How to connect to Kibana with security onion?
SGUIL_CLIENT_PASSWORD_1 will be the password to use to connect to security onion Your machine will reboot once, and after a few minutes, it should be ready to use... By default the integrated firewall will block all incoming connections. To allow remote connections to Kibana you must type sudo so-allow and select a in the menu.
What are the security features in Kibana?
For example, some users might only need to view your stunning dashboards, while others might need to manage your fleet of Elastic agents and run machine learning jobs to detect anomalous behavior in your network. This guide introduces you to three of Kibana’s security features: spaces, roles, and users.
How do I configure Kibana to work with remote users?
You need to configure the file /etc/kibana/kibana.yml as root: Uncomment the lines: # Kibana is served by a back end server. This setting specifies the port to use. server.port: 5601 # To allow connections from remote users, set this parameter to a non-loopback address. server.host: "0.0.0.0"
How do I enable or disable elastic features in Kibana?
If you had previously enabled Elastic Features and then upgrade to Security Onion 2.3.40 or higher, you may notice some features missing in Kibana. You can enable or disable features as necessary by clicking the main menu in the upper left corner, then click Stack Management, then click Spaces, then click Default.
How do I access Kibana remotely?
To remotely connect to Kibana, set server. host to a non-loopback address....Log on to the web applicationeditLog on to your account.Go to the home page, then click Kibana.To make the Kibana page your landing page, click Make this my landing page.
How do you use Onion security?
Installation using Security Onion ISO Image Review the Hardware Requirements and Release Notes sections. Download and verify our Security Onion ISO image. Boot the ISO in a machine that meets the minimum hardware specs. Follow the prompts to complete the installation and reboot.
How do you start Kibana in security Onion?
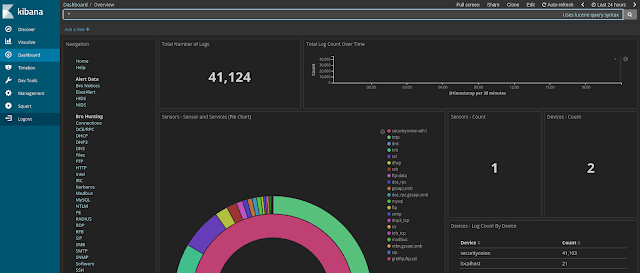
Dashboards. Once you log into Kibana, you should start on the Security Onion - Home dashboard. Notice the visualization in the upper left is labeled Security Onion - Navigation . This navigation panel contains links to other dashboards and will change depending on what dashboard you're currently looking at.
What is Kibana security Onion?
Security Onion supports Elastic authentication. This means that you will authenticate to Elasticsearch and Kibana using the same username and password that you use for Security Onion Console (SOC).
Is security onion a good tool?
Security Onion is one of the best Linux distribution with get to ready security tools for network and security analysis. It is user friendly, easy installation on single click but lacks in issue of trust with production environment.
Is security onion free?
Security Onion is a free and open source intrusion detection system (IDS), security monitoring, and log management solution.
How do you start a security Onion?
Installation using Security Onion ISO Image Review the Hardware Requirements and Release Notes sections. Download and verify our Security Onion ISO image. Boot the ISO in a machine that meets the minimum hardware specs. Follow the prompts to complete the installation and reboot.
What port does security onion use?
8080 (Osquery, if enabled)
What is security onion Siem?
Security onion is an open-source that does the intrusion detection system (IDS), log management solution, monitoring, etc. It also helps to peel back the security layers of your enterprise. It has many security tools, including Fleet, CyberChef, Playbook, TheHiva, Kibana, Suricata, Elasticsearch, and much more.
What does security onion use for full packet capture?
Security Onion Console (SOC) gives you access to our PCAP interface. This interface allows you to access your full packet capture that was recorded by Stenographer. In most cases, you'll pivot to PCAP from a particular event in Alerts, Dashboards, or Hunt by choosing the PCAP action on the action menu.
Can you run security onion on Raspberry Pi?
