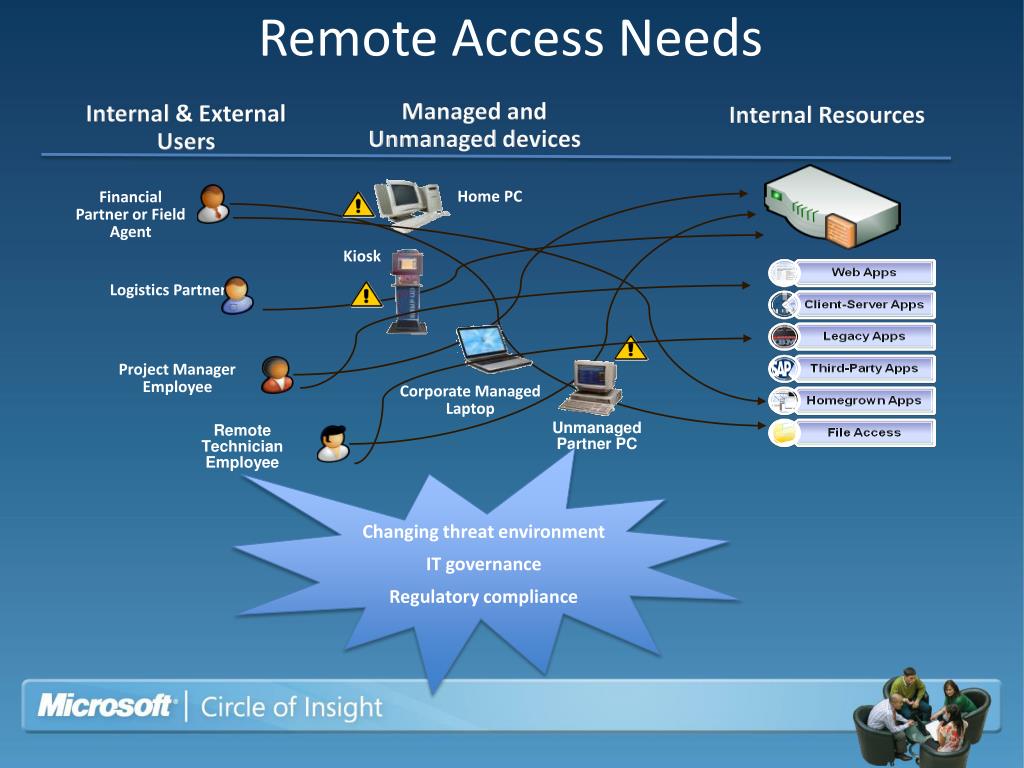
Remote access means, the ability to perform troubleshooting operations or simply view a device that is not physically reachable by you. It enables you with the power to remotely operate on a device even out of your corporate network without VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Full Answer
What is remote access and why do we need it?
Once the software is installed, the local computer can access the remote computer and perform several tasks like running applications, managing updates, and even handling administrative tasks. Why do enterprises need remote access? For businesses, remote access can maximize efficiency and boost employee productivity.
How to easily run Task Manager remotely?
How to Easily Run Task Manager Remotely Ctrl + Shift + Esc Or to Start Task Manager – Windows XP Remote Desktop Right click the Taskbar -> select Task Manager
How do I install the remote access role?
You must install the Remote Access role on a server in your organization that will act as the Remote Access server. On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features.
How do I deploy DirectAccess for remote management only?
In the middle pane of the Remote Access Management console, in the Step 1 Remote Clients area, click Configure. In the DirectAccess Client Setup Wizard, on the Deployment Scenario page, click Deploy DirectAccess for remote management only, and then click Next.
