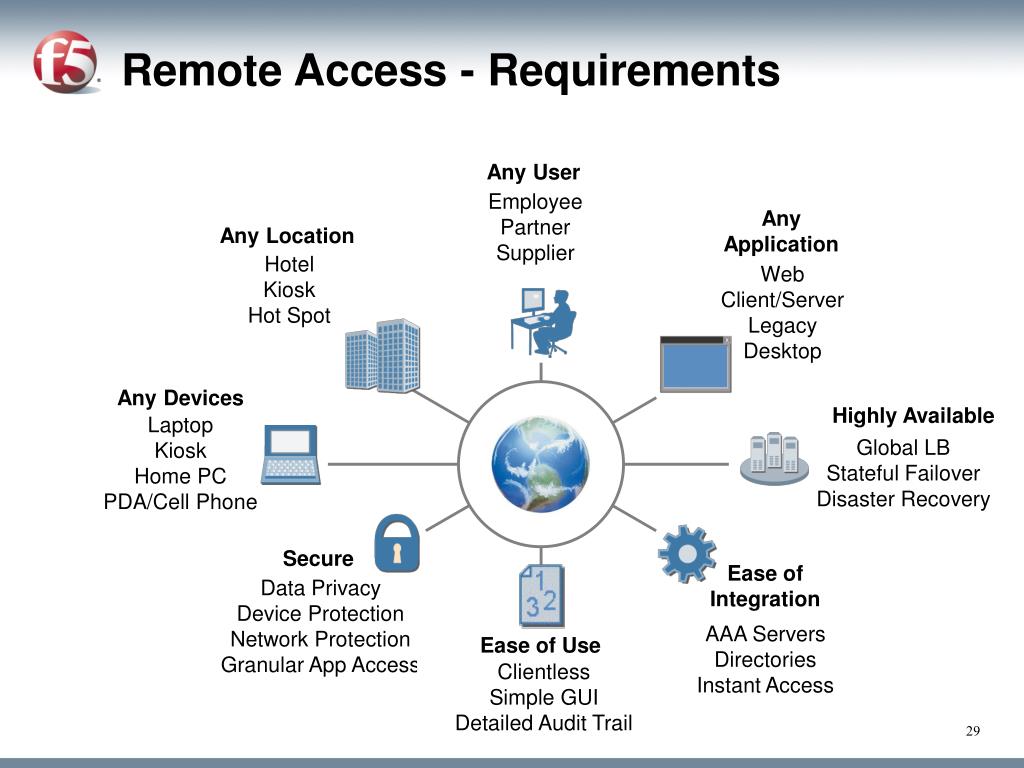
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
What does F5 stand for in F5 Networks?
F5 Networks originally have been named F5 Labs, which have been established in 1996. The company name was inspired by the 1996 movie Twister, in which reference was made to the fastest as well as the most powerful tornado on the Fujita Scale: F5. F5’s first product was a load balancer called BIG-IP, which was launched in 1997.
What is a F5 Access app?
The recently launched F5 Distributed Cloud WAAP (Web Application and API Protection) can address all the security concerns of an app-centric world through end-to-end observability. It further provides organizations with valuable insights and telemetry from a centralized interface across their distributed app infrastructure.
What is F5 access?
F5 announces BIG-IP Next Cloud-Native Network Functions (CNF) for service providers migrating network services to the cloud or deploying 5G. The new F5 CNFs will be globally available in the Rakuten Symphony Symworld marketplace. Rakuten Mobile will also ...
See more

What is F5 remote access?
Clientless remote access is remote network access obtained without the installation of software on a user's device. Unlike IPsec VPNs, the F5 BIG-IP APM provides remote access without requiring pre-installed client software and configuration of the remote device.
What is F5 VPN client?
F5 Network's FirePass SSL VPN is an SSL VPN that provides broad application support, scalability, easy installation and use, and the highest standard of integrated end-point security.
How do I connect to F5 in access?
