In the Palo Alto application, click Policies > Security > Add. Create firewalls rules to allow inbound traffic from the internet to the external IP address of the firewall. This rule should allow IPSec.
Full Answer
How do I monitor a Palo Alto Networks IPsec tunnel?
On the IPSec tunnel, enable monitoring with action failover if configuring the tunnels to connect to anther Palo Alto Networks firewall. Otherwise, set up the PBF with monitoring and a route for the secondary tunnel. Tunnel Monitoring (Palo Alto Networks firewall connection to another Palo Alto Networks firewall) Primary tunnel with monitoring.
How to configure Palo Alto firewall with VPN?
In our case, we will be using two (2) Palo Alto firewall. Go to Network >> Zones and click Add. Now add the zone name as VPN and Type of the zone Layer3. And, then click OK. Go to Network >> Interface >> Tunnel and click Add to add a new tunnel. A pop-up will open, add Interface Name, Virtual Router, Security Zone, IPv4 address.
How to configure Cisco ASA to work with Palo Alto Networks?
When working with a Cisco ASA, make sure it knows how to return traffic to 172.16.0.1/30. Additionally, configure a Proxy ID for this network on the Palo Alto Networks device's IPSec tunnel configuration.
How do I set up an IPSEC tunnel for my service?
Use the following steps to set up an IPSec tunnel for your service connection. The first tunnel you create is the primary tunnel for the service connection. You can then repeat this workflow to optionally set up a secondary tunnel. When both tunnels are up, the primary tunnel takes priority over the secondary tunnel.

Does remote access VPN use IPSec?
While Remote access VPN supports SSL and IPsec technology.
How do I access my Palo Alto firewall remotely?
Go to Network > Interfaces > Ethernet, then click on the Interface name, for the external interface. I used ethernet1/3. Click the Advanced tab. Under the Other Info tab, next to Management Profile, use the dropdown to select Remote_management, then click OK.
What is IPSec remote access?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
How do I initiate IPSec tunnel in Palo Alto?
- Knowledge Base - Palo Alto Networks....OverviewInitiate VPN ike phase1 and phase2 SA manually. ... Check ike phase1 status (in case of ikev1) ... To check if phase 2 ipsec tunnel is up: ... Check Encryption and Decryption (encap/decap) across tunnel. ... Clear The following commands will tear down the VPN tunnel:
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Which type of remote access functions as a secure tunnel through any network?
A VPN creates a “tunnel” that passes traffic privately between the remote network and the user. The tunnel protects the traffic and keeps it safe from being intercepted or tampered with. VPNs are commonly implemented using the protocols IPsec or SSL.
What is the difference between VPN and IPsec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Is IPsec faster than SSL?
In short: Both are reasonably fast, but IKEv2/IPSec negotiates connections the fastest. Most IPSec-based VPN protocols take longer to negotiate a connection than SSL-based protocols, but this isn't the case with IKEv2/IPSec.
Is IPsec more secure than SSL?
Security and convenience are two key factors to consider. Because IPsec requires third-party client software, it is more complicated and expensive to set up and maintain. However, this also makes it more secure.
How do I configure IPsec tunnel?
Preshared key authenticationIn the administration interface, go to Interfaces.Click Add > VPN Tunnel.Type a name of the new tunnel.Set the tunnel as active and type the hostname of the remote endpoint. ... Select Type: IPsec.Select Preshared key and type the key.More items...
How IPsec VPN works step by step?
Authenticates and protects the identities of the IPSec peers. Negotiates a matching IKE SA policy between peers to protect the IKE exchange. Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys. Sets up a secure tunnel to negotiate IKE phase two parameters.
How do I enable IPsec?
How do I enable IPSec on a machine?Right click on 'My Network Places' and select Properties.Right click on 'Local Area Connection' and select Properties.Select 'Internet Protocol (TCP/IP)' and click Properties.Click the Advanced button.Select the Options tab.Select 'IP security' and click Properties.More items...
How do I log into my Palo Alto firewall command line?
Access the CLILaunch the terminal emulation software and select the type of connection (Serial or SSH). ... When prompted to log in, enter your administrative username. ... Enter the administrative password.
How do I configure my Palo Alto firewall interface?
1:576:17Configuring Ethernet interfaces on Palo Alto - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo let's go ahead and configure our first interface. Just going to click on where says Ethernet 1 1.MoreSo let's go ahead and configure our first interface. Just going to click on where says Ethernet 1 1. In your face name. Yeah not a problem interface type I want to change this to layer.
What is Palo Alto virtual wire?
The V-Wire deployment options overcome the limitations of TAP mode deployment, as engineers are able to monitor and control traffic traversing the link. A Virtual Wire interface supports App-ID, User-ID, Content-ID, NAT and decryption.
How do I open ports on a Palo Alto firewall?
StepsNavigate to Objects > Services.Click on Add to bring up the Service dialog.Configure the new service with values for Name, Protocol and Destination Port range.
What is remote access?