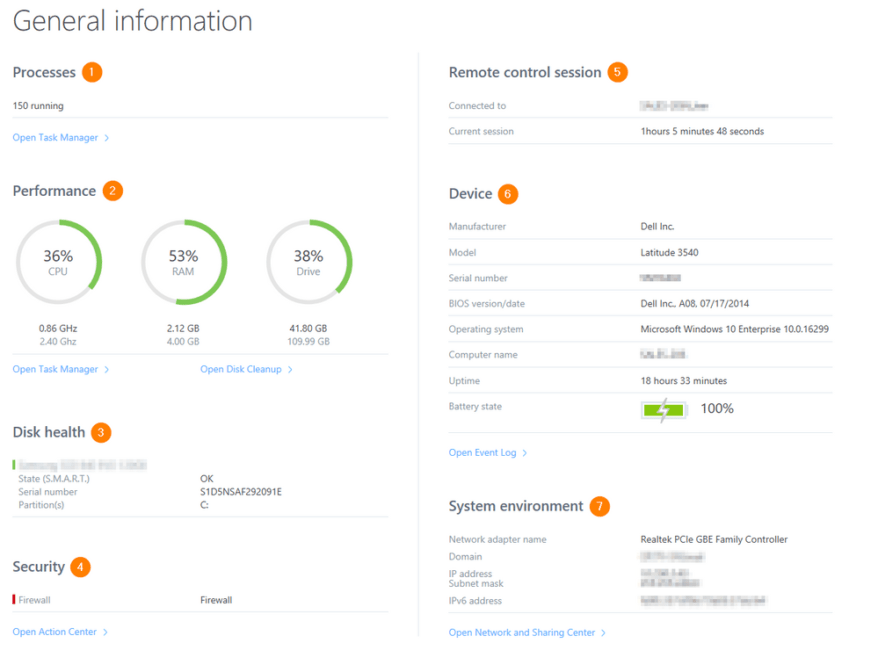
What is remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers.
How do I run remote access?
Here is how you can open Remote Desktop Connection with Run:Right-click Start or press Win + X to open the aptly-named WinX menu.Select Run on that menu.Type mstsc in the Open box.Click the OK button to open Remote Desktop Connection.
How do I run Task Manager remotely?
Another way to open the Task Manager on a remote computer is by right-clicking the taskbar and clicking “Task Manager” from the submenu.
What is remote task server?
A dedicated remote Task Server acts as an always-on, automated administrator. The Task Server installs packages and changes client settings without direct control from the Remote Desktop app.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Can you run Process Explorer remotely?
Remote Process Explorer is a Windows utility used to manage processes on a remote computer. This product utilizes built-in Windows (e.g. Remote Desktop, Computer and Service Management, network applications, etc.) and launches them from a single Graphical User Interface (GUI) console.
How can I monitor my remote computer performance?
More informationAt the command prompt, type the following command, and then press ENTER: Console Copy. monitor \\remotecomputer setup. ... To use the workspace file for logging, type the following command, and then press ENTER: Console Copy. monitor \\remotecomputer filename.
How do I get the task bar in Remote Desktop?
Sometimes, Windows Explorer has problems. This makes the taskbar not hidden in Remote Desktop sessions. To solve that, you need to restart Windows Explorer. -> Right-click on the taskbar and select the Task Manager option.
What is a task server?
The Task Server is an App Server that is used to process requests that have been spawned. Spawned requests can originate from the xdmp:spawn command or from a post-commit trigger action (for example, as the result of a document running through a pipeline in the Content Processing Framework).
How can I access someone else's computer remotely?
Chrome Remote Desktop is available on the web on your computer. To use your mobile device for remote access, you need to download the Chrome Remote Desktop app....Access a computer remotelyOn your Android phone or tablet, open the Chrome Remote Desktop app. ... Tap the computer you want to access from the list.More items...
How do I setup a remote access server?
Remote Desktop to Your Server From a Local Windows ComputerClick the Start button.Click Run...Type “mstsc” and press the Enter key.Next to Computer: type in the IP address of your server.Click Connect.If all goes well, you will see the Windows login prompt.
How can I remotely access another phone?
When you (or your customer) run the SOS app on the Android device it will display a session code that you will enter on your screen to remotely view that device. Users with devices running Android 8 or higher will be prompted to turn on accessibility in Android to allow remote access.
How do I access another computer on the same network?
Access other computersOpen File Explorer.In the Navigation pane on the left, click 'Network'.You will see all devices that are connected to the network. ... If prompted, enter the username and password that will grant you access to the system.You will see the Users folder and have access to select files.
Completing the migration
Migration is complete as soon as verification efforts demonstrate that the destination server has replaced the source server in serving the network.
Configuring firewall rules for VPN
Firewall rules that permit VPN network traffic are included with the Windows Firewall with Advanced Security, but they are disabled by default. The rules that enable the required inbound network traffic must be enabled on the destination server.
