
What is secure remote access?
Secure Remote Access. Secure remote access safeguards sensitive data when applications are accessed from computers outside the corporate network. Secure remote access calls for measures to ensure end-point security and use an SSL VPN to authenticate users and encrypt data.
How does F5 handle secure remote access?
How Does F5 Handle Secure Remote Access? F5 has a host of access security solutions purpose-built to keep good traffic flowing and bad traffic out. BIG-IP Access Policy Manager (APM) lets you create identity-aware, context-based access policies, implement an SSO solution, and create an SSL VPN.
What is the best remote access solution for your business?
Virtual Private Network (VPN) – VPNs are extremely popular for remote access, since they allow remote users connected via insecure remote Wi-Fi (Starbucks, bookshops) to connect to a private network through an encrypted tunnel.
What are the characteristics of a successful remote access implementation?
These characteristics of a successful remote access implementation mean different things across various communication contexts: facility-to-facility (F2F), business-to-business (B2B), and individual-to-business (I2B). Three current solutions provide the flexibility to match implementation-specific requirements: T1/T3, IPSec VPN, and SSL VPN.
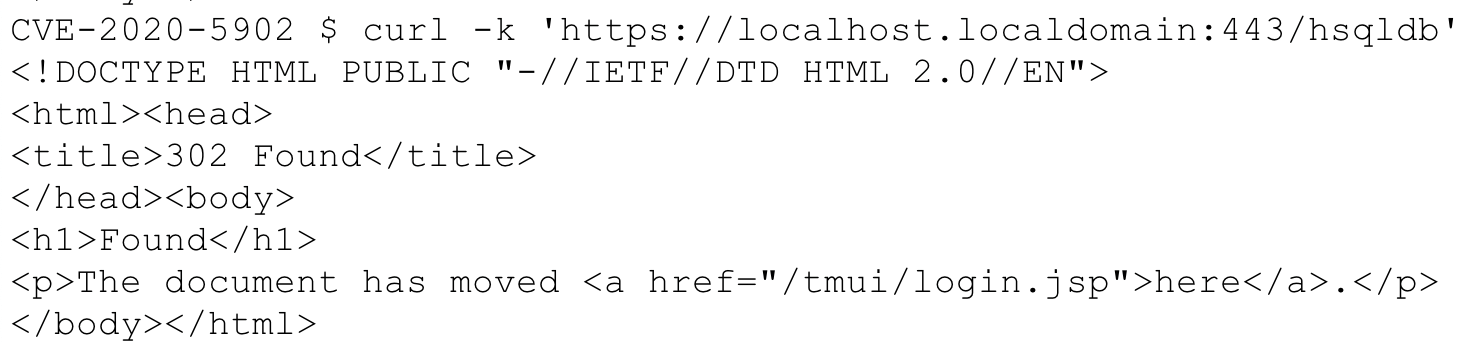
What is a secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What is supervised F2F protocol?
The multi-technology, multi-frequency readers support supervised F2F protocol, which is a proprietary reader communication protocol and wiring scheme used by the Symmetry SR product, as well as by some legacy access control systems.
How do you secure a remote network?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is F5 remote access?
Clientless remote access is remote network access obtained without the installation of software on a user's device. Unlike IPsec VPNs, the F5 BIG-IP APM provides remote access without requiring pre-installed client software and configuration of the remote device.
What is an Osdp card reader?
In contrast to a Wiegand reader which is essentially a basic one-way communication device, an OSDP reader is a “smart” device that can both communicate to the controller and receive communication from the controller.
What is Osdp communication?
June 23, 2021. Open Supervised Device Protocol (OSDP) is an access control systems standard developed by the Security Industry Association (SIA). The protocol works across all parts of an access control system, including the tag reader, access control panel, and lock.
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
Is F5 a VPN?
F5 Network's FirePass SSL VPN is an SSL VPN that provides broad application support, scalability, easy installation and use, and the highest standard of integrated end-point security.
Is F5 VPN good?
An excellent VPN solution for companies. A good VPN solution for companies. Especially on Mac. No disconnection or connection problems.
What is SSL and VPN?
A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for specialized software.
Which option creates a secure connection for remote workers?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It's the secure, private method for virtually entering the corporate office, so to speak.
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
How can you ensure your network remains secure when you have clients with remote access?
Utilise VPNs Any remote connection between a computer and the corporate network should always be secured via a virtual private network (VPN) connection. The private network eliminates the need for a physical connection between integrated devices so that employees can remotely and securely access the office's servers.
