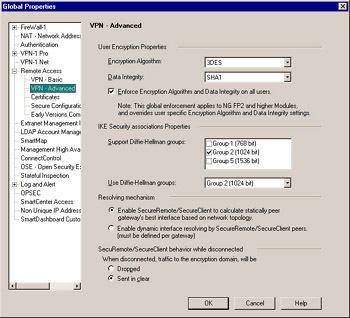
How does remote access work with Check Point?
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser. Provides full access to the corporate network with a VPN client. Provides web-based access without the need to install a VPN client.
What version of E82 is securemote on Windows?
E82.40_TRAC.cab Product SecuRemote, Check Point Mobile, Endpoint Security VPN Version E82 Minor Version E82.40 OS Windows Build Number MD5
How to install Endpoint Security VPN on a client computer?
To install Endpoint Security VPN for Mac on a client computer: Download the Endpoint Security VPN for Mac E82.00 - Disc Image file to the client computer. Double-click the file. After the disk image mounts to the file system, a Finder window opens with the contents of the package.
What is Check Point GO VPN?
It was previously called Mobile VPN. Check Point GO is a portable workspace with virtualized Windows applications, on a secure and encrypted USB Flash Drive. Users insert the USB device into a host PC and securely access their workspace and corporate resources via SSL VPN technology.
What is Check Point Mobile?
What is endpoint security suite?
Does Check Point Mobile support two factor authentication?
Is remote access a weak point?
Does Endpoint Security VPN include firewall?
See 2 more
About this website
What is Checkpoint VPN client?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
How do you check VPN on checkpoint?
0:0710:3510.Check Point Remote Access VPN. VPN users monitoring - YouTubeYouTubeStart of suggested clipEnd of suggested clipВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомнюMoreВозможно вы хотите оценить. Если у вас еще запас по подключением в рамках текущей лицензии напомню что лицензии конкурентной то есть они считают только. Одновременных подключений у вас может быть.
How do I update my Checkpoint VPN?
Below is a quick process to patch your computer and restore VPN/Endpoint connectivity.Validate if your Check Point VPN/EndPoint Client version is one of the following: ... If your client version is: Check Point Endpoint VPN E80. ... Reboot your machine.Click on EPPatcher_for_users.exe to install the patch.More items...
How do I install Checkpoint VPN client in Linux?
Downloading the Shell ScriptsLogin.Click on “Settings” button.Click on “Download Installation for Linux” for both SSL Network Extender and Check Point Mobile Access Portal Agent.
What type of VPN is Check Point?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I install Checkpoint VPN client?
Installation InstructionsStep 1: Download Checkpoint VPN E84.30. Download and save the VPN client installation file from this link. ... Step 2: Remove currently installed version. To uninstall the currently installed version of Check Point VPN Client: ... Step 3: Install new version.
What is Check Point Endpoint Security?
Check Point Endpoint Security™ is the first single agent for total endpoint security that combines the highest-rated firewall, network access control (NAC), program control, antivirus, anti-spyware, data security, and remote access.
How do I install Checkpoint endpoint security?
In the Installation Type window, select Security Gateway and/or Security Management....Installing an Endpoint Security Management Server.StepInstructions4On the General Properties page, click the Management tab.5Select the Endpoint Policy Management blade.6Click OK.7In the SmartConsole top left corner, click Menu > Install database.6 more rows
What is F5 VPN?
F5 Network's FirePass SSL VPN is an SSL VPN that provides broad application support, scalability, easy installation and use, and the highest standard of integrated end-point security.
How do I use Openswan?
Installing and Configuring OpenswanConnect to the EC2 instance and install Openswan. ... Edit the IPSec configuration file. ... Create a VPN configuration file: sudo nano /etc/ipsec.d/{vpnname}.conf. ... Create a Secrets File: sudo nano /etc/ipsec.d/{vpnname}.secrets. ... Start Openswan: sudo service ipsec start.More items...
What is remote secure access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
How check VPN tunnel status Checkpoint r80?
Click Logs & Monitor > New Tab. From the bottom of the window, click Tunnel and User Monitoring. Click the gateway to see IPsec VPN traffic and tunnels opened.
How do I connect to Checkpoint VPN?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How do I troubleshoot Checkpoint VPN?
Things to look for when troubleshooting a Checkpoint VPN connection:VPN domains. Review setup in the topology of an item. ... Encryption Domains. Your firewall contains your networks. ... Rule Setup. ... Pre-shared secret or certificate. ... RuleSet. ... Address Translation. ... TRADITIONAL MODE NOTES. ... SIMPLIFIED MODE NOTES.More items...•
How do I configure site to site VPN in Checkpoint r80?
