While Site to Site VPN uses a security method called IPsec to build an encrypted tunnel from one Customer network (generally HQ or DC) to the customer’s remote site between whole or part of a LAN on both sides, Remote access VPN connect individual users to Private Networks (usually HQ or DC). Advertisements
What is the difference between site to site VPN and remote access VPN?
Both Site to site VPN and Remote access VPN are the types of VPN which stands for Virtual Private Network. Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer.
What is a remote-access VPN?
With remote-access VPNs, the device of the remote user is in charge of encrypting and decrypting data that is either sent or received. A remote-access VPN requires a NAS (network access server), or VPN gateway, to authenticate the credentials of any device attempting to sign into the VPN.
What is site-to-site VPN?
Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer.
How secure is your remote access solution?
A robust, secure remote access solution should be designed to provide highly secure access to the applications and data that employees need to be productive. Granular access can be granted to specific applications depending on role or user type, reducing risk associated with traditional VPNs that may provide more unrestricted network access.
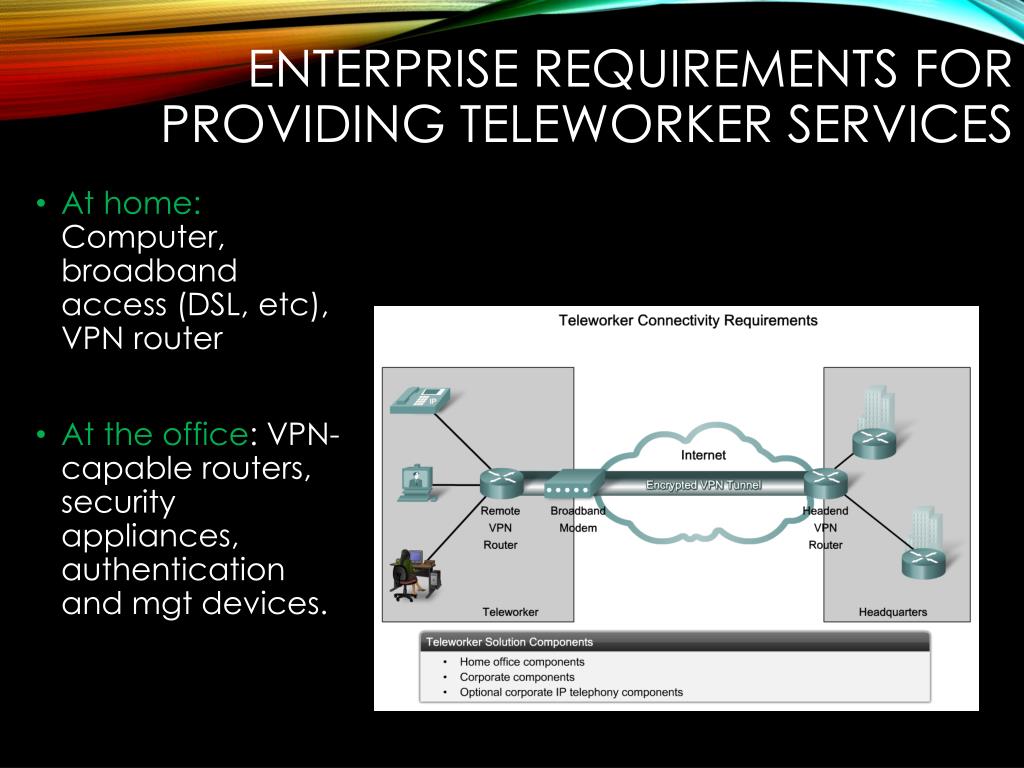
What is remote access and site to site VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does VPN work for remote access?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How secure is a site to site VPN?
Secure Connectivity: All traffic flowing over a site-to-site VPN is encrypted. This means that any business data crossing over the public Internet is encrypted, protecting it against eavesdropping and modification.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How does VPN help you stay secure?
VPN security enables users to protect their online privacy and prevent their internet service provider (ISP) from tracking their browsing activity. It works by connecting a user's device to the VPN server, then passing their internet traffic through the VPN provider's internet connection.
What is VPN and how does it work?
VPN stands for "virtual private network" — a service that helps you stay private online. A VPN establishes a secure, encrypted connection between your computer and the internet, providing a private tunnel for your data and communications while you use public networks.
Why do we need a site-to-site VPN?
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits.
What are two benefits of a site-to-site IPsec VPN?
Security. Site-to-site VPN security is the most important benefit, as IPsec protocols will ensure all traffic is encrypted in transit through the VPN tunnel. ... Scalability. When compared to a traditional VPN, a top benefit of a site-to-site VPN is its scalability. ... Lower latency. ... Managed services options.
What is needed for a site-to-site VPN?
In order to set up an internet-based site-to-site VPN between two sites, a VPN gateway (router, firewall, VPN concentrator, or security appliance) such as the Cisco Adaptive Security Appliance (ASA) is required at both sites.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is remote connectivity?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
Can you be tracked if you use VPN?
