The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
Full Answer
What is site to site and remote access VPN?
A site-to-site VPN is a permanent connection designed to function as an encrypted link between offices (i.e., “sites”). This is typically set up as an IPsec network connection between networking equipment. A remote access VPN is a temporary connection between users and headquarters, typically used for access to data center applications.
Why use a VPN for remote access in the cloud?
Why is a VPN Needed?
- Reduces Risk. A Clark School study is one of the first to quantify the near-constant rate of hacker attacks on computers with Internet access—every 39 seconds on average—and the non-secure ...
- Secures & Extends Private Network Services. ...
- Leverages Existing Security Investments. ...
- Increases Employee Productivity. ...
How to setup a VPN Server and connect through it?
Here’s how you can do this:
- Open the Settings menu
- Select Network and Internet
- Click on VPN, which’ll bring you back to the screen we had shown above
- You should be able to see the VPN profile you had added on this screen.
- Click on the “Connect” button and wait for a few minutes
- You’ve now successfully connected to a VPN server!
Can connect to VPN, cannot access remote resources?
If you cannot access some resources using only the VPN (e.g., it’s behind a departmental firewall), Millward said you should connect to the GlobalProtect client first to verify your identity, then use your preferred remote access management client.

How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What is a VPN and how is it implemented?
What is a VPN and how does it work? A virtual private network (VPN) is a series of virtual connections routed over the internet which encrypts your data as it travels back and forth between your client machine and the internet resources you're using, such as web servers.
Why must you create a remote access policy for VPN?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
What is remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is the purpose of VPN?
What is the purpose of a VPN? The main purpose of a VPN is to hide your online activity. VPNs are often used to guard against hackers and snoops on public networks, but they're also useful for hiding your IP address, browsing activity, and personal data on any Wi-Fi network — even at home.
What is the purpose of a remote access policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
What should be included in a remote access policy?
Remote policies have guidelines for access that can include the following: Hardware and software configuration standards for remote access, including anti-malware, firewalls, and antivirus. Encryption policies. Information security, confidentiality, and email policies.
Why is remote access important?
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
Why you shouldn't use a VPN?
The 10 biggest VPN disadvantages are: A safe, top-quality VPN will cost you money: Read more. VPNs almost always slow your connection speed: Read more. Using a VPN on mobile increases data usage: Read more. Some online services try to ban VPN users: Read more.
How a VPN solution could be implemented into the network for remote working?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How does a VPN work for dummies?
A VPN does the same but over the internet. It uses data encryption and special servers to make your connection inaccessible to other internet users. It's like a wire connecting those same two computers – only the second one is the entire internet. The scale is much bigger, but the level of security is the same.
What is VPN and types of VPN?
Virtual Private Network (VPN) services fall into four main types: personal VPNs, remote access VPNs, mobile VPNs, and site-to-site VPNs. In this guide, we explain how each of these VPN types work and when to use them. A VPN is a service that creates a private tunnel within a public connection (e.g. the internet).
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
What type of authentication does a VPN use?
Most VPN solutions support different types of authentication mechanisms, depending on the type of VPN (site-to-site, remote user). One type that supports MFA is the use of RADIUS, in which the VPN server becomes a RADIUS client to a RADIUS server, which in turn is able to perform a Multi-factor Authentication. For example, CyberArk Idaptive connector software can serve as a RADIUS server as well as an AD proxy to perform the AD authentication as well as present a second factor in the form of a mobile authenticator, OATH OTP, email, for the second factor.
Is it important to grant access to devices with verified by MFA?
With users being remote, and possibly also using their own devices (BYOD), it is important to only grant access to those devices with users who were verified by MFA as part of logging into the device itself.
Is VPN safe for remote access?
The VPN is one of the most time-tested, albeit a bit risky, solution out there for secure remote access. I call it risky because, if not properly implemented and maintained, attackers might be able to exploit weaknesses to gain privileged access to sensitive systems and data. In fact, some organizations are opting for new ways to connect their remote workforces that eliminate the need for VPNs or agents and help streamline operations and user workflows.
Does anyconnect support SAML?
Does the solution support a client-less VPN authentication mechanism such as SAML? This is especially convenient since then the IT administrator does not have to ensure that each client is installed with the right version of the client and thus is able to embrace a wider range of endpoints in a secure fashion. Some clients (Cisco’s Anyconnect is an example) do have support for embedded browsers, which can then support SAML.