Which protocol would you use to set up a secure connection at a remote site?
SSL – A Secure Socket Layer (SSL) is a network security protocol primarily used for ensuring secure internet connections and protecting sensitive data. This protocol can allow for server/client communication as well as server/server communication.
How Does F5 Handle Secure Remote Access?
F5 has a host of access security solutions purpose-built to keep good traffic flowing and bad traffic out. BIG-IP Access Policy Manager (APM) lets you create identity-aware, context-based access policies, implement an SSO solution, and create an SSL VPN.
Why is remote access important?
Why is Secure Remote Access Important? With the proliferation of internet-connected devices, an organization’s workforce is no longer sequestered to a single location. Instead, an organization may have employees connecting to their internal network and accessing sensitive data from locations across the globe.
What is endpoint security?
Endpoint security – Verifies desktop antivirus and firewall software is in place, systems are patched, keyloggers or other dangerous processes are not running, and sensitive data is not left behind in caches
What is a security policy?
It can refer to any security policy or solution that prevents unauthorized access to your network or sensitive data. With the proliferation of internet-connected devices, an organization’s workforce is no longer sequestered to a single location.
Is old security enough?
Because of this, old access security measures are no longer enough and must be replaced with safeguards that allow employees and other verified users safe and secure access from anywhere, at any time, from any device.
What is secure remote access?
What it means to provide secure remote access has changed considerably in the past few years as a result of new technologies and the pandemic. At its most basic, secure remote access is having location-agnostic connectivity among enterprise users and centralized applications, resources and systems, whether cloud-based or on premises.
Who is responsible for secure remote access?
Although remote access tools, such as VPNs and firewalls, are typically under the purview of network teams, in this new era, cybersecurity teams tend to lead and manage the policies, processes and technologies associated with ensuring secure remote access.
The diminishing power of VPNs
One tactic organizations use to combat the vulnerabilities associated with working remotely -- especially if employees are using consumer-grade systems -- is to reestablish VPN standards. This entails enforcing basic protections, such as strong passwords, multifactor authentication, role-based access and encryption.
Setting secure remote access policies
A hallmark of secure remote access is the underlying policy that safeguards access to and the use of enterprise resources, such as data, databases, systems and networks.
Components of the secure remote access ecosystem
Secure remote access touches just about every aspect of enterprise security. TechTarget has curated a series of guides to help IT and security professionals get up to speed on important technologies and concepts.
Zero trust and secure remote access
Cybersecurity and IT teams realize words like perimeter and trust are quickly becoming outdated as borders dissolve and the base of users that need access to resources expands. No longer are organizations protected by four castle walls, with a firewall moat keeping miscreants out.
SASE and secure remote access
Secure Access Service Edge is an emerging concept that combines network and security functions into a single cloud service, not only to alleviate traffic from being routed through the data center, but also to embrace a remote workforce, IoT adoption and cloud-based application use.
What is remote access security?
Remote access security begins with hardening the devices seeking to connect, as demonstrated in Chapter 6. We follow this with a selection of one or more remote access methods based on functional and technical requirements. Finally, we control access based on context.
What is remote access?
Remote access is no longer just about a laptop or home desktop user connecting to catch up on some work or update customer and order information. The explosion of consumer devices in the hands of our employees changes how we look at remote connectivity. In addition to supporting various platforms and proprietary operating systems, traditional security controls do not provide sufficient granularity for policy enforcement. This results in either lax security or inflexibility in how we deliver business services.
How many T1s can be bonded?
When an organization requires more bandwidth, it can bond multiple T1s to look like a single connection. For example, bonding two T1s results in bandwidth of about 3 Mbps. Another option is to implement a full or partial T3 circuit. A T3 is an aggregate of 28 T1s, providing bandwidth of 44.736 Mbps.
How is context based access control facilitated?
Context-based access control is facilitated by first defining policies, as depicted in Figure 9-9. Remote access policy must address who, what, when, where, and with what is access allowed and to what extent. Figure 9-10 depicts an example of how an organization might apply a set of polices.
Which is better for today's Internet connected businesses with multiple communication pathway requirements?
A better choice for today’s Internet-connected businesses with multiple communication pathway requirements is VPN, which we explore in detail later in this chapter.
Is remote access better than internet?
Using the Internet with high-speed connections is a better option and usually more secure.
Do access controls apply to all devices?
The principle standard to apply across all access and all devices is that different controls apply to different access contexts.
