Configure IPsec (remote access)
| Name | Example settings |
| Interface | 203.0.113.1 Select a WAN port. |
| Authentication type | Digital certificate |
| Local certificate | Appliance certificate |
| Remote certificate | TestCert Select a locally-singed certifi ... |
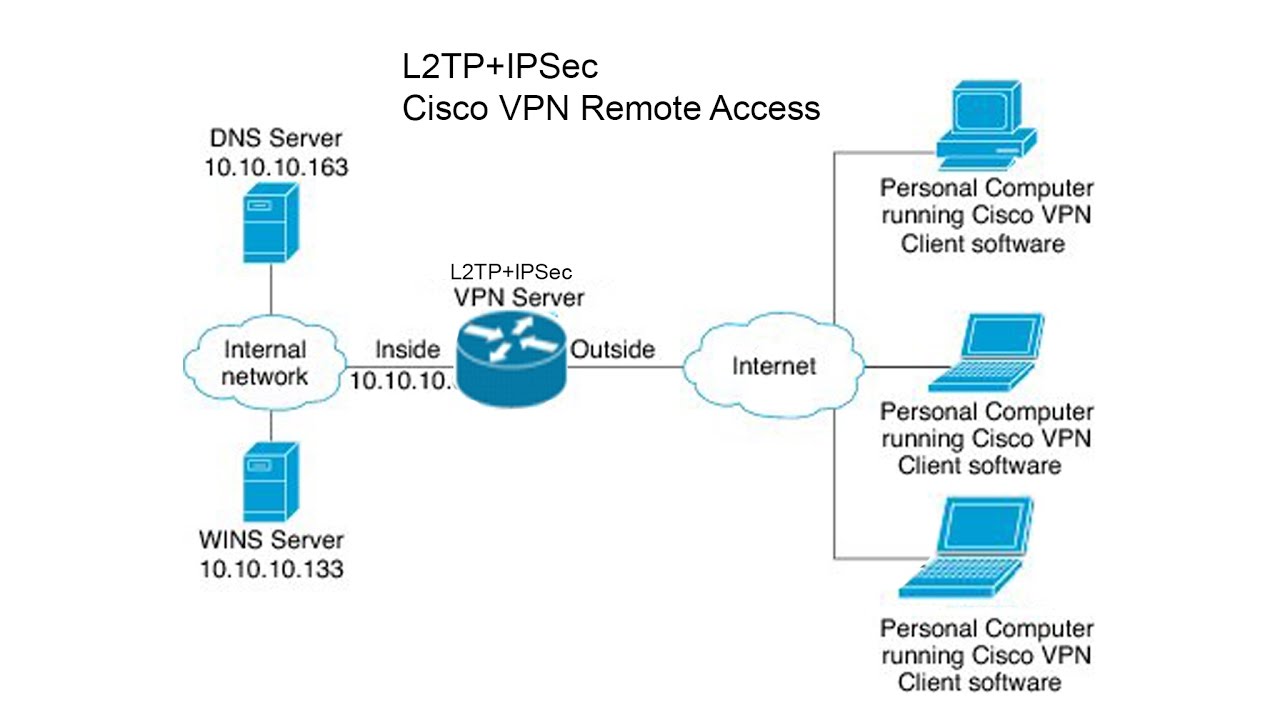
Which IPsec remote access VPN client should I use?
The current best practice is to use IKEv2 for IPsec Remote Access on modern clients. See IPsec Remote Access VPN Example Using IKEv2 with EAP-MSCHAPv2 for details. This setup has been tested and working on various Android and iOS devices. Other clients may work as well.
How to set up IPsec server setup?
IPsec Server Setup ¶. 1 Navigate to VPN > IPsec, Mobile Clients tab. 2 Check Enable IPsec Mobile Client Support. 3 Check Provide a virtual IP address to clients. 4 Enter an unused subnet in the box, pick a subnet mask. 5 Set any other desired options here. 6 Click Save. 7 Click Apply Changes. 8 Click Create Phase1 (if it appears)
How to allow IPsec tunnel connections on Wan?
To allow IPsec Tunnel Connections, the following should be allowed on WAN. To allow traffic passing to your LAN subnet you need to add a rule to the IPsec interface. In the next table you can see the existing VPN authentication mechanisms and which client operating systems support it, with links to their configurations.
How do I enable IPsec xauth for a user?
Add a user, grant the user the User - VPN - IPsec xauth Dialin permission, or add them to a group with this permission. Note that for xauth, the password used is the password for the user, not the “IPsec Pre-Shared Key” field. That is used for non-xauth IPsec.

Can IPsec be used for remote access?
This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using IPSec. IPSec allows you to give individual hosts access to your network through an encrypted IPSec tunnel.
What is the difference between VPN and IPsec?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
What is IPsec remote access VPN Sophos XG?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
How is IPsec used in VPN?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
Can IPsec be hacked?
Hackers Could Decrypt IPsec Information However, a team of researchers discovered numerous security vulnerabilities related to an internet key exchange protocol called “IKEv1.” IPsec maintains encrypted connections between two parties when both of them define and exchange shared keys during communications.
Is IPsec only used for VPN?
While IPsec isn't the only protocol out there, it's strong in three scenarios: VPN security, application security, and routing security. VPN security—particularly for businesses—is noteworthy. The IPsec standard comes with baked-in support for multiple cryptographic methodologies.
