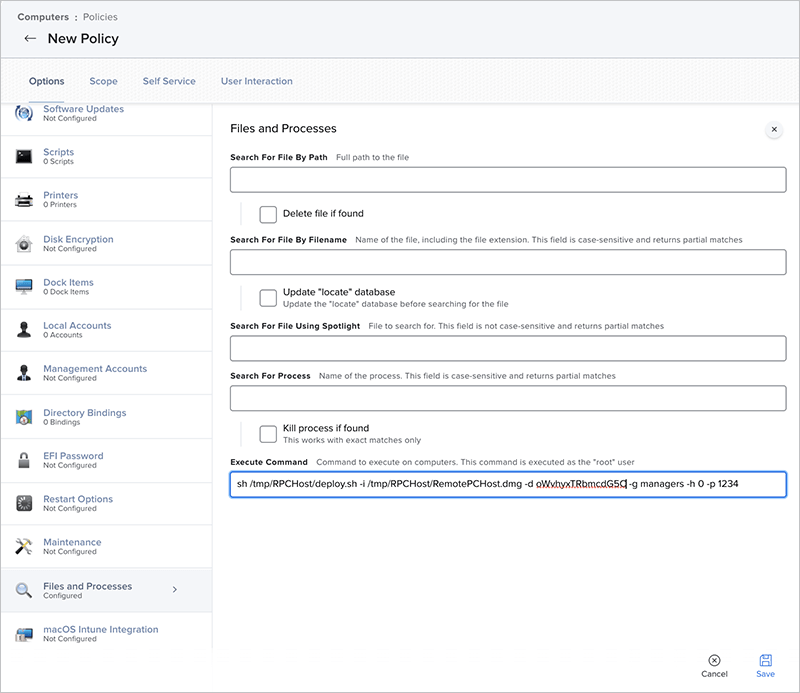
The following table describes the remote commands that you can send from Jamf Pro:
| Remote Command | Description |
| Lock Computer | Logs the user out of the computer, resta ... |
| Remove MDM Profile | Removes the MDM profile from the compute ... |
| Renew MDM Profile | Renews the MDM profile on the computer, ... |
| Wipe Computer | Permanently erases all the data on the c ... |
Full Answer
What remote commands can I send from Jamf Pro?
The following table describes the remote commands that you can send from Jamf Pro: Logs the user out of the computer, restarts the computer, and then locks the computer To unlock the computer, the user must enter the passcode that you specified when you sent the Lock Computer command.
What is Jamf private access?
And Jamf Private Access protects end-user privacy, which means employees don’t need to make tradeoffs in the name of security. Private Access and the power of the platform. A modern Zero Trust Network Access (ZTNA) replaces legacy Enterprise VPN and conditional access workflows.
What is Jamf connect for Macs?
With Jamf Connect, an end user can unbox their Mac, power it on and access all of their corporate applications after signing on with a single set of Okta, Microsoft Azure or Google Cloud credentials.
How do I force Jamf Pro to resend a failed command?
If a remote command reported a failed status, Jamf Pro will automatically resend the command every six hours for the compatible computers. To manually force the attempt, use the “Send blank push” management command. To access this feature, navigate to the Management tab in the inventory of a computer and click Management Commands.
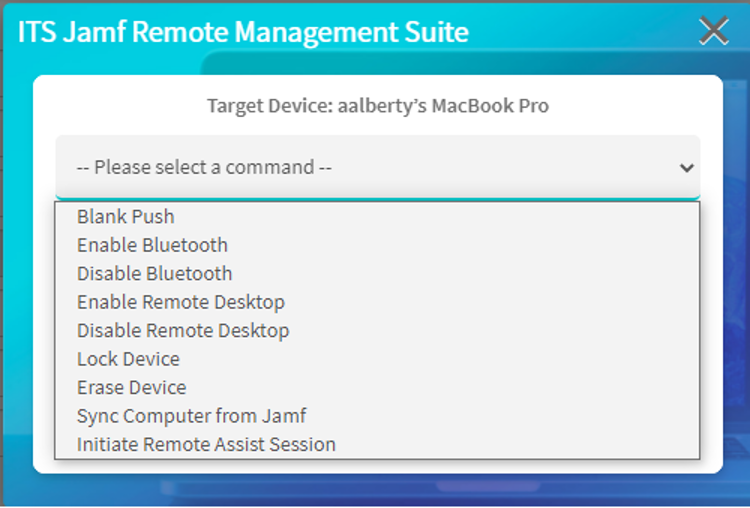
Does jamf allow Remote access?
To initiate screen sharing from Jamf Remote, you need to do the following: Enable remote management by having users select the Screen Sharing checkbox in System Preferences. Note: Because of increased user data protections with macOS 10.14 or later, you cannot enable remote management remotely using the SSH protocol.
How do I Remote into my jamf computer?
To initiate screen sharing from Jamf Remote, you need to do the following:Enable remote management by having users select the Screen Sharing checkbox in System Preferences. ... Ensure the computer running Jamf Remote and the computer being remotely managed are on the same network.
What does jamf have access to?
This content includes access to software, printers, maintenance tasks, helpful links and other documentation. The Self Service app lets users install and manage printers and software on thier devices.
Can jamf track browsing history?
We do not collect any personal information, such as the contents or names of personal files (documents, email, pictures, browsing history, etc).
How does jamf Remote work?
