How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
How to install Palo Alto on VirtualBox?
How to Install Palo Alto VM Firewall in VMWare
- Download Palo Alto Virtual Firewall. First of all, you have to download your virtual Palo Alto Firewall from your support portal. ...
- Download and Install VMWare Workstation. After downloading the Virtual Firewall image, you must have to download and install VMWare Workstation.
- Configuring your Virtual Network Interfaces. ...
How to configure IPSec VPN on Palo Alto firewall?
Steps to configure IPSec Tunnel in FortiGate Firewall
- Creating IPSec Tunnel in FortiGate Firewall – VPN Setup. ...
- IPSec Tunnel Phase 1 & Phase 2 configuration. ...
- Configuring Static Route for IPSec Tunnel. ...
- Configuring the Security Policy for IPSec Tunnel. ...
- Finally Initiating the tunnel and verify the configuration. ...
How to configure Palo Alto Networks?
Configure the Palo Alto Networks Terminal Services Agent for User Mapping. Retrieve User Mappings from a Terminal Server Using the PAN-OS XML API. Send User Mappings to User-ID Using the XML API. Enable User- and Group-Based Policy. Enable Policy for Users with Multiple Accounts.

How do I create a VPN user in Palo Alto firewall?
Enter a name and then choose a “Type” of “Local Database.” Under the “Advanced” tab, choose the users you want to allow. Alternatively, you can choose “All” from the list as well, to allow all users from the local database to be granted VPN access. Network -> GlobalProtect -> Gateways -> Click “Add.”
How do I set up GlobalProtect VPN?
SET UP GLOBALPROTECT VPN FOR ANDROIDGo to the Google Play store on your device and search for GlobalProtect. ... Once installed, tap Open.Once the app is opened, GlobalProtect will prompt you for a portal. ... Next, you will be prompted for your Marquette username (e.g., eagleg — and not email address) and password.More items...
How configure GlobalProtect Palo Alto?
To implement GlobalProtect, configure:GlobalProtect client downloaded and activated on the Palo Alto Networks firewall.Portal Configuration.Gateway Configuration.Routing between the trust zones and GlobalProtect clients (and in some cases, between the GlobalProtect clients and the untrusted zones)More items...•
Can GlobalProtect portal page be configured to be accessed on any port?
Although it is not possible to change the port GlobalProtect uses, it is possible to use another port with help from a loopback IP address and security rules.
How does Palo Alto VPN Work?
When connected to a VPN, a device will behave as if it's on the same local network as the VPN. The VPN will forward device traffic to and from the intended website or network through its secure connection. This allows remote users and offices to connect securely to a corporate network or website.
What is GlobalProtect in Palo Alto?
GlobalProtect™ network security client for endpoints, from Palo Alto Networks®, enables organizations to protect the mobile workforce by extending the Next-Generation Security Platform to all users, regardless of location.
How does GlobalProtect choose Gateway?
Gateway Selection Algorithm When multiple gateways are listed in the portal, the client will automatically connect to the preferred gateway. The clients use priority and response time as a factor to determine the best gateway.
How does GlobalProtect VPN Work?
Your VPN enables a secure connection between your computer and resources on your Relativity instance's network. The following resources are available when you connect to the GlobalProtect VPN client: Utility Server VM via Windows Remote Desktop Connection (RDP) Direct access to SQL.
Does Palo Alto support SSL VPN?
Palo Alto Networks' devices provide an integrated SSL VPN service.
How do I configure GlobalProtect client to get the same IP address?
From the WebGUI, Go to Network > GlobalProtect > Gateways and edit the appropriate Gateway. Go to Agent > Client Settings > and edit the appropriate Client Config. Go to the IP Pools tab. The GlobalProtect user will be offered the first IP address that is defined in the pool of IP addresses.
What protocol does GlobalProtect VPN use?