What is a VPN site to site?
Site-to-Site VPNs, sometimes called LAN-to-LAN or L2L VPNs connect two locations or sites together , extending a classical WAN design. Two intermediate devices, commonly called VPN gateways, protect the traffic between the two LANs. This type of VPN tunnels packets between the locations: the original IP packet from one LAN is encrypted by one gateway, forwarded to the destination gateway, and then decrypted and forwarded to the local LAN at its end to the destination. From the real source and destination’s perspective, the VPN is virtual—they do not even know their traffic is being protected between the two VPN gateways. The most common
What is VPN in business?
Virtual Private Network (VPN) is the technology that can use to access the office or home network remotely and securely over the Internet, so that the communication data is protected from hijacking by hackers. When the VPN connection is established between 2 parties (between a VPN client and vpn gateway or between 2 VPN gateways), ...
How does IPSec work?
To facilitate VPN connections, one of the VPN gateways issues a request to the other to establish an IPSec connection. The two VPN gateways exchange information with each other and create an IPSec connection. Routing on each network is configured so that as hosts on one network need to communicate with hosts on the other network, their network traffic is automatically routed through the IPSec connection, protecting it appropriately. A single IPSec connection establishing a tunnel between the gateways can support all communications between the two networks, or multiple IPSec connections can each protect different types or classes of traffic. [2]
What is the most common site to site protocol used to protect traffic?
The most common. Site-to-site protocol used to protect traffic is IPSec Routers are commonly used as the VPN gateway product, though other products can be used, such as firewalls. Cisco products that support IPSec L2L VPNs include routers, ASA and PIX security appliances, and the VPN 3000 concentrators.
What is IPSEC protocol?
IPSec is an Internet Engineering Task Force (IETF) standard suite of protocols that provides data authentication, integrity, and confidentiality as data is transferred between communication points across IP networks. IPSec provides data security at the IP packet level. A packet is a data bundle that is organized for transmission across a network, and it includes a header and payload (the data in the packet). IPSec emerged as a viable network security standard because enterprises wanted to ensure that data could be securely transmitted over the Internet. IPSec protects against possible security exposures by protecting data while in transit. [1]
What is the least commonly used VPN architecture?
The least commonly used VPN architecture is the host-to-host model, which is typically used for special purpose needs, such as system administrators performing remote management of a single server. In this case, the organization configures the server to provide VPN services and the system administrators.
Why is VPN gateway called VPN gateway?
The VPN gateway is aptly named because it functions as a “gatekeeper” for each of the computers connected on the Local Area Network behind it. In most cases, each gateway will have a “public” facing address (WAN side) and a “private” facing address (LAN side).
What is clientless VPN?
With clientless SSL VPNs, a user uses a web browser as the client software. And because most users have a web browser already installed on their PCs and are very comfortable with web browser applications, there is basically no special client software nor any learning curve involved to use the SSL VPN. SSL VPNs, however, have one limitation: because they are implemented at the application layer, only web-based applications (those via a web browser) can be protected. Other applications, by default, are not protected. In some instances, an SSL VPN vendor can write special code on the SSL VPN gateway device to handle additional applications. But as to what applications are actually supported, this will vary from vendor to vendor. In this instance, a Layer-3 VPN solution, such as IPsec or L2TP/IPsec, would be better because they can protect all traffic from the network layer and above; in other words, these VPNs are not application-specific. SSL VPNs are discussed in more depth in Chapter 5, "SSL VPNs."
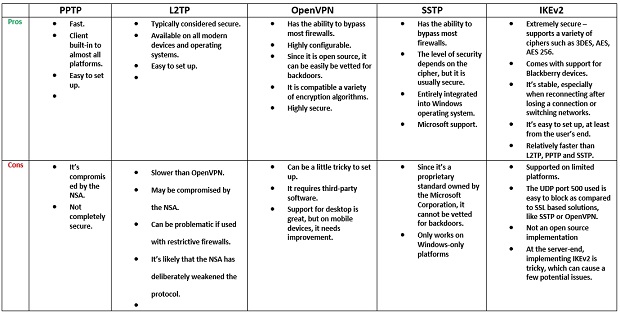
What is PPP protocol?
Point-to-Point Protocol ( PPP) This standard is used to define the encapsulation process: PPTP encapsulates PPP packets, containing the payload, within an IP packet, which is transported across a network.