Connect to a profile to use the connections to your network supported by F5 Access.On your Windows system, select. Settings. VPN. . On Windows Mobile, select. Settings. Network & Wireless. VPN. ... Select the existing VPN profile. Additional options display.From the new options, select. Connect. .
What is F5 Networks BIG-IP Edge client?
F5 BIG-IP® Edge Gateway™ is an accelerated remote access solution that brings together SSL VPN, security, application acceleration, and availability services.
Is F5 a firewall?
F5® BIG-IP® Local Traffic Manager™ (LTM) has numerous security features that enable it to serve as a network firewall, so Internet data centers can deliver applications while protecting the infrastructure that supports their clients. The BIG-IP system is an ICSA Certified Network Firewall.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
Is Big-IP Edge Client a VPN?
The BIG-IP Edge Client is a Virtual Private Network (VPN) client; its purpose is to establish and maintain a VPN tunnel.
How do I connect to a big-IP?
TopicLog in to the Configuration utility.Go to Access > Connectivity / VPN > Connectivity > Profiles. Note: For BIG-IP 12. ... Select the name of your connectivity profile.Select Customize Package.Select BIG-IP Edge Client.Select the Enable Always connected mode check box.
How do I use big-IP Edge Client?
Installing Windows version of f5 BigIP Edge ClientDownload Windows f5 BigIP Edge Client.Open the BIGIPEdgeClient.exe from the location that you saved it in step 1.Click Install.If you see the Windows Smart Screen warning click More info.Then click Run anyway.Program will show a progress bar.Click Finish.
Why is my F5 VPN not working?
Check if any network firewall is blocking the VPN connection. Check if any software firewall is blocking the VPN connection. Re-install corrupted Add-ons. Re-build client's OS.
What is big IP Edge client components?
BIG-IP Edge Client for Windows comprises individual components that provide Windows log on integration, endpoint protection, client inspection, and network and application access.
How do I download F5 VPN?
How to install F5 Access on your Android device:Click on the Continue To App button on our website. ... Once the F5 Access is shown in the Google Play listing of your Android device, you can start its download and installation. ... A pop-up window with the permissions required by F5 Access will be shown.More items...
Who owns F5 VPN?
NGINX, Inc.As a part of the NGINX, Inc. acquisition in 2019, F5 offers a premium, enterprise-level version of NGINX with advanced features, multiple support SLAs, and regular software updates.
What is the SSL VPN?
A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for specialized software.
What is F5 load balancer?
A load balancer is a device that acts as a reverse proxy and distributes network or application traffic across a number of servers. Load balancers are used to increase capacity (concurrent users) and reliability of applications.
How does SSL VPN Work?
SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
Explore Solutions to Top Challenges
Know what makes your apps vulnerable and how they can be attacked, so you can put solutions in place that lower your risk.
FRAUD: IN A GAME OF CAT AND MOUSE, BE THE CAT
Companies that effectively fight fraud have one thing in common—they bring their security and fraud departments together, sealing the cracks fraudsters often easily slip through.
Move to the Cloud with Confidence
Migrate applications to AWS with F5 and keep the same level of security, reliability, and scalability you already depend on.
Threat Intel, Tech Details, and Peer Connections
Get the who, what, when, and what’s next in cyber-attacks to inform your security.
Support, Account Management, and Partner Resources
Knowledge center, downloads, bug tracking, bug patches, online training, and more.
Next Steps
We can assess your needs and connect you with the right cloud provider, reseller partner, or an F5 sales engineer.
What is Citrix remote desktop?
Citrix remote desktops are supported by Citrix XenApp and ICA clients. With Access Policy Manager you can configure clients to access servers using Citrix terminal services. You provide a location from which a client can download and install a Citrix client for a Citrix ICA connection.
What is APM in RDP?
The configuration supports Microsoft RDP clients on Windows, Mac, iOS, and Android. When a user types the address or hostname of the gateway into an RDP client and specifies a particularly configured virtual server for it, APM authorizes the client. When the client requests connections to resources on backend servers, APM authorizes the access.
How to complete the process of remote desktop?
To complete the process, you must assign a webtop, apply the access policy, and associate the access policy and connectivity profile with a virtual server so users can launch the remote desktop session .