How do I configure IPsec remote VPN in Sophos XG firewall?
Configure IPsec remote access VPN with Sophos Connect clientSpecify the settings on the Sophos Connect client page.Send the configuration file to users.Add a firewall rule.Send the Sophos Connect client to users. ... Users install the client, import the configuration file into the client, and establish the connection.
How do I configure IPsec remote access VPN in Sophos XG firewall?
3:5113:14Sophos Firewall: Configure IPsec and SSL VPN Remote Access - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou will need to port forward port udp 500 udp 4500 and the esp protocol with ip protocol number 50MoreYou will need to port forward port udp 500 udp 4500 and the esp protocol with ip protocol number 50 from the upstream router for authentication type select pre-shared key and enter the phrase.
How do I enable IPsec VPN Sophos?
From Sophos Firewall, go to Rules and policies > Firewall rules and verify that the VPN rules allow ingress and egress traffic. Go to Current activities > IPsec connections to view the existing connections. Go to Reports > VPN and verify the IPsec usage. Click the connection name for details.
What are the benefits of IPsec?
IPsec provides the following security services for traffic at the IP layer: Data origin authentication—identifying who sent the data. Confidentiality (encryption)—ensuring that the data has not been read en route. Connectionless integrity—ensuring the data has not been changed en route.
What is the difference between IPsec and SSL VPN?
The main difference between IPsec and SSL VPNs is the endpoints for each protocol. While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network.
What are the 3 protocol used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Is IPSec better than OpenVPN?
IPSec is generally regarded as faster than OpenVPN. The main reason for this is actually a pro for OpenVPN in another area, and that is how it is implemented. IPSec is implemented in the IP stack of the kernel, whereas OpenVPN is implemented in the userspace.
Which type of VPN is best?
Many VPN experts recommend OpenVPN as the most secure protocol. It uses 256-bit encryption as a default but also offers other ciphers such as 3DES (triple data encryption standard), Blowfish, CAST-128, and AES (Advanced Encryption Standard).
What's the difference between OpenVPN and IPSec?
IPSec is more complex than OpenVPN and can require additional configuration between devices behind NAT routers. However as long as both the server and client support NAT traversal there shouldn't be any issues.
What are the benefits of IPSec?
IPsec provides the following security services for traffic at the IP layer: Data origin authentication—identifying who sent the data. Confidentiality (encryption)—ensuring that the data has not been read en route. Connectionless integrity—ensuring the data has not been changed en route.
What is IPsec firewall?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301. Use these settings to create and manage IPsec connections and to configure failover.
What is remote access policy?
With remote access policies, you can provide access to network resources by individual hosts over the internet using point-to-point encrypted tunnels. Remote access requires SSL certificates and a user name and password.
What is a bookmark in a VPN?
Bookmarks specify a URL, a connection type, and security settings. Use bookmarks with clientless access policies to give users access to your internal networks or services. For example, you may want to provide access to file shares or allow remote desktop access. Users can access bookmarks through the VPN page in the user portal.
How to enable Sophos Connect?
Go to VPN > Sophos Connect client and click Enable.
What is Sophos Connect?
Sophos Connect client is VPN software that runs on Microsoft Windows 7 SP2 and later, and Mac OS 10.12 and later. It establishes highly secure, encrypted VPN tunnels for off-site employees.
What is firewall rule?
Firewall rules implement control over users, applications, and network objects in an organization. Using the firewall rule, you can create blanket or specialized traffic transit rules based on the requirement. The rule table enables centralized management of firewall rules.
How to send only traffic through XG firewall?
Optional To send only traffic destined to XG Firewall through the tunnel, under Networks , click Add new, enter the subnets you want to allow users to access, and press Enter. This automatically turns off the Tunnel all option.
What is IPSEC VPN?
IPSec VPN is used to create a VPN connection between local and remote networks. To use IPSec VPN, you should check that both local and remote routers support IPSec VPN feature. Then, follow the steps below to set up an IPSec VPN connection.
How to add VPN to AC modem?
You can refer to How to log into the web-based interface of the AC VDSL/ADSL Modem Router (new logo)? 2) Go to Advanced > VPN > IPSec VPN, and click Add. 3) In the IPSec Connection Name column, speci fy a name.
What is site A in Archer VR2800?
Here takes Archer VR2800 as demonstration. 1. The typical VPN topology is here. Site A refers to local network, and Site B refers to the remote network that is to be connected. Record Site A and Site B’s LAN and WAN IP addresses before you start configuration. 2. Configuration on Site A (local network).
IP-HTTPS: Route error
After you install and configure DirectAccess in Windows Server, you may receive an error message that indicates that IP-HTTPS is not working correctly. When you view the Operations Status overview in the Dashboard of the Remote Access Management console, the display shows that the IP-HTTPS interface is in error.
IP-HTTPS: Certificate error
In other situations, the issue can be related to the certificate itself. That would be true in this instance because the certificate is expired:
IP-HTTPS: Route advertisement error
Because the error message is clear, check whether the route advertisement is disabled. If it is, enable it.
IPSec error
To be able to connect to internal resources, two connection security tunnels are configured by the remote access wizard through a GPO and deployed on the DA clients and DA servers.