What is MPPE in PPTP?
Microsoft Point-to-Point Encryption (MPPE) This standard is used to provide for data confidentiality (encryption) for PPTP.
Does GRE work on Cisco routers?
From a Cisco-product perspective, GRE works only on Cisco IOS-based routers.
Is PPTP open standard?
One problem with using PPTP is that even though the process was defined later in an IETF RFC, PPTP was a semi-open standard. In other words, if you worked in a Microsoft environment, or with vendors that worked closely with Microsoft, deploying PPTP worked well. However, PPTP typically would not work in a mixed-vendor networking environment.
Can GRE be used as a VPN?
Because of these two limitations, GRE is typically not used as a complete VPN solution; however, it can be combined with other solutions, such as IPsec, to create a more robust and scalable VPN deployment.
Is GRE a good VPN?
Given its flexibility of encapsulating many protocols, you would think that GRE would be a great VPN solution, at least compared to other VPN solutions with limited protocol support. However, GRE has two main disadvantages:
What is the first step in implementing a VPN?
The first step is to evaluate a company’s strategy. What is the goal the company hopes to achieve through the use of a VPN? It may be growth, cost reduction, application enablement, or a combination of those things. Knowing the strategic foundation and the priorities of a company is the first step in successfully implementing a VPN.
Why do universities use VPN?
Universities use VPN to secure faculty resources from students, and wireless networks use VPN clients to ensure that there is no unauthorized “”snooping”” from outside their property.
What is the difference between a VPN and a VPN?
The second type of VPN is the Remote Access VPN, which connects individual tele-workers to corporate networks. The difference between a LAN-to-LAN VPN and a Remote Access VPN is the point where the tunnel terminates at the user side. The Remote Access VPN tunnel terminates at the user workstation and is maintained by VPN client software running on ...
What is VPN in the internet?
In general, there are two types of Virtual Private Networks (VPN). The first type is known as site-to-site or LAN-to-LAN, and is typically used to connect Local Area Networks (LANs) at remote locations to corporate networks through the Internet. The Internet is transparent to the LAN-to-LAN user, since the VPN “”tunnel”” provides ...
What are the drivers of VPN?
Other drivers include: higher levels of security, increased mobility, better quality of service and increased access to information .
Is VPN a LAN to LAN?
The Internet is transparent to the LAN-to-LAN user, since the VPN “”tunnel”” provides a secure connection to the other side. This tunnel is created and maintained by a VPN gateway at the remote site, and a VPN concentrator at the main location. The second type of VPN is the Remote Access VPN, which connects individual tele-workers ...
Is VPN based on SSL?
With the increase in VPN popularity also come pressures towards standardization. Most VPNs today are based on IPSec, with some using the SSL security protocol. Encryption is based on DES-3 with some movement towards AES (Advanced Encryption Standard). Users can be assured that VPN technology is secure.
Why is VPN better than other methods of remote communication?
Communication with a VPN connection provides a higher level of security compared to other methods of remote communication, keeping private networks closed to people who don’t have authorized access.
How to get a VPN up and running?
The simplest way to get your VPN up and running is to install clients from your VPN provider. However, they may not offer software for every platform you need, such as Windows, iOS, and Android. Even if they don't, it's better to install what they offer first and then confirm that your VPN account is operating correctly.
Why is my VPN connection so slow?
Slow connection speeds. If you're using a VPN client that provides free VPN service, your connection speed may be slow, as these providers do not usually offer high-speed connections. Consider whether the speed is sufficient for business needs.
How to fix VPN not working?
Usually, your VPN provider's client will start working right away. But if that's not the case, try these steps: 1 Shut down and reopen the client and try rebooting your device. 2 If you have any other VPN software running, make sure you're disconnected, then close it down.
What is the oldest VPN protocol?
Point-to-Point Tunneling Protocol is one of the oldest VPN protocols. But it is becoming less widely used since there are faster and more secure protocols available.
What is VPN in business?
Businesses often use VPN connections because they're a more secure way to help employees remotely access private company networks, even when they're working outside the office. The VPN lets remote devices, like laptops, ...
What to do if VPN doesn't work?
If, for some reason, your VPN provider doesn't offer software for the devices your business uses, check the provider's website for guides on manual setup. Hopefully, you'll find the documentation you need. If you don't, search for other providers' setup guides that use the same devices.