How to install a keylogger remotely for free?
- First, you will have to execute the setup of the Ardamax tool of the key logger on your computer device after license key activation. ...
- Once you reach over there, click on the option of Remote installation from the download menu. ...
- When the above action is completed, another window will trigger with the options of invisibility. ...
How to install a keylogger remotely by the email?
Highster Mobile – Remote Installation Keylogger for iPhone
- Upload it to Google Drive
- Upload it to DropBox
- Send it in a messaging application
- Send it to yourself in an e-mail
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
Can a keylogger be installed remotely?
iSafe Remote Install Keylogger is one of the stealthiest keyloggers available which can be remotely installed to any remote target computer without needing the physical access to them in a totally stealthy mode.

What is remote keylogger?
A keylogger, sometimes called a keystroke logger or keyboard capture, is a type of surveillance technology used to monitor and record each keystroke on a specific computer. Keylogger software is also available for use on smartphones, such as the Apple iPhone and Android devices.
Does keylogger work on remote desktop?
If the keylogger is only listening to any hardware devices that identify as a "keyboard" for their keystrokes, then no. It would not capture your remote keystrokes regardless of what you typed in through that remote-access software as it would be looking for input from that specific class of hardware device.
Does Teamviewer have a keylogger?
Yes, if there is monitoring software (for example a keystroke logger) enabled on the remote machine. Teamviewer indicates they secure their connections client to client.
Can a keylogger be installed just by visiting a website?
Once you visit an infected website, a keylogger can get onto your computer in a matter of seconds, installing itself in the background.
Can keyloggers detect copy paste?
The short answer is "yes", you are at risk. On a related note: not all Keyloggers are limited to monitoring input from the keyboard (they also monitor clipboard activity [cut and paste], desktop activity, instant messaging, emails, etc).
What is ardamax keylogger?
Ardamax Keylogger is a lite program that captures all activity of anyone using your computer and logs all keystrokes. It's a kind of program commonly used by some enterprises to know what the staff does when working, now you can use it at home and control your children, friends and family.
Can people hack computer through TeamViewer?
If you are using TeamViewer, then beware and make sure you're running the latest version of the popular remote desktop connection software for Windows.
Can TeamViewer track activity?
Built-in reporting log captures all remote session activities and management console actions: who did what, when, and for how long for every incoming and outgoing connection. Critical for security purposes, these audit logs can only be viewed by designated IT admins with appropriate user permissions.
How can I use TeamViewer without the other person knowing?
You have to set a personal password on the other computer, so you can access the computer without your partner having to do anything. Open Teamviewer, then click on "Menu" and then on "Options". A windows should pop up. Now you have to click on "Securtiy".
Can I get keylogger without downloading anything?
Conclusion. There are numerous ways to get a keylogger installed on your device without you even realizing it. Hackers are improvising their methods and using several software programs to attack the users. So, there are chances of getting a keylogger simply by visiting a website if it contains a malware program.
How do hackers install keyloggers?
Keyloggers can be installed through webpage script. This is done by exploiting a vulnerable browser and the keystroke logging is launched when the user visits the malicious website. a keylogger can exploit an infected system and is sometimes capable to download and install other malware to the system.
Can you get a Trojan from visiting a website?
Yes, you can get a virus or malware on a phone by visiting a website. Hackers have been known to embed malicious code, predominately spyware, into compromised websites. This code is designed to attack vulnerabilities in the mobile browser and the underlying operating system, such as iOS.
Can RDP be hacked?
RDP has become a common way for hackers to steal valuable information from devices and networks. It is specifically vulnerable because of its ubiquity. Since so many businesses use it, the odds accessing an improperly secured network are higher and hackers have a better chance of breaking through.
How does the keylogger app work?
A software keylogger is put on a computer when the user downloads an infected application. Once installed, the keylogger monitors the keystrokes on the operating system you are using, checking the paths each keystroke goes through. In this way, a software keylogger can keep track of your keystrokes and record each one.