IPsec/SSL VPNLaptops, smartphones, and tablets with the GlobalProtect app automatically establish a secure IPsec/SSL VPN connection to the next-generation firewall using the best gateway, thus providing the organization with full visibility of all network traffic, applications, ports, and protocols.
Is GlobalProtect SSL or IPsec?
GlobalProtect is slower on SSL VPN because SSL requires more overhead than IPSec. Also, Transmission Control Protocol (TCP) is more prone to latency than User Datagram Protocol (UDP), which is used in IPsec GlobalProtect. Hope this helps.
How do I find my GlobalProtect password?
How to Reset Your GlobalProtect VPN Password After a Password...In the system tray, double-click on the GlobalProtect icon. ... If your credentials are stored/saved, your username will be shown in the top right corner. ... To clear your credentials, simply click on the Sign Out button next to your username.More items...•
How does GlobalProtect VPN Work?
In order to protect network traffic, GlobalProtect Gateway provides IPsec and SSL VPN connections to mobile devices using GlobalProtect App. The VPN connection maintains network privacy even when the mobile device is being used in public locations such as hotels, conference halls and coffee shops.
How do I add a user to GlobalProtect?
Device -> Authentication Profile -> Click “Add.” Enter a name and then I choose a “Type” of “Local Database.” Under the “Advanced” tab, choose the users you want to allow. Alternatively, you can choose “All” from the list as well, to allow all users from the local database to be granted VPN access.
How do I connect my GlobalProtect VPN to my Mac?
Install and Connect to the GlobalProtect VPN on a MacClick the Download Mac 32/64-bit GlobalProtect agent link to download the installer to your computer.Click Allow if prompted.Open the GlobalProtect file.Click Continue.Click Continue and then click Continue again.Click Install.More items...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
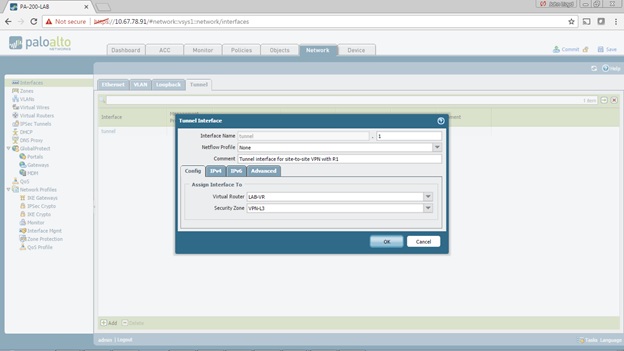
Step 1
NOTE: If the tunnel interface is in a zone different from the zone where the traffic will originate or depart, then a policy is required to allow the traffic to flow from the source zone to the zone containing the tunnel interface.
Step 2
Go to Network > Network Profiles > IKE Crypto , click Add and define the IKE Crypto profile (IKEv1 Phase-1) parameters. Name does not matter, can be whatever you like. These parameters should match on the remote firewall for the IKE Phase-1 negotiation to be successful.
Step 3
Go to Network > Network Profiles > IKE Gateway to configure the IKE Phase-1 Gateway.
Step 4
Under Network > Network Profiles > IPSec Crypto , click Add to create a new Profile, define the IPSec Crypto profile to specify protocols and algorithms for identification, authentication, and encryption in VPN tunnels based on IPSec SA negotiation (IKEv1 Phase-2).
Step 5
Under Network > IPSec Tunnels, click Add to create a new IPSec Tunnel. In the General window use the Tunnel Interface, the IKE Gateway and IPSec Crypto Profile from above to set up the parameters to establish IPSec VPN tunnels between firewalls.
Step 6
Under Network > Virtual Routers, click on your Virtual router profile, then click Static Routes, add a new route for the network that is behind the other VPN endpoint. Be sure to use the proper Tunnel Interface. Click OK when done.
Step 7
Allow ike negotiation and ipsec/esp packets. By default the ike negotiation and ipsec/esp packets would be allowed via the intrazone default allow.