Jamf Remote uses ssh to broker the connection, so you need to have that enabled with your management account given access to ssh. You do not need Screen Sharing enabled.
What can jamf now do?
Jamf Now Service PlansDeploy custom iPad and iPhone apps.Deploy custom Mac packages.Access to Composer, our packaging tool.Deploy custom configuration profiles.Mac Malware Prevention with Jamf Protect.Mac Password Sync with Jamf Connect.Deploy Mac App Store apps and custom apps with Jamf Self Service for macOS.More items...
What Jamf can track?
Jamf Imaging logs. Management history (completed, pending, and failed management commands) Hardware/software history. User and location history.
Is Jamf owned by Apple?
IBM selected Jamf Pro to manage their Macs in 2015. Vista Equity Partners acquired a majority of shares in Jamf in December 2017.
Is Jamf a security tool?
Jamf Protect amplifies core Apple security features with better preventions, stronger controls, and broader visibility and remediation capabilities.
Can MDM see your screen?
Researchers found that with a VPN and trusted certificate, SSL encryption can be broken, allowing MDM to monitor all activity in the browser. This includes information like personal banking passwords, personal email and more, all routed through the corporate network in plain text.
What data does Jamf collect?
Jamf collects data specifically focused on technical support of your device. This can include the following: Hardware specifications/configuration. Installed software applications and usage history.
Can my employer read my iMessages?
Your employer can see how many iMessages you sent or received, but they cannot open and view your messages remotely.
Can remote commands be sent to static computer groups in Jamf?
Remote Commands are deployed via Jamf Pro and leverage Apple Push Notification service (APNs). The remote commands available for computers vary depending on macOS version and PreStage enrollment . Remote Commands can be sent to a single computer or to multiple computers simultaneously.
What does sudo Jamf Recon do?
To ensure inventory is up to date in the JSS, run "sudo jamf recon" from terminal. This will do an inventory scan and send it to the JSS immediately. That way you can be sure the machine you are working on has up to date information in the JSS.
What is the Jamf binary?
Jamf Apps and Binaries /usr/local/jamf/bin/jamf—The binary used to execute most tasks for Jamf Pro. /usr/local/bin/jamf—Symbolic link to the jamf binary so it can be found in the default search paths.
What is Jamf admin?
Jamf Admin—The Jamf Admin application is a repository that allows you to add and manage packages. It also allows you to create configurations (images) using these items and replicate files to distribution points.
Identity-centric security model
Only authorized users can connect to business applications and ensure policy enforcement is consistent across data centers, clouds and SaaS applications.
Application-based microtunnels
Only connect users to apps they are authorized to access. Microtunnels enforce least privilege access and prevent lateral network movement (a common vector for security breaches).
Modern cloud infrastructure
Zero hardware to manage, support contracts to renew or complex software to configure. Even eliminate the need to have administrative control of a device to enable secure access.
Integration with your identity services
Enable user authentication through single sign-on (SSO) and eliminate the need to manage certificates.
Risk-aware access policies
Enhance security by preventing access from users and devices that may be compromised.
Unified access policy
Spans all hosting locations (on-premises, private and public clouds, and SaaS applications), all modern operating systems, and all management paradigms.
Fast and efficient connectivity
Uncompromised access to business apps — without impacting battery life — and operates silently in the background without interfering with the user experience.
Screen Sharing Using Jamf Remote
Disclaimer: Screen Sharing workflow using Jamf Remote has been deprecated. It is recommended to use TeamViewer for remote administration. For instructions on how to integrate TeamViewer with Jamf Pro, see TeamViewer Integration.
General Requirements
To initiate screen sharing from Jamf Remote, you need to do the following:
How Screen Sharing Works
Jamf Pro uses the management account to screen share with Jamf Remote. When a screen sharing session is initiated from Jamf Remote, the following steps are performed to start the screen sharing session:
What is Jamf Connect?
Whether it’s during setup or in day-to-day use, Jamf Connect ensures a single identity is being used to access a user’s device and applications – without the need to bind to Active Directory.
Why is Jamf Connect important?
That’s why Jamf Connect provides IT admins with the ability to keep an eye on all company devices and who is accessing them, when and from what device, providing peace of mind that both the device and corporate information are protected
What percentage of help desk tickets are password resets?
50% of all IT help desk tickets are password resets. That’s why Jamf Connect keeps account credentials in sync between the Mac and cloud-identity provider ensuring employees stay on task instead of making trips to IT.
How to send remote command to Jamf Pro?
Log in to Jamf Pro. Click Computers at the top of the page. Perform a simple or advanced computer search. Click the computer you want to send the remote command to. If you performed a simple search for an item other than computers, you must click Expand next to an item to view the computers related to that item.
Can you send a remote command to multiple computers?
You can send a remote command to a single computer. Some commands can also be sent to multiple computers at once using mass actions. For more information, see Mass Actions for Computers. Note: The remote commands available for a particular computer vary depending on the computer's OS version.
A shift from legacy to modern access
Admins now have the task of accommodating more users and devices, in different places, on more networks. Relying on the corporate perimeter no longer ensures user and device trust. This means security and access strategies must evolve while keeping end-user productivity and privacy in mind.
Zero-trust network access for remote access and network security
Authentication alone may not protect sensitive business data from compromised devices. So what’s the solution?
Create a modern identity management stack to unlock productivity and transform business
Directory services acts as a centralized record of employee information, such as name and department. Often used when integrating with Apple device management platforms like Jamf to deploy customized devices.