0:0323:04Checkpoint R80.20 Training -IPSEC site to site Lab - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd welcome back to the checkpoint lab training for this video we'll be seeing ipsec side to sideMoreAnd welcome back to the checkpoint lab training for this video we'll be seeing ipsec side to side vpn. For that you have to follow some steps so that we can configure our ip6 the first step should be
Download checkpoint client for free (Windows)
This release, E75.10 Remote Access Clients, adds new features and two additional VPN Clients: Check Point Mobile for Windows and SecuRemote.... Remote Access Clients, adds new ... additional VPN Clients: Check Point ...
Check Point Capsule VPN for Windows 10 - CNET Download
Download Check Point Capsule VPN for Windows 10 for Windows to securely access all your corporate resources from your device through a VPN tunnel. Check Point Capsule VPN for Windows 10 has had 0 ...
E85.00 Check Point Remote Access VPN Clients for Windows
File Name: E85.00_CheckPointVPN.msi: Product: SecuRemote, Check Point Mobile, Endpoint Security VPN: Version: E85: OS: Windows: Build Number: MD5 ...
E83.10 Check Point Remote Access VPN Clients for Windows
File Name: E83.10_CheckPointVPN.msi: Product: SecuRemote, Check Point Mobile, Endpoint Security VPN: Version: E83: Minor Version: E83.10: OS: Windows: Build Number
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
Installation and Configuration
Before you install this release, make sure that you have supported gateways.
Automatic Upgrade from the Gateway
You can configure your Security Gateway to automatically upgrade Remote Access VPN clients the next time that they connect. When this occurs, the Security Gateway downloads the applicable package to the client. Endpoint users must have administrator permissions to install an upgrade.
What is Check Point Mobile?
Check Point Mobile for Windows is an IPsec VPN client. It is best for medium to large enterprises that do not require an Endpoint Security policy.
What is endpoint security suite?
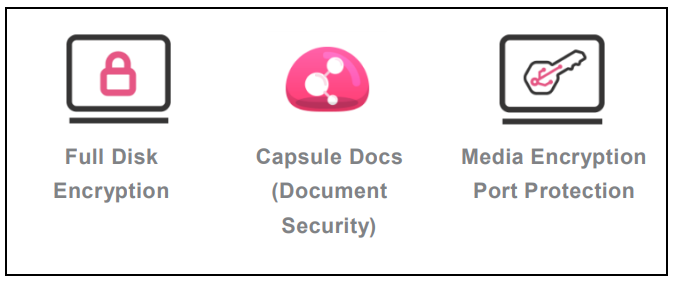
The Endpoint Security Suite simplifies endpoint security management by unifying all endpoint security capabilities in a single console and a single client. Endpoint Security Software Blades include: Desktop Firewall and Security Verification, Full Disk Encryption, Media Encryption and Port Protection, SandBlast Agent, Anti-Malware and Program Control, WebCheck browser virtualization and Remote Access VPN.
Does Check Point Mobile support two factor authentication?
Check Point Mobile for Windows, Check Point VPN Plugin for Windows 8.1 and Check Point Capsule VPN for Windows 10 do not support "two factor user authentication". (The limitation applies only to E80.64 and earlier in the context of Check Point Mobile for Windows.)
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
Does Endpoint Security VPN include firewall?
Note: Endpoint Security VPN for Mac OS X includes a Desktop Firewall, but not Security Verification.
What is Check Point Mobile?
Check Point Mobile for Windows is an IPsec VPN client. It is best for medium to large enterprises that do not require an Endpoint Security policy.
What is endpoint security suite?
The Endpoint Security Suite simplifies endpoint security management by unifying all endpoint security capabilities in a single console and a single client. Endpoint Security Software Blades include: Desktop Firewall and Security Verification, Full Disk Encryption, Media Encryption and Port Protection, SandBlast Agent, Anti-Malware and Program Control, WebCheck browser virtualization and Remote Access VPN.
Does Check Point Mobile support two factor authentication?
Check Point Mobile for Windows, Check Point VPN Plugin for Windows 8.1 and Check Point Capsule VPN for Windows 10 do not support "two factor user authentication". (The limitation applies only to E80.64 and earlier in the context of Check Point Mobile for Windows.)
Is remote access a weak point?
Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
Does Endpoint Security VPN include firewall?
Note: Endpoint Security VPN for Mac OS X includes a Desktop Firewall, but not Security Verification.