When you were viewing videos your browser started out operating as a RDP having a key logger which provided?
"When you were viewing videos, your browser started out operating as a RDP having a key logger which provided me with accessibility to your display and web cam." "My malware obtained every one of your contacts from your Messenger, FB, as well as email account."
How does a Remote Keylogger Work?
A remote keylogger intercepts keystrokes by monitoring the path the characters pass through when you type. The keys you type go through a path to reach the application. A remote keylogger positions itself on this path to track and record keystrokes. The information is saved on the software for retrieval.
How to protect endpoint devices from remote keylogger?
To protect endpoint devices from a remote keylogger, you need anti malware software with endpoint protection. Endpoint protection monitors the business network and endpoint devices using a central server.
How to prevent remote keylogger?
If there’s an effective tool that can prevent a remote keylogger from entering the computer, it’s the anti malware software. It is designed specifically to detect and block varieties of malware such as a remote keylogger. It also detects spear phishing, fake software, and phishing URL. Just look for a trusted anti malware software and install it on your computer. Then you can do a full malware scan to detect and remove a keylogger from your computer.
Why is anti-malware software important?
But a reputable anti malware software can help you avoid falling victim to keylogger attacks.
What is Comodo Advanced Endpoint Protection?
Comodo Advanced Endpoint Protection prevents data breach by filtering network traffic and data transmission. It also equipped with a Host Intrusion Prevention System that deals with a remote keylogger. It constantly monitors keyboard and hard drive against direct access.
How to prevent keyloggers from infecting my computer?
One effective way to prevent a keylogger from infecting the computer is by using a URL scanner. Just copy and paste the link into the URL scanner. It will scan the reputation of the website to verify if it’s safe or malicious. You can use Comodo Website Inspector or VirusTotal to scan any URL.
What is remote keylogger?
A remote keylogger is a stealthy software that enables hackers to monitor target computers remotely. What makes a remote keylogger a serious threat is its ability to steal personal information by monitoring the computer silently in the background.
What is a free keylogger?
This is an ultimate monitoring solution for home and office. Free Keylogger Remote is the popoular keylogging software, which is able to record all PC activities remotely! You can start spying remotely after 2 minutes of deployment.#N#Just install keyloggeer and quickly configure it. And voila! You don't have to access computer anymore! The reports with recorded information will be sent to your email every day.#N#What activities can record remote keylogger?#N#- Keystrokes. Every key typed on keyboard will be recorded into secure report.#N#- Internet activity. The titles and addressed of all visited websites will be captured as well.#N#- Running applications. When user runs some program, its name and path are catched;#N#- Visual monitoring. The software is able to capture screen every few minutes (you can adjust the interval).#N#- Clipboard text. When the user copies some text, our program will surely record it.#N#What about the Invisibility of this software?#N#Of course, this kind of software must be secure and undetectable! That's why we offer several security options for you:#N#- You can set the password for Free Keylogger. So if you will try to open the program, you will be asked for a password.#N#- The special hotkey is used to switch Invisible mode. When Covert mode is active, the keylogger is fully invisible. So in order to show it, you have to press the special key combination, e.g. Ctrl+Alt+Shift+G . Then you will have to enter your password to access the program.#N#- You can hide keylogger in the Add/Remove Software List of Windows. As well as in the Start Menu / Metro Menu.#N#For whom is this program?#N#Free Keylogger Remote is used in various waysaims. For example, the parents use it to control their children on the Web. They read online conversations, and find out what websites are visited by their kids. The spouse use Free Keylogger to convict of adultery of his/her partner. Also, it is possible to use keylogger on the work, to control the performance of employees. And finally, keylogger is a perfect backup tool for text information. Use keylogger every day on your computer, and you will never lose your passwords, logins and other critical information. You can always recover it from the reports!
How to show keylogger in covert mode?
So in order to show it, you have to press the special key combination, e.g. Ctrl+Alt+Shift+G . Then you will have to enter your password to access the program. - You can hide keylogger in the Add/Remove Software List of Windows.