Introduction. Over the last few years, many folks have asked if they could run Security Onion on a Raspberry Pi. The answer is no, for two main reasons: The Raspberry Pi has an ARM processor and we do not compile Security Onion for ARM.
What is Kibana tool?
Kibana is a data visualization and exploration tool used for log and time-series analytics, application monitoring, and operational intelligence use cases. It offers powerful and easy-to-use features such as histograms, line graphs, pie charts, heat maps, and built-in geospatial support.
What companies use security Onion?
Companies Currently Using Security OnionCompany NameWebsiteRevenue (USD)Carnegie Mellon Universitycmu.eduOver $1,000,000,000Stratus Solutionsapplied-insight.comFrom $100,000,000 to $199,999,999Applied Insightappliedinsight.netFrom $1,000,000 to $9,999,999Kingland Systemskingland.comFrom $10,000,000 to $49,999,9992 more rows
How do you snort on security Onion?
0:4731:26Snort IDS Tutorial on Security Onion 101 - YouTubeYouTubeStart of suggested clipEnd of suggested clipClick on yes and from here I can figure it in network interfaces now I'm to skip that. And click onMoreClick on yes and from here I can figure it in network interfaces now I'm to skip that. And click on kids. It's it's alarming you--be about the password I sort of the RAM.
What is onion model in security in computing?
The onion model in computing is used as a metaphor for the complex structure of information systems. The system is split into layers to make it easier to understand. A simple example is to start with the program, operating system and hardware layers. Each of these layers can then be subdivided.
What is security Onion Siem?
Security onion is an open-source that does the intrusion detection system (IDS), log management solution, monitoring, etc. It also helps to peel back the security layers of your enterprise. It has many security tools, including Fleet, CyberChef, Playbook, TheHiva, Kibana, Suricata, Elasticsearch, and much more.
How to grant access to Kibana dashboard?
To grant access to dashboards in the Marketing space, locate the Kibana section, and click Add Kibana privilege: From the Spaces dropdown, select the Marketing space. Expand the Analytics section, and select the Read privilege for Dashboard . Click Add Kibana privilege . Click Create role.
What are the three security features of Kibana?
This guide introduces you to three of Kibana’s security features: spaces, roles, and users . By the end of this tutorial, you will learn how to manage these entities, and how you can leverage them to secure access to both Kibana and your data.
Why is Kibana important?
Kibana is home to an ever-growing suite of powerful features, which help you get the most out of your data. Your data is important, and should be protected. Kibana allows you to secure access to your data and control how users are able to interact with your data.
What is a role in Kibana?
Roles are a collection of privileges that allow you to perform actions in Kibana and Elasticsearch. Roles are assigned to users, and to system accounts that power the Elastic Stack. You can create your own roles, or use any of the built-in roles.
What is a Kibana space?
A space allows you to organize your dashboards, alerts, machine learning jobs, and much more into their own categories. For example, you might have a Marketing space for your marketeers to track the results of their campaigns, and an Engineering space for your developers to monitor application performance.
Can you create your own roles in Elastic Stack?
You can create your own roles, or use any of the built-in roles. Some built-in roles are intended for Elastic Stack components and should not be assigned to end users directly.
How to allow remote connections to Kibana?
By default the integrated firewall will block all incoming connections. To allow remote connections to Kibana you must type sudo so-allow and select a in the menu.
What is security onion?
Security Onion is a great tool that combines full packet capture, intrusion detection (snort and bro) and the elasticsearch-logstash-kibana (ELK) stack to store and visualize your security data. Let's see how to get started...
What is Kibana dashboard?
Kibana has multiple tabs on the left side. The main one is the dashboard , it show you statistics about your system: how many events are received, from wich ip's etc.
Which port should a sniffing interface be connected to?
The sniffing interface will receive the network traffic that has to be analyzed, so it should be connected to the 'mirroring' port of a switch.
Where are packet captures saved?
Packet captures (pcap files) are saved in /nsm/sensor_data/<hostname>-<interface>/dailylogs. They can also be visualized using the web app CapME.
Can you create a graph in Security Onion?
Once again, Security onion provides a lot of predefined graphs. You can also create your own graph, based on the search query that you saved previously...