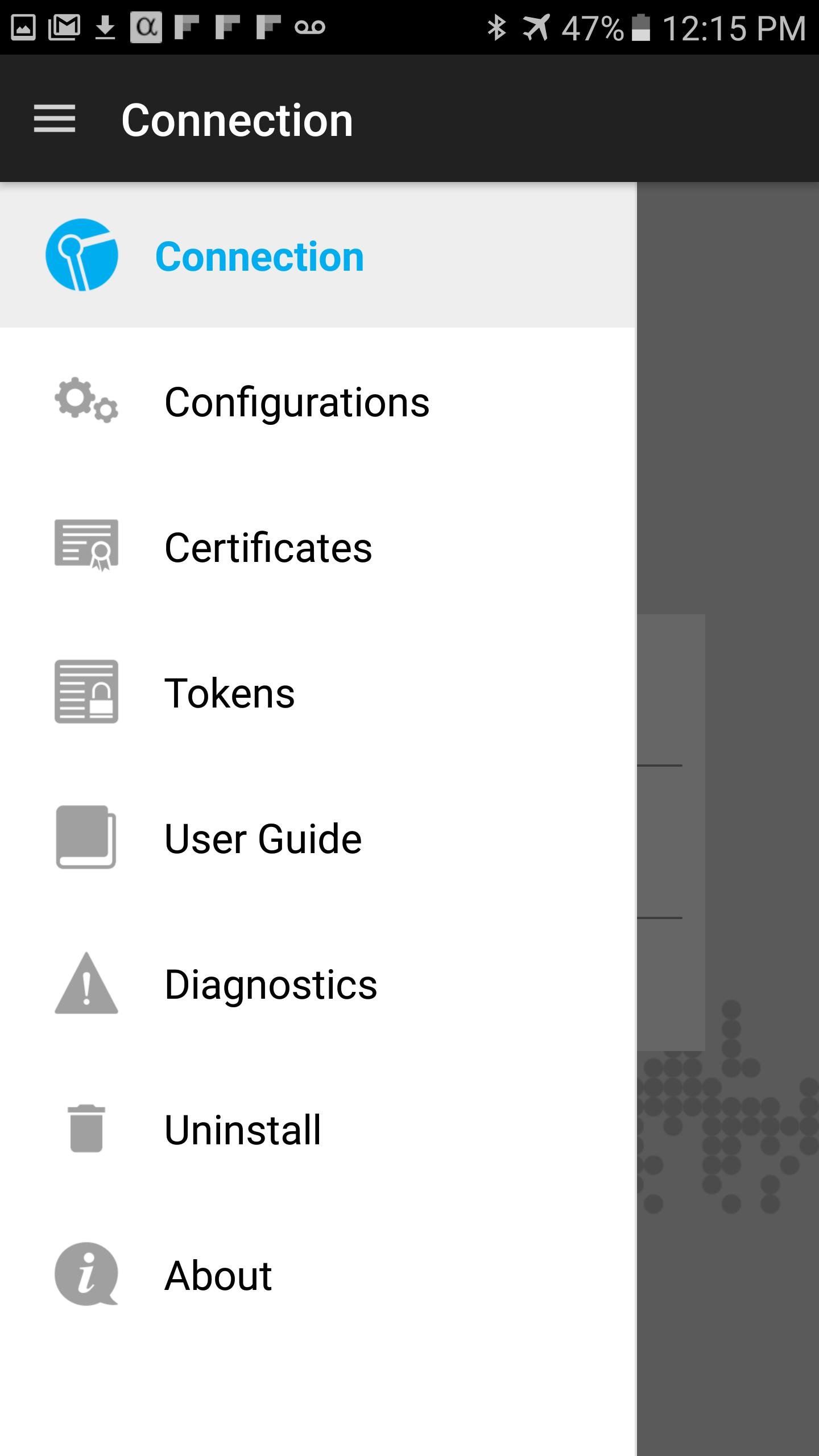
What is F5 remote access?
Clientless remote access is remote network access obtained without the installation of software on a user's device. Unlike IPsec VPNs, the F5 BIG-IP APM provides remote access without requiring pre-installed client software and configuration of the remote device.
What is F5 VPN used for?
F5 Network's FirePass SSL VPN is an SSL VPN that provides broad application support, scalability, easy installation and use, and the highest standard of integrated end-point security.
How do I connect to F5 in access?
How to setup F5 using App ConfigurationNavigate to Apps & Books > List View > Public.Select Add Application and select Android from the Platform field.Search for F5 within the managed Google Play iframe and approve permissions for F5 to add the app into the Workspace ONE UEM Console.More items...•
Is F5 Big-IP a VPN?
F5 Access is lightweight and provides SSL VPN secure access as an alternative to the BIG-IP Edge Client. End users can download and install F5 Access directly from their respective app stores.
Who owns F5 VPN?