Why do spouses use keyloggers?
The spouse use Free Keylogger to convict of adultery of his/her partner. Also, it is possible to use keylogger on the work, to control the performance of employees. And finally, keylogger is a perfect backup tool for text information.
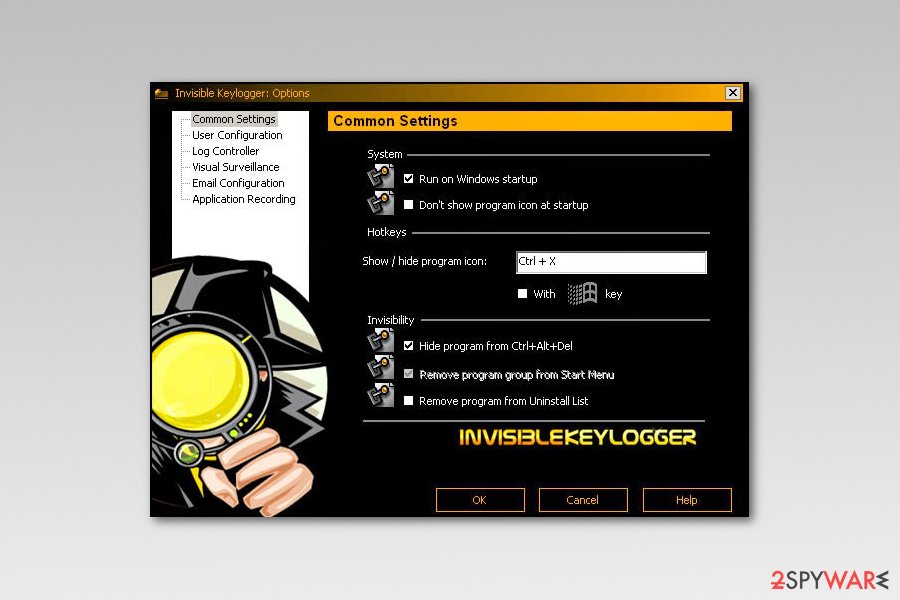
Is Keylogger remote invisibility?
You can also use a special hotkey to switch Invisible Mode which allows you to make the program visible if you wish, but even then, the password will still be required to access it. Additionally, Free Keylogger Remote can be hidden from the Start Menu as well as from the Windows Task Manager to ensure that it remains invisible to all users at all times.
Does a free keylogger remote work?
Once it is set up, Free Keylogger Remote will do wonders in keylogging and PC monitoring. It will record every keystroke typed in any program or application, it will capture the titles and URLs of all visited websites and used applications, and it will even record all clipboard text which means that if some text is copied/cut and pasted instead of typed, it will still be logged.
Can you monitor your PC remotely?
Installation and configuration process is quick and easy and while you need access to the monitored computer to set up Free Keylogger Remote, once it is active, you can monitor the PC’s activity remotely without ever having to have physical access to the PC again. On top of that, this keylogging software is completely invisible and the users will never be able to tell that their PC activity is being recorded.
Is Keylogger Remote free?
Free Keylogger Remote in an all featured spy program that is entirely free of charge. However, it doesn’t lack the quality of features offered by some paid-for software and it performs quite admirably. This keylogging program is completely invisible and password-protected and it successfully records all internet activity, keystrokes, clipboard text, and more. You can view all the logs remotely and avoid the need of having physical access to the monitored PC.
Can antivirus interfere with free keylogger?
However, keep in mind that some antivirus programs might interfere with the Free Keylogger Remote installation . If that happens, you should add the program to the list of exceptions to continue the installation without interruptions.
Does Keylogger have visual monitoring?
Additionally, this keylogger software also comes with the visual monitoring features which means that it will automatically capture screenshots at a predetermined interval. You can choose of often you want the screen to be captured and all screenshots, as well as other logs, will be safely delivered to you and you can view them remotely at any given moment.