However, if you use a poor quality VPN, you could still be tracked. A premium quality VPN encrypts data and hides your IP address by routing your activity through a VPN server; even if someone tries to monitor your traffic, all they'll see is the VPN server's IP and complete gibberish.
Which VPN is best for remote access?
Best Remote Access VPNs for business.Perimeter 81 – Best all-round business VPN.GoodAccess – Security Strategy Options.ExpressVPN – Lightning Fast VPN.Windscribe – VPN with Enterprise-Friendly Features.VyprVPN – Secure VPN with Business Packages.NordVPN – Security-first VPN.More items...•
What is site to site VPN?
Site-to-Site VPN is also known as Router-to-Router VPN. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. Multiple users are not allowed in Site-to-Site VPN.
What is remote access VPN?
Remote access VPN. 1. In site to site VPN, IPsec security method is used to create an encrypted tunnel from one customer network to remote site of the customer. In remote access VPN, Individual users are connected to the private network. 2.
What is remote access VPN?
A remote access VPN is a temporary connection between users and headquarters, typically used for access to data center applications.
Why do organizations use VPNs?
Many organizations use site-to-site VPNs to leverage an internet connection for private traffic as an alternative to using private MPLS circuits. Site-to-site VPNs are frequently used by companies with multiple offices in different geographic locations that need to access and use the corporate network on an ongoing basis. ...
How to use SASE?
Some of the benefits of using a SASE are that it allows companies to: 1 Provide branch offices and retail stores with access to the cloud or the data center. 2 Quickly identify users, devices and applications. 3 Consistently apply security policies across multiple locations and enforce least-privileged access. 4 Dramatically simplify their IT infrastructure and reduce costs since they can use a single cloud-based solution instead of buying and managing multiple point products.
What are the benefits of using a SASE?
Some of the benefits of using a SASE are that it allows companies to: Provide branch offices and retail stores with access to the cloud or the data center. Quickly identify users, devices and applications. Consistently apply security policies across multiple locations and enforce least-privileged access.
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other
Remote access to corporate networks and internal resources has become the norm, rather than the exception, for...
Continue Reading This Article
Enjoy this article as well as all of our content, including E-Guides, news, tips and more.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What are the advantages of remote access VPN?
Another advantage of remote access VPNs is that they provide companies with an affordable way to secure data sent by offsite employees. The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows and this is especially true if a VPN service provider is used.
Why is VPN important for business?
The most important benefit though is data security. When an offsite employee sends data through a VPN, it is encrypted, so even if a hacker is able to intercept that data, they won’t be able to use it. This is particularly important if an employee accesses their companies’ network using public Wi-Fi while traveling because traffic sent over these networks is usually not encrypted.
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is a network access server?
A network access server could be a dedicated server or it might be a software application running on a shared server. Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
Why do businesses use VPNs?
Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
4 benefits of site-to-site VPNs
Site-to-site VPN security is the most important benefit, as IPsec protocols will ensure all traffic is encrypted in transit through the VPN tunnel. The site-to-site VPN tunnel only allows traffic from one end to the other, blocking any attempts to intercept the traffic from the outside.
Considerations before adopting a site-to-site VPN
As with any technology, there are some risks to consider before deploying a site-to-site VPN. Settings and configurations must be monitored with care, especially when dealing with a PKI.
What is VPN connection?
A VPN (Virtual Private Network) is a secure connection between you and the internet. It provides its users with more online privacy, security, and freedom. There are several ways to set up a VPN connection, but most private users do so by subscribing to a VPN service.
What is VPN on the internet?
When you’re using the internet, there is a constant process of your device exchanging data with other parties on the web. A VPN, or Virtual Private Network, creates a secure tunnel between your device (e.g. smartphone or laptop) and the internet.
What is a VPN?
Back to the basics. VPN stands for Virtual Private Network. Using a VPN is an easy and efficient way to increase your online safety, privacy and freedom.
How Does a VPN Work?
Connecting to a VPN is generally quite simple. After subscribing to a VPN provider, you download and install the VPN software. You then select a server you want to connect to and the VPN will do the rest.
Does a VPN Slow Down Your Internet Connection?
After all, a VPN redirects your connection through a remote server. This takes longer, so it could slow down your internet connection. However, this isn’t always the case.
Is Using a VPN Legal?
If those people can’t be traced online, it’s much harder to punish them for their crimes, after all. Even so, this doesn’t necessarily mean a VPN is illegal.
What VPN providers are there?
Above we have shown you three good VPN providers but there are hundreds of companies that offer commercial VPNs. Just type in VPN in the App Store or Play Store, and you’ll see a dizzying amount of VPN apps, that are often free to download. And then there are also quite a few companies that offer business VPN packages.
How to allow VPN access to private subnets?