Remote access allows end users to access resources on the corporate network from a distant location. The most common function of remote access is to enable employees who are traveling or telecommuting to connect to the company network and access resources such as internal applications, intranet, mail services, and file sharing.
What is the primary method of remote access?
Virtual Private Networks. The predominant method of providing remote access is via a Virtual Private Network (VPN) connection. Normally, a user has no expectation of privacy on a public network, as their network traffic is viewable by other users and system administrators.
What is the difference between SSL VPN and IPsec?
Both are in popular use, but the main difference is the layer of network traffic it secures. An IPsec connection requires client software (provided by a third party or by the operating system), whereas an SSL VPN connection can be accessed through a web browser.
How does a VPN work?
A VPN creates a “tunnel” that passes traffic privately between the remote network and the user. The tunnel protects the traffic and keeps it safe from being intercepted or tampered with. VPNs are commonly implemented using the protocols IPsec or SSL. Both are in popular use, but the main difference is the layer of network traffic it secures.
What is proxy based portal?
Proxy-based portals require remote users to connect to an intermediary server (the SSL Portal VPN) where they are granted access to applications and resources permitted from the network administrators.
What is emerging model of remote access?
An emerging model of remote access provides the benefit of a tunnel for broad application support while retaining strong control over access to applications through the next-generation firewall security policy. This approach allows administrators to safely enable remote user activity and access on the network. Combining the benefits from earlier implementations, this model is the most secure and practical remote access solution available today.
Does SSL VPN use client software?
However, due to the growing complexity of running code in a web browser and the diversity of browser platforms, many SSL VPN products now use client software as well. SSL VPNs may also provide remote access through a proxy. Proxy-based portals require remote users to connect to an intermediary server ...
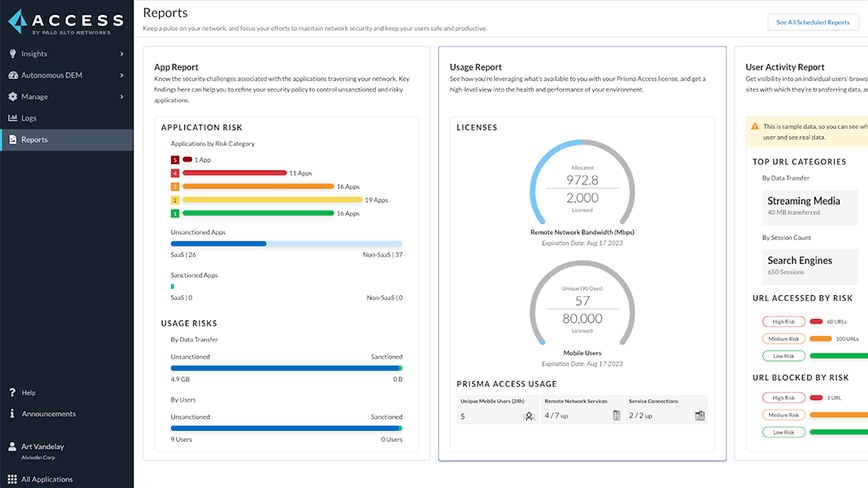
What is Prisma Access?
Based on the IPSec device type you selected, Prisma Access provides a recommended set of IPSec protocol and key lifetime settings to secure data within the IPSec tunnel between your branch device and Prisma Access in IKE Phase 2 for the Security Association (SA). You can use the recommended settings, or customize the settings as needed for your environment.
How to add a VPN tunnel?
Add Primary and Secondary IPSec VPN Tunnels 1 Give the tunnel a descriptive#N#Name#N#. 2 Select the#N#Branch Device Type#N#for the IPSec device at the remote network site that you’re using to establish the tunnel with Prisma Access. 3 For the#N#Branch Device IP Address#N#, choose to use either a#N#Static IP#N#address that identifies the tunnel endpoint or a#N#Dynamic#N#IP address.#N#If you set the#N#Branch Device IP Address#N#to#N#Dynamic#N#, you must also add the IKE ID for the remote network site (#N#IKE Local Identification#N#) or for Prisma Access (#N#IKE Peer Identification#N#) to enable the IPSec peers to authenticate.#N#Because you do not have the values to use for the Prisma Access IKE ID (#N#IKE Peer Identification#N#) until the remote network is fully deployed, you would typically want to set the IKE ID for the remote network site (#N#IKE Local Identification#N#) rather than the Prisma Access IKE ID.
What is the authentication algorithm for Prisma Access?
Prisma Access supports the following authentication algorithms: sha1 (160 bits), sha256 (256 bits), sha384 (384 bits), sha512 (512 bits), and md5 (128 bits). You can also select null (no authentication).
Does Prisma Access initiate IKE connections?
so that Prisma Access only response to IKE connections and does not initiate them.
Does Prisma Access have IKE?
Based on the IPSec device you use to establish the tunnel at the remote network site, Prisma Access provides built-in, recommended IKE and IPSec security settings. You can use the recommended settings to get started quickly, or customize them as needed for your environment.