Configuring firewall rules for DirectAccess
When using additional firewalls in your deployment, apply the following Internet-facing firewall exceptions for Remote Access traffic when the Remote Access server is on the IPv4 Internet:
Restoring Remote Access in the event of migration failure
If migration of Remote Access to the destination server fails, you can put the source server back into operation by following these steps:
Retiring Remote Access on your source server
After you verify that the migration is complete, the source server can be disconnected from the network and removed from service. Stop RRAS before you remove the computer from the network and turn it off. You can keep this computer as a backup server in the event that you want to revert to your previous Routing and Remote Access configuration.
Troubleshooting cmdlet-based migration
The Windows Server Migration Tools deployment log file is located at % windir %\Logs\SmigDeploy.log. Additional Windows Server Migration Tools log files are created at the following locations.
Viewing the content of Windows Server Migration Tools result objects
All Windows Server Migration Tools cmdlets return results as objects. You can save result objects, and query them for more information about settings and data that were migrated. You can also use result objects as input for other Windows PowerShell commands and scripts.
How to access remote access server?
On the Remote Access server, open the Remote Access Management console: On the Start screen, type, type Remote Access Management Console, and then press ENTER. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
How to deploy DirectAccess for remote management only?
In the DirectAccess Client Setup Wizard, on the Deployment Scenario page , click Deploy DirectAccess for remote management only, and then click Next.
How to add roles and features to DirectAccess?
On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features.
How to install Remote Access on DirectAccess?
On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features. Click Next three times to get to the server role selection screen. On the Select Server Roles dialog, select Remote Access, and then click Next.
What group does DirectAccess belong to?
For a client computer to be provisioned to use DirectAccess, it must belong to the selected security group . After DirectAccess is configured, client computers in the security group are provisioned to receive the DirectAccess Group Policy Objects (GPOs) for remote management.
How to configure deployment type?
On the Remote Access server, open the Remote Access Management console: On the Start screen, type, type Remote Access Management Console, and then press ENTER. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
How to add domain suffix in remote access?
On the DNS Suffix Search List page, the Remote Access server automatically detects domain suffixes in the deployment. Use the Add and Remove buttons to create the list of domain suffixes that you want to use. To add a new domain suffix, in New Suffix, enter the suffix, and then click Add. Click Next.
What is task scheduler?
For scheduling and automatic execution of tasks in the Windows environment, the standard Task Scheduler tool is provided, which ensures that pre-prepared tasks are performed at a specific time, or when certain events occur, either once or at intervals, in the context of system or user accounts . In other words, using the Task Scheduler, you can schedule or perform a certain event, perform previously prepared actions, for example, check for updates, synchronize the clock on the time server when any user logs on, turn off or restart the computer, create a system restore point, etc. Starting from Windows Vista, Task Scheduler has become the main system maintenance tool, without which its normal operation is impossible. To manage scheduled tasks in a graphical user interface environment, the Microsoft Management Console (MMC) with the taskschd.msc module or the Schtask.exe command line utility can be used.
Do you need to have a login for a remote computer?
You must have the login credentials for the remote computer and the login credential must be part of the Administrators group on the remote computer .
Can you create new tasks on a remote PC?
You now have access to the Tasks Scheduler in the remote PC and are able to create new tasks or manipulate the existing tasks on the remote PC.
What is a remote access security policy manager?
Ensure a remote access security policy manager is used to manage the security policy on devices used for remote network connection or remote access.
Where is the remote user policy assessment/enforcement device installed?
The remote user policy assessment/enforcement device will be installed on a separate host from the authentication server. This device interacts directly with public networks and devices and...
What is managed device?
In this STIG, a managed device is defined as a device that has installed software (i.e. an agent) that allows the device to be managed and queried from a remote server. Thus, an unmanaged device...
What happens if a device fails a network policy assessment test?
If the device requesting remote network access fails the network policy assessment tests, then the policy server will communicate with the remote access device (e.g. , VPN gateway or RAS) to perform an approved action based on the requirements of this policy.
Where does device authentication take place?
Device authentication must be performed at the perimeter or on a subnet separated from the trusted internal enclave. User authentication ensures the user is authorized for access. However, user...
What happens if a client is incapable of employing critical security protections?
If the client is incapable of employing critical security protections then allowing access to that devices could expose the network to potentially significant risk.
Does the remediation server have access to other network resources?
Endpoints accessing the remediation server will not have access to other network resources that are not part of the remediation process.