?
OpenVPN = the perfect solution for home-office users. OpenVPN is easy to implement and is compatible with all types of platforms (Windows, Mac, Android, iOS, …) This article does not cover site-to-site mode configuration of OpenVPN (shared key or X.509).
What is PfSense firewall?
PfSense firewall uses an open source tool Strongswan which provides the IPsec VPN functionality. Both phases of IPsec (Key sharing and encryption) is implemented by Strongswan tool on Linux/Unix platforms. It provides the internet key exchange (IKE) or automatic sharing of keys among nodes or gateways of IPsec VPN and then uses the Linux/Unix kernel implementation of authentication (AH) and encryption ( ESP). Stongswan uses the OpenSSL implementation of cryptographics algorithms ( such as AES128/256, MD5/SHA1 etc) in the first phase (IKE phase) of IPsec VPN. Encapsulated security payload (ESP) of IPsec VPN is available in Linux / Unix kernels which is uses by Strongswan in the second phase of VPN.
How to create a tunnel on PfSense?
Check Enable IPsec option to create tunnel on PfSense. Click on plus button to add new policy of IPsec tunnel on local side (side-a in this case). Following snapshots show the setting for IKE phase (1st phase) of IPsec.
What is the default encryption algorithm for first phase?
The Main mode is selected because it is more secure than aggressive mode. The Pre shared key or shared secret for both devices is "test12345" . The following snapshot also shows the encryption setting for first phase. Default selection of encryption algorithm is AES256 and SHA1 for hashing algorithm.
What is the second phase of IPsec?
In the first phase, IKE is configured and encryption/authentication algorithm are selected. Second phase of IPsec is setting ESP parameters such as encryption/authentication on both VM. Setting such as local/remote ip, local/remote networks, encryption/authentication algorithms ) of IPsec VPN on both VM's should be correct to establish tunnel between VM.
What is IPsec rule?
IPsec rule is also configured in firewall to pass traffic through the established VPN. It is also important to make sure that remote device is available for IPsec VPN. Following snapshot shows that, remote device is up and replying back. After ensuring gateway to gateway connectivity, next step is to configure VPN (both phase 1 and phase 2) on VM's.
What is IPsec protocol?
Two components of IPsec protocol are Authentication Header (AH) and Encapsulating Security Payload (ESP) to provide packet integrity, authentication and confidentiality security features. Cryptographic security mechanism are used in IPsec to protect communications over IP layer. IPSec protocol allows to encrypt and authenticate all IP layer traffic between local and remote location.
Is Strongswan available on Linux?
Strongswan package is already installed on the fresh installation of PfSense and available on web interface under VPN menu. However, installation of Strongswan on Linux platform is also available on previous article.

Network Diagram
1/3 – Configuring The Phase 1
- Go to VPN > IPsec: Click on the “+ Add” button. The fields to be filled in are the following: 1. Disabled: check this case to disable this phase 1 (and thus to disable the IPsec VPN). 2. Key Exchange version: allows you to choose the version of the IKE (Internet Key Exchange) protocol. Choose “IKEv2“. If the other peer does not support IKEv2 or if ...
2/3 – Configuring The Phase 2
- On the IPsec VPN tunnels page (where you should be right now), for our P1 entry we just created, we click successively on the “Show Phase 2 Entries (0)”, then on “+ Add P2”. The fields to be filled in are the following: 1. Disabled: check this case to disable this phase 2. 2. Mode: keep the default value “Tunnel IPv4”. 3. Local Network: the local subnet reachable through this VPN. In our case …
3/3 – Configuring The Firewall Rules
- There is at least two rules to configure: one rule for the traffic from the LAN to the IPsec VPN ; and another one for the traffic from the VPN to the LAN. For the LAN rule, look for an example: For the IPsec VPN rule, look for an example: The configuration is done. It should work. Did you like this article? Are you looking for professional equipment? Visit our shop.