NGINX, Inc.As a part of the NGINX, Inc. acquisition in 2019, F5 offers a premium, enterprise-level version of NGINX with advanced features, multiple support SLAs, and regular software updates.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is F5 client?
F5 offers two types of apps that support BIG-IP APM: F5 Access Clients: Downloaded from OS App stores (iTunes for iPhone, iPad, and iPod touch (iOS) devices, at the Google Play Store for Android devices, at the Chrome Web Store for Google Chrome OS, and at the Windows Phone Apps+Games store)
How do I connect to a big-IP?
TopicLog in to the Configuration utility.Go to Access > Connectivity / VPN > Connectivity > Profiles. Note: For BIG-IP 12. ... Select the name of your connectivity profile.Select Customize Package.Select BIG-IP Edge Client.Select the Enable Always connected mode check box.
How do I log into a big-IP?
"First off, you need to log in to the BIG-IP APM Configuration utility. In the app, navigate to Access > Connectivity / VPN > Network Access (VPN) > Network Access Lists. Navigate to the network access profile > Network Settings tab. To configure it for the client, you would need to click Advanced option.
How do I run F5 on VPN?
Connect to a profile to use the connections to your network supported by F5 Access.On your Windows system, select. Settings. VPN. . On Windows Mobile, select. Settings. Network & Wireless. VPN. ... Select the existing VPN profile. Additional options display.From the new options, select. Connect. .
Is VPN better than SSL?
If it would be easy for attackers to lure folks to them as a MITM, SSL is probably better since it authenticates each server to the client. A typical VPN, once set up, doesn't help the user avoid an attacker who has gotten into other hosts on the VPN.
Which VPN is the best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What is SSL VPN used for?
A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for specialized software.
What is the use of big IP Edge client?
The BIG-IP Edge Client is a Virtual Private Network (VPN) technology which provides Windows logon integration, endpoint protection, client inspection, network and application access. This entry only applies to the Desktop edition of the software.
Which VPN is the best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
Is VPN better than SSL?
If it would be easy for attackers to lure folks to them as a MITM, SSL is probably better since it authenticates each server to the client. A typical VPN, once set up, doesn't help the user avoid an attacker who has gotten into other hosts on the VPN.
Why Access Control and Authorization Matters
With users connecting from various locations and devices, and applications in multiple environments, organizations need a new secure access approach to prevent data breaches and increase user productivity.
How F5 Can Help
F5 has developed best practices for secure access solutions to meet the needs of a wide variety of customers. Whether you need to quickly scale and secure your remote access solution or accelerate your zero trust application access plans, F5 can help.
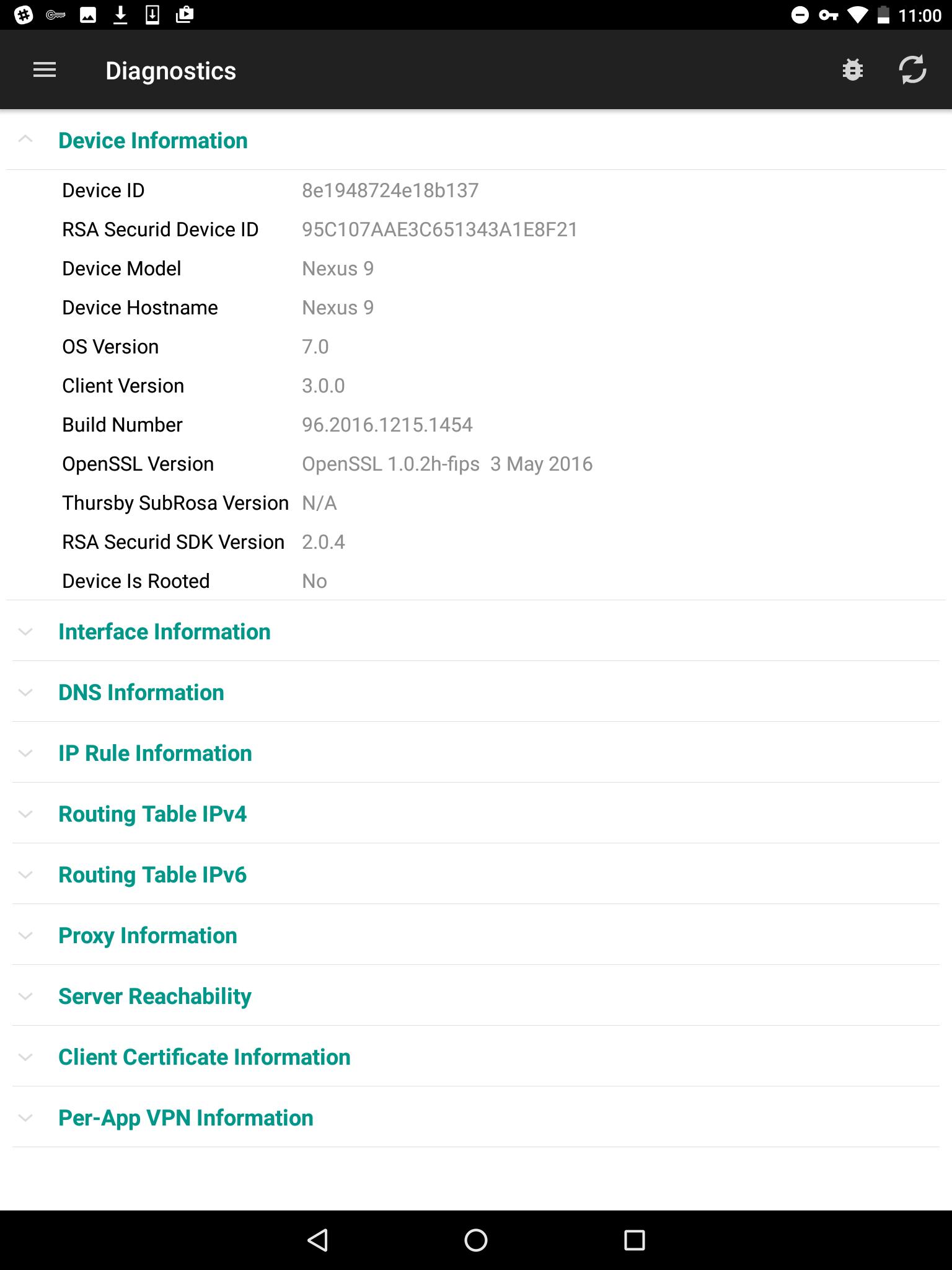
What is APM in remote desktop?
When you create a remote desktop resource, Access Policy Manager (APM) automatically creates an allow ACL for the IP addresses and ports specified in the resource. To disallow access to any other IP addresses and ports, you must create ACLs that deny access to them and assign the ACLs in the per-session policy. F5 recommends that you create an ACL that rejects access to all connections and put it last in the ACL order.
What is APM in RDP?