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
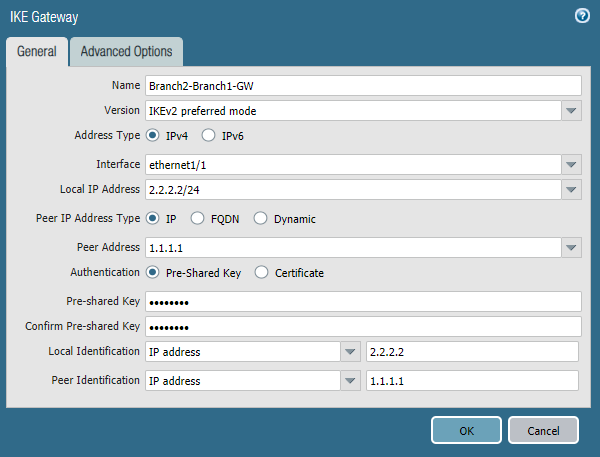
How to create IPSec tunnel?
Under Network > IPSec Tunnels, click Add to create a new IPSec Tunnel. In the General window use the Tunnel Interface, the IKE Gateway and IPSec Crypto Profile from above to set up the parameters to establish IPSec VPN tunnels between firewalls.
How to add IPSec crypto to VPN?
Under Network > Network Profiles > IPSec Crypto , click Add to create a new Profile, define the IPSec Crypto profile to specify protocols and algorithms for identification, authentication, and encryption in VPN tunnels based on IPSec SA negotiation (IKEv1 Phase-2). These parameters should match on the remote firewall for the IKE Phase-2 negotiation to be successful.
How to add IKE crypto profile?
Go to Network > Network Profiles > IKE Crypto , click Add and define the IKE Crypto profile (IKEv1 Phase-1) parameters. Name does not matter, can be whatever you like. These parameters should match on the remote firewall for the IKE Phase-1 negotiation to be successful.
When configuring an IPSec tunnel, what is the proxy-ID configuration?
When configuring an IPSec Tunnel Proxy-ID configuration to identify local and remote IP networks for traffic that is NATed, the Proxy-ID configuration for the IPSec Tunnel must be configured with the Post-NAT IP network information, because the Proxy-ID information defines the networks that will be allowed through the tunnel on both sides for the IPSec configuration.
What is passive mode in firewall?
Enable Passive Mode - The firewall to be in responder only mode. The firewall will only respond to IKE connections and never initiate them.
Does Palo Alto Networks support IPSec?
NOTE: The Palo Alto Networks supports only tunnel mode for IPSec VPN. The transport mode is not supported for IPSec VPN.
What is remote work AP?
In a home office scenario, the Remote Workplace AP is cloud-managed and it forms an IPSec tunnel to the corporate data center (CDC). CDC is the head end tunnel terminator. The Remote Workplace AP uses 802.1X authentication such as Pre-Shared Key or Captive Portal to authenticate clients.
What is a full tunnel AP?
In a full tunnel mode, the Remote Workplace AP sends all data traffic to the CDC. The CDC processes the data using existing corporate security tools.
What is source zone?
Source zone is the zone that you have created in the Create a VPN Zone section and the destination zone is the zone where you have the resources in CDC. Note: Ensure that your firewall rule allows access to the DNS servers that will be responsible for resolving internal DNS names.
Is a wildcard SSL certificate valid?
You have a valid or publicly signed SSL certificate. Wildcard SSL certificates are also acceptable.
What IP address is Sitea to Siteb?
We need to add routes to reach SITEA to SITEB and vise-versa. Below are the route from SITEA to SITEB, where gateway is IPSec peer IP , which is 10.10.10.2
How to add IKE crypto to network?
Go to Network >> Network Profile >> IKE Crypto and click Add. Now add below details-
Can we reach SiteB from SiteA?
We can successfully reach SiteB from SiteA. Let’s verify IPSec information from palo alto using below command-
How many routes are there in a VPN tunnel?
With this method, using tunnel monitoring there are two routes in the routing table, the first with metric of 10 for the Primary VPN traffic, and the second with the metric of 20 for the Secondary VPN. Since the tunnels terminate on the Secondary VR, the routes will be placed on that VR.
Why is PBF disabled?
When the PBF is disabled, because the destination is not reachable, the other VPN will start using the routing table with a route that has the same destination but is using the other configured tunnel. Note: In the above example, a probe is sent out to 192.168.10.2 to check if it's reachable.
What is a high availability device?
A single device with two internet connections (High Availability)
Does each VR have an ISP?
Each VR has an ISP Interface attached, but all other interfaces will stay connected to VR Secondary, as well as all future interfaces. The purpose is to let all interfaces be known by connected routes and routes on the VR as their routing method when the Main ISP goes down.
Does PBF forward traffic?
The firewall tells the PBF not to forward traffic destined to a private network, since it cannot route private addresses on the Internet (as there might be private network addresses that need to be forwarded out). Click Negate.