Go to the Admin UI and go to VPN Settings. In the item titled Should VPN clients have access to private subnets set the selection to Yes, using routing (advanced) and in the large text field just below it specify the subnet of the network where your OpenVPN Access Server is located. To compare it to the example site-to-site setup described in the picture series above, this would be 192.168.70.0/24. Make sure the checkbox to allow access from the private subnets is left checked. Now save settings and update running servers.
How to login to OpenVPN?
Go to the OpenVPN Access Server's client UI using a web browser, click the connect dropdown menu and switch it to login. Enter the user name and password of the user account you created for site-to-site connectivity and click go. You will be presented with a list of files available for this user account. Locate the auto-login profile and download it. It will be called client.ovpn.
What is site to site setup?
A site-to-site setup is where two (or more) different networks are connected together using one OpenVPN tunnel. In this connection model, devices in one network can reach devices in the other network, and vice versa. The implementation of this is, for as far as Access Server is involved in this, relatively simple. The more difficult part comes when dealing with firewalls and security filtering options, and altering routing tables in routers and Internet gateways, as there are so many of them of various brands and models, that we cannot possibly document all of them. However, routers should all have one thing in common: the ability to route traffic using static routes. With that capability comes the means to send traffic from one network to another, through a gateway system that provides connectivity to the other network. An OpenVPN Access Server with a Linux VPN gateway client forms such a gateway system, to form a bridge between two networks. If your network equipment is then properly adjusted as well, then a site-to-site setup that works transparently for all devices in the two networks can be achieved.
What IP address does OpenVPN use?
With the new static routes in place, whenever traffic now arrives at the router that has as a destination an IP address somewhere in 172.16.0.0/20 or 10.0.60.0/24, it will know that it should forward this to the OpenVPN Access Server at IP address 192.168.70.222. It will then forward it to where it needs to go, as it knows how to contact those two subnets.
How to connect to ovpn on Linux?
Transfer this client.ovpn file to your Linux client system (with SCP or WinSCP or copying and pasting contents of the file in a text editor like nano) and place it in the /etc/openvpn/ directory. Rename the file to something like headquarters.conf. The filename is not particular important, but the extension must end with .conf for the OpenVPN daemon to pick it up. Now reboot the Linux client operating system. It should now automatically connect and you should be able to see this connection appear on the OpenVPN Access Server's Current Users overview.
How to install OpenVPN on Linux?
What you do need is the OpenVPN open source client program for Linux. On Ubuntu you can install this with the command apt-get install openvpn. With the client program now installed, it is going to check for any *.conf files in the /etc/openvpn/ directory and at system startup try to connect them and keep them connected. What we need next is to obtain the auto-login connection profile for the user account created for site-to-site connectivity, and save it in the /etc/openvpn/ directory. To do that we need to get the file first:
What is IP forwarding?
IP forwarding is the function in an operating system that allows it to accept an incoming network packet on one network interface, and if the destination is on another network, to forward it there. This is what you need when packets coming in from your network need to go to the VPN tunnel, or vice versa.
What is site to site VPN?
Site-to-site VPNs connect entire networks to each other, for example, connecting a branch office network to a company headquarters network. In a site-to-site VPN, end hosts send and receive normal TCP/IP traffic through a VPN “gateway”. The VPN gateway is responsible for encapsulating and encrypting outbound traffic.
Why use VPNs?
Cost savings – VPNs enable organizations to use cost-effective, high-bandwidth technologies, such as DSL to connect remote offices and remote users to the main site.
What command to use to verify PPP?
Use the debug ppp negotiation command to verify PPP negotiation.
Where is the DSL connection located?
The DSL connection is set up between the customer premises equipment (CPE) and the DSL access multiplexer (DSLAM) device located at the Central Office (CO). Transceiver – Usually a modem in a router which connects the computer of the teleworker to the DSL.
Can you configure single homed BGP?
Note: Although it is recommended only in unusual situations, for the purposes of this course, you will configure single-homed BGP.
Can PPP be used on all serial links?
PPP can be used on all serial links including those links created with dial-up analog and ISDN modems.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.

What Is A Remote-Access VPN?
Which Is Right For Me?
- Choosing between a remote-access VPN and a site-to-site VPN depends entirely on your needs. If you’re just looking for a personal solution to keep yourself safe and anonymous while using the internet, then a remote-access VPN is the perfect choice for you. If you’re choosing a VPN for your business, you can’t overlook the significant financial and human resource demands required by …
Conclusion
- A remote-access VPN allows a device to securely communicate with your company’s private LANno matter where in the world the device or the LAN may be. A site-to-site VPN, however, securely bridges your various LANs – no matter where they are– to allow employees at all LAN locations secure access to the resources of the complete network. A site-to-site VPN certainly p…
Further Reading
- Check out the best VPNs according to Reddit. Find great savings on VPN plans with our VPN deals and coupons. Learn how to secure your business with The Complete Cybersecurity Guide for Small Businesses.