Is Keylogger Remote the right keylogger?
So is Free Keylogger Remote the right keylogger for you? If you want to access a wide range of monitoring features without paying for expensive subscriptions – yes, this could be the right keylogger software for you. It is great for those who simply want to backup all their texts and passwords, as well as for those who want to keep an eye on someone’s online activities, application usage, as well as emails and chat messages.
SniperSpy Review
Reading Time: 3 minutes SniperSpy allows live monitoring, records visited websites, and even block websites and social networks such as Facebook and Twitter, chats and other applications. You can do it at the office, at home, or any unit that you want to get access discreetly by getting a keylogger download. VIEW LIVE …
PC Pandora Review
Reading Time: 3 minutes Internet has given us many opportunities to learn, conduct business, play games and socialize. However, this also poses threats to us both in our home and at work. Crimes are rampant nowadays and the internet is a good source of information for those who have bad intent. To prevent ourselves …
SpyAgent Review
Reading Time: 2 minutes Years before we hire spies and do our own physical investigation to monitor the online daily activities of our loved ones and even employees. But today, in this fast changing world, we can do this remotely without hiring someone. As indicated on many online reviews, one of the best spy …
Realtime-Spy Review
Reading Time: 3 minutes Realtime-Spy is the latest high tech surveillance and remote spy that allows you to monitor any computer and access the activities logs anywhere and anytime you want. It is one of the most advanced software today offering remote system shutdown, remote access of log as well as remote log delivery …
Ardamax Keylogger Review
Reading Time: 2 minutes Ardamax Keylogger is on of the less known but very effective remote keyloggers available today. It’s a fact that there is no way for you to monitor your computer at home or in the office every time. You may not even know who among your family members or co-workers use your …
Refog Keylogger Review
Reading Time: 3 minutes Refog keylogger is remote computer monitoring software that allow users to monitor how the target computer is used. Although internet is a very powerful tool that can sharpen user’s skills, when not properly monitored, employees may use office computers for personal gain- this can lower productivity by folds. With the …
AnyKeylogger for Mac Review
Reading Time: 2 minutes Keylogger application is always considered as a spyware program. The fact is, keylogger can be used for many legitimate purposes. Worried parents may use it to record their children’s online activities to check whether they have browsed inappropriate sites.
Can a keylogger spy on someone?
Key Logger can be a nice option for spying on someone. Find out how to install keylogger remotely on a computer.
Can remote keyloggers be used without port configuration?
Remote key loggers are quite easy to install and one doesn’t need to learn rocket science to deal with it. You can really do without a bunch of port configuration information and exceptions lists et-al. However, should you be tracking Trojan concepts of port forwarding and IP addresses are a must.
What is an Android Keylogger?
A Keylogger is a crucial spy app tool which helps to find out all the buttons being pressed in a target device. Basically, an Android keylogger can help you hack anyone’s account by extracting all passwords for you.
How to use Neatspy Android Keylogger?
Getting started with Neatspy is a 3-step process. No technical jargon is involved. Follow the Setup Wizard and you will be able to configure the Neatspy setup on target device smoothly.
What is the most popular Android keylogger app?
Neatspy is the most celebrated Android keylogger app in the market. It has been acclaimed and celebrated by reputed media institutions such as Forbes, New York Times, CNET, and Washington Post.
What is keylogging on Android?
As already explained, keylogging is the feature with which you can find out all the buttons that your target individual is pressing on his Android. Once you have that information you can figure out their passwords, and gain complete access to their phone!
What version of Android is Spyic compatible with?
Spyic is compatible with Android 4.0 or higher versions.
Why is Highster Mobile so good?
The reason that Highster Mobile makes for such a great keylogger for Android is because of its simplicity and minimalism. Highster Mobile is a no-fuss, simple, easy-to-navigate keylogger Android app.
How much does Spyier cost?
It costs $39.99 for a one-month license, $49.99 for three months of access or $99.99 for one year.