FortiGuard Labs is aware of a report that a new Remote Access Trojan (RAT) called "Woody" has been lurking in the wild for the past year. Reported initial infection vectors include email attachments as well as Microsoft Word documents that leverage the recently patched Follina vulnerability (CVE-2022-30190).
Full Answer
What is a remote access trojan (RAT)?
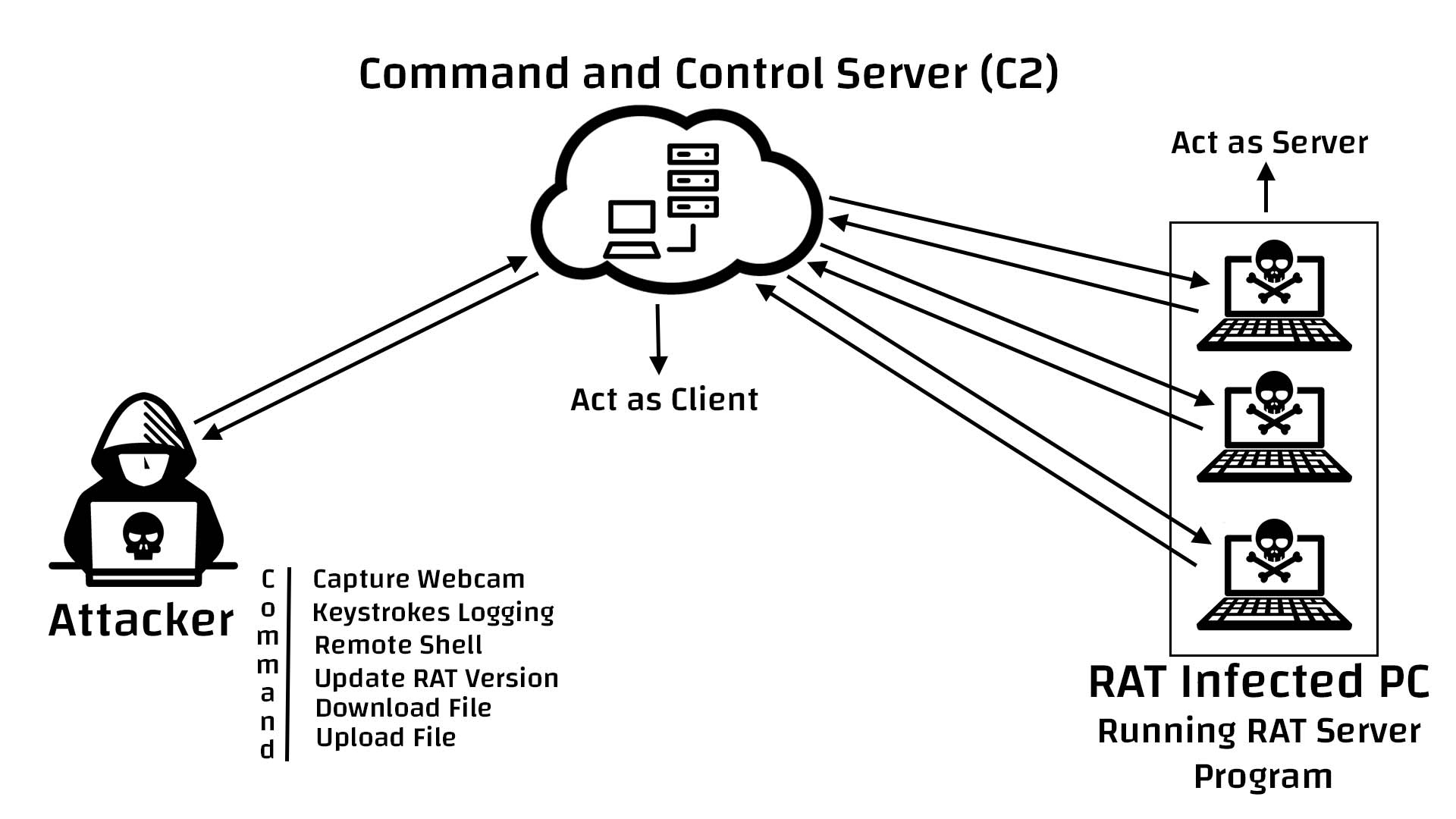
What Is a RAT Virus? A remote access trojan (RAT), also called creepware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim.
What is remote access toolkit malware?
This type of malware is designed to allow a hacker to remotely control a target machine, providing a level of access similar to that a remote system administrator. In fact, some RATs are derived from or based upon legitimate remote administration toolkits.
What are the CPU and RAM usage of the Trojan?
Besides, the Trojan creates several processes on startup and is visible in the Task Manager. The consumption rate is 0.1% CPU and 4.2 MB RAM. Drive load is 100 kbps.
How powerful is Cybergate Trojan?