How to edit access policy?
On the Main tab, click Access Policy > Access Profiles. The Access Profiles List screen opens. Click the name of the access profile for which you want to edit the access policy. The properties screen opens for the profile you want to edit. On the menu bar, click Access Policy.
When creating a virtual server for an access policy, what address is specified?
When creating a virtual server for an access policy, specify an IP address for a single host as the destination address.
Can you specify a hostname for a destination?
Note : If you specify a hostname for your destination, make sure that it is DNS-resolvable. After the remote desktop is assigned to a full webtop in an access policy, the remote desktop does not appear on the full webtop if the hostname is not DNS-resolvable. Under the Default Customization Settings section, type a Caption.
Is there a subset of access policy items?
Note: Only an applicable subset of access policy items is available for selection in the visual policy editor for any access profile type.
What is machine tunnel?
When installed on client machines as a Windows Service, a machine tunnel starts during the machine boot sequence, and establishes a VPN connection to the specified APM servers in background. No user interaction or interactive Windows session is required. This can be used for several different scenarios.
Why install component installer with elevated privileges?
On Windows-based clients, install the Component Installer with elevated privileges so that it can install, upgrade, and run APM components that require elevated privileges.
What is BIG IP?
This feature allows you to specify that the client is always connected to the VPN, and allows you to configure the behavior when the client is not connected. You can specify whether the client is connected automatically after Windows logon, and configure exclusion addresses.
What is a custom Windows client package?
Customize a Windows client package to specify the client components to install, and to customize settings for BIG-IP Edge Client and Dialup Settings components if you include them.
What is APM in Windows?
Access Policy Manager ® (APM ®) supports all Network Access features with BIG-IP ® Edge Client ® for Windows. For a complete list of Network Access features, refer to
How does Big IP work?
Users of BIG-IP Edge Client for Windows can connect securely and automatically to your network while roaming using the automatic reconnect, password caching, and location awareness features of Edge Client. You can also enforce Always Connected mode, and configure the list of trusted sites to which to allow access. You can customize the client package and you must download it and make it available to users as hosted content on the BIG-IP system or through another delivery mechanism. Users must install the package, or Component Installer, if available on the client, can install it for them.
What is machine cert Auth check?
A Machine Cert Auth check requires administrative privilege. The Windows client package associated with a connectivity profile can be configured to include a Machine Certificate Checker Service component. The service can check the machine certificate on a client endpoint even when the user does not have admin privilege. The option to include this component in the package is disabled by default.
What can you use network settings for?
You can use network settings to specify a lease pool for network access clients, and also to configure traffic options, client behavior, DTLS settings, and set up proxy behavior.
What is proxy ARP?
Proxy ARP allows remote clients to use IP addresses from the LAN IP subnet, and no configuration changes are required on other devices such as routers, hosts, or firewalls. IP address ranges on the LAN subnet are configured in a lease pool and assigned to network access tunnel clients. When this setting is enabled, a host on the LAN that sends an ARP query for a client address gets a response from Access Policy Manager with its own MAC address. Traffic is sent to the Access Policy Manager and forwarded to clients over network access tunnels.
What is APM in network?
When this setting is enabled, Access Policy Manager ® (APM ®) continuously checks the DNS order on the network interface and sets the network access-supplied entries first in the list if they change during a session. To use your local DNS settings as primary and the network access-supplied DNS settings as secondary, clear this setting. This might be useful when split tunneling is in use and a client connects remotely. This check box is selected by default.
What is ACE in SSH?
This example access control entry (ACE) allows SSH connections to the internal host at 192.168.112.9.
What happens if you enable security warnings?
If you enable this setting, the system displays security warnings before starting applications from network access, regardless of whether the site is considered a Trusted site. If the check box is not selected, the system displays security warnings if the site is not in the Trusted Sites list.
What is launch application settings?
Specify launch application settings to control how applications are launched when the network access connection starts.
What is auto map?
Auto Map specifies that the system uses all of the self IP addresses as the translation addresses for the pool.