The configuration supports Microsoft RDP clients on Windows, Mac, iOS, and Android. When a user types the address or hostname of the gateway into an RDP client and specifies a particularly configured virtual server for it, APM authorizes the client. When the client requests connections to resources on backend servers, APM authorizes the access.
What is APM webtop?
APM webtop supports native connections for Windows, Mac, and Linux clients. When this option is selected, a user on any compatible platform is presented with a simple interface to the Microsoft RDP server with reduced visual display features.
How to edit access profile?
The Access Profiles ( Per-Session Policies) screen opens. Click the name of the access profile for which you want to edit the access policy. The properties screen opens for the profile you want to edit. On the menu bar, click.
Why Zero Trust Application Access Matters
Applications can be located anywhere and accessed from everywhere. In a zero trust architecture, it’s imperative that app access is secure, regardless of where the app or user is located.
Implementing Zero Trust
As users become more mobile and apps are hosted in numerous data centers and clouds, the traditional network perimeter is fading away and tough to defend. Try a different approach by streamlining and protecting authentication and managing access to apps via a centralized access proxy that moves the perimeter to your apps, users, and devices.
How to edit access policy?
On the Main tab, click Access Policy > Access Profiles. The Access Profiles List screen opens. Click the name of the access profile for which you want to edit the access policy. The properties screen opens for the profile you want to edit. On the menu bar, click Access Policy.
Can you specify a hostname for a destination?
Note : If you specify a hostname for your destination, make sure that it is DNS-resolvable. After the remote desktop is assigned to a full webtop in an access policy, the remote desktop does not appear on the full webtop if the hostname is not DNS-resolvable. Under the Default Customization Settings section, type a Caption.
Specifying LDAP or Active Directory server information
Verify that the BIG-IP ® system user accounts have been created on the remote authentication server.
Specifying client certificate LDAP server information
Verify that the required user accounts for the BIG-IP ® system exist on the remote authentication server.
Specifying RADIUS server information
Verify that the BIG-IP ® system user accounts have been created on the remote authentication server.
Configuring access control for remote user groups
You perform this task to assign a user role, a corresponding administrative partition, and a type of terminal access to a remotely-stored group of user accounts. For a given user group, you can assign as many role-partition combinations as you need, as long as each role is associated with a different partition.
Saving access control settings to a file
You can save the running configuration of the system, including all settings for remote user authentication and authorization, in a flat, text file with a specified name and the extension .scf.
Importing BIG-IP configuration data onto other BIG-IP systems
You can use the tmsh sys load command to import a single configuration file (SCF), including access control data, onto other BIG-IP ® devices on the network.
Can you see a remote user account in Big IP?
If a remote user account has the default role assigned to it, you cannot see that account in the user account list.
Can a remote user access different partitions?
Individual members of this account cannot have access to different partitions. From the Terminal Access list, select Enabled or Disabled. Click Update.