Besides, the Trojan creates several processes on startup and is visible in the Task Manager. The consumption rate is 0.1% CPU and 4.2 MB RAM. Drive load is 100 kbps. Cybergate does not seem to care about shielding itself. The build does not even try to hide an exceptionally large number of libraries and functions.

Can a Trojan give remote access?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What are the variant of remote access Trojan?
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Can Norton detect RATs?
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton, can detect RATs and other types of malware if they infect your devices.
Which is the best remote access Trojan?
Blackshades is a Trojan which is widely used by hackers to gain access to any system remotely. This tool frequently attacks the Windows-based operating system for access.
What are the main features of a remote access Trojan?
RAT (remote access Trojan)Monitoring user behavior through keyloggers or other spyware.Accessing confidential information, such as credit card and social security numbers.Activating a system's webcam and recording video.Taking screenshots.Distributing viruses and other malware.Formatting drives.More items...
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
How do I know if someone is accessing my computer remotely?
You can try any of these for confirmation.Way 1: Disconnect Your Computer From the Internet.Way 2. ... Way 3: Check Your Browser History on The Computer.Way 4: Check Recently Modified Files.Way 5: Check Your computer's Login Events.Way 6: Use the Task Manager to Detect Remote Access.Way 7: Check Your Firewall Settings.More items...•
What do Trojan creators look for?
Explanation: Trojan creators do not look for securing victim's system with their programs, rather they create such trojans for stealing credit card and financial details as well as important documents and files.
Does Norton remove Trojans?
Resolution. Norton Antivirus detects and removes Trojan horses. Via LiveUpdate, administrators can download to a computer the latest virus definitions, which contain information that the scan engine needs to find existing and emerging threats on a system.
Can antivirus detect Trojan?
An effective antivirus program searches for valid trust and app behavior, as well as trojan signatures in files in order to detect, isolate and then promptly remove them.
Does Norton clean malware?
Yes, Norton 360 provides anti malware protection. It protects against computer viruses, spam, social dangers, phishing, identity theft, and other online born threats.
What is a backdoor Trojan?
Backdoor malware is generally classified as a Trojan. A Trojan is a malicious computer program pretending to be something it's not for the purposes of delivering malware, stealing data, or opening up a backdoor on your system.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
What is data sending Trojan?
A data-sending Trojan is a kind of Trojan virus that relays sensitive information back to its owner. This type of Trojan can be used to retrieve sensitive data, including credit card information, email addresses, passwords, instant messaging contact lists, log files and so on.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What is the new Trojan?
The new 'Abaddon' remote access trojan may be the first to use Discord as a full-fledged command and control server that instructs the malware on what tasks to perform on an infected PC. Even worse, a ransomware feature is being developed for the malware.
What is the new piece of malware that shows no similarities with samples used in known campaigns?
Researchers named the threat Milum and dubbed the operation WildPressure.
What is a RAT in pysa?
The PYSA ransomware gang has been using a remote access Trojan (RAT) dubbed ChaChi to backdoor the systems of healthcare and education organizations and steal data that later gets leveraged in double extortion ransom schemes.
Why are remote access Trojans important?
Remote Access Trojans fulfill an important function for hackers. Most attack vectors, like phishing, are ideal for delivering a payload to a machine but don’t provide the hacker with the ability to explore and interact with the target environment. RATs are designed to create a foothold on the target machine that provides the hacker with the necessary level of control over their target machine.
What is the next step in a phishing attack?
Once a hacker has gained initial access to a target machine, expanding and solidifying that foothold is the next logical step. In the case of a phishing attack, this involves using malware to take advantage of the access provided by the email.
What is ICS malware?
Malware targeting industrial control systems (ICS) is nothing new, with big names like Stuxnet and Industroyer designed to cause physical damage. However, some ICS-focused malware is targeted at controlling critical infrastructure.
Is Androrat still used?
Despite the age of the source code (last update in 2014), AndroRAT continues to be used by hackers. It includes the ability to inject its malicious code into legitimate applications, making it easy for a hacker to release a new malicious app carrying the RAT.
Do remote access Trojans exist?
Many different Remote Access Trojans exist, and some hackers will modify existing ones or develop their own to be better suited to their preferences. Different RATs are also designed for different purposes, especially with RATs geared specifically to each potential target (desktop versus mobile, Windows versus Apple and so on).
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
What happens if you remove the internet from your computer?
Removing the Internet connection from the device disables remote access to your system by an attacker. After the device can no longer connect to the Internet, use your installed anti-malware program to remove it from local storage and memory. Unless you have monitoring configured on your computer, you won't know which data and files transferred to an attacker. You should always change passwords across all accounts, especially financial accounts, after removing malware from your system.
Can malware writers name processes?
For most applications and processes, you can identify any suspicious content in this window, but malware writers name processes to make them look official. If you find any suspicious executables and processes, search online to determine if the process could be a RAT or other type of malware.
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.
Can an attacker record video?
The attacker can activate the webcam, or they can record video.
