DMZ in a router is a function that allows you to open all external ports for a specific IP from the router's local network. Usually used to implement remote access to a specific device behind the router. Especially often DMZ is used to access from anywhere in the Internet to IP cameras or DVR, i.e. for video surveillance.
Full Answer
What is DMZ mode on Wi-Fi router?
Especially often DMZ is used to access from anywhere in the Internet to IP cameras or DVR, i.e. for video surveillance. Many Wi-Fi routers have the function of providing access from an external network to devices on their local network (DMZ host mode, it is also the exposed host).
How do I build a DMZ on a home network?
However, the router serves as both a connection point and a firewall, automating traffic filtering to ensure only safe messages enter the local area network. So, on a home network, a DMZ can built by adding a dedicated firewall, between the local area network and the router.
How do I deploy remote desktop services to a DMZ?
From Server Manager, you can find Remote Desktop Services on the left. In the Deployment Overview section, click the “plus” (+) symbol for RD Gateway. In the wizard, select the RDS server for your deployment (you could add a separate server for this role e.g. if you had another server deployed in a DMZ).
Is it safe to place items in a DMZ?
Placing any item in a DMZ that has access to your network especially to a domain can be dangerous. I would suggest using a 3rd party software (VPN clients) over using RDP. RDP has security flaws that could expose the network to possible intrusion. If you absolutely have to use RDP please review these items: 1.

What is a DMZ and why would we use it?
A DMZ Network is a perimeter network that protects and adds an extra layer of security to an organization's internal local-area network from untrusted traffic. A common DMZ is a subnetwork that sits between the public internet and private networks.
What is the difference between DMZ and firewall?
Simply, a DMZ is portion of your network carved off and isolated from the rest of your network. A firewall is the appliance that creates that isolation, by restricting traffic both between the intranet and the DMZ and the DMZ and other networks it's exposed to.
What happens if I enable DMZ?
Note: By enabling the DMZ (Demilitarized Zone) feature, you are allowing the router to forward all incoming traffic from the internet to the device specified, virtually disabling the routers "firewall protection". This may expose the device to a variety of security risks, so only use this option as a last resort.
Can DMZ access internal network?
The point of a DMZ is that connections from the internal and the external network to the DMZ are permitted, whereas connections from the DMZ are only permitted to the external network -- hosts in the DMZ may not connect to the internal network.
Are DMZ still used?
While most organizations no longer need a DMZ to protect themselves from the outside world, the concept of separating valuable digital goodies from the rest of your network is still a potent security strategy. If you apply the DMZ mechanism on an entirely internal basis, then there are still use cases that makes sense.
Do I need port forwarding with DMZ?
Relocating these services to the DMZ allows the admin to implement tighter security on the rest of the network. Additional firewalls are often put-up between the DMZ and the internal network. Port forwarding is not really essential and you can still use the internet without it.
When should I use DMZ?
DMZ networks are often used for the following: isolate and keep potential target systems separate from internal networks; reduce and control access to those systems by external users; and. host corporate resources to make some of them available to authorized external users.
Does DMZ slow Internet?
It should be noted that DMZ or DMZ Host does not improve the performance speed or latency of your router's connection to the server. It is simply a security measure (or lack of) that decides whether or not the devices is completely open to the internet.
What IP should I use for DMZ?
You should assign the DMZ host an IP address in the same subnet as the RV110W's LAN IP address, but it cannot be identical to the IP address given to the LAN interface of this gateway. To configure DMZ: Choose Networking > LAN > DMZ Host.
Is DMZ internal or external?
A DMZ, short for demilitarized zone, is a network (physical or logical) used to connect hosts that provide an interface to an untrusted external network – usually the internet – while keeping the internal, private network – usually the corporate network – separated and isolated form the external network.
What are the potential security risks of using DMZ?
In the event that a hacker gains entry to a file server in the DMZ, they may be able to access and download sensitive data and trading partner files that were placed there. Even encrypted files can be at risk to high-grade attackers if keys or passwords are compromised.
What is a DMZ in cybersecurity?
What is a DMZ Network? In computer security, a DMZ Network (sometimes referred to as a “demilitarized zone”) functions as a subnetwork containing an organization's exposed, outward-facing services. It acts as the exposed point to an untrusted networks, commonly the Internet.
Is DMZ behind firewall?
A network DMZ sits between two firewalls, creating a semisafe buffer zone between the internet and the enterprise LAN. If better-prepared threat actors pass through the first firewall, they must then gain unauthorized access to the services in the DMZ before they can do any damage.
What is the difference between DMZ and non DMZ?
DMZ, which stands for Demilitarized Zone, is an additional layer of security between the WAN and the LAN. A router with a DMZ subnet will allow access to the DMZ from the WAN while having the LAN still protected by the firewall.
How do I set my firewall to DMZ?
How to Configure a DMZConfigure the interface. Create a network segment (e.g., 172.16. ... Configure the access rule. Create an access rule that allows HTTP traffic from the Internet to the web server residing in the DMZ. ... Verify the order of the access rules. New rules are created at the bottom of the firewall rule set.
What is DMZ in a router?
The Demilitarized Zone (DMZ) is a feature that allows only one (1) local user to be exposed to the Internet for special purposes like Internet gaming or video conferencing.
What is a DMZ host?
What is DMZ and how to configure DMZ host? DMZ in a router is a function that allows you to open all external ports for a specific IP from the router's local network. Usually used to implement remote access to a specific device behind the router.
What is DMZ in video?
Especially often DMZ is used to access from anywhere in the Internet to IP cameras or DVR, i.e. for video surveillance. Many Wi-Fi routers have the function of providing access from an external network to devices on their local network (DMZ host mode, it is also the exposed host).
Can a DMZ host connect to internal network?
A DMZ host can freely connect to resources on the internal network, while connections to the internal network from the canonical DMZ are blocked by the firewall that separates them. In terms of security, the solution is not the best.
What is remote access?
Remote access is a relatively new capability for industrial control systems —one that comes with specific engineering and financial benefits. However, when considering new remote access connections, organizations need to involve the necessary stakeholders to make security and reliability-based decisions.
What are remote access requirements?
Remote access requirements should be determined, including what IP addresses, what communication types, and what processes can be monitored. All others should be disabled by default. Remote access including process control should be limited as much as possible.
Do not enable remote access?
First and foremost, do not enable remote access by default. This is not a strict anti-remote access stance— rather a pro-engineering discussion. Because remote access is a “gate” through the (hopefully robust) perimeter and moat and walls of your fort, you want to make sure it is secure. This requires multiple stakeholders to be involved, including OT security, IT security, engineering, vendors, and any maintenance support teams. It is not something that is easily pre-packaged and it is never a “set it and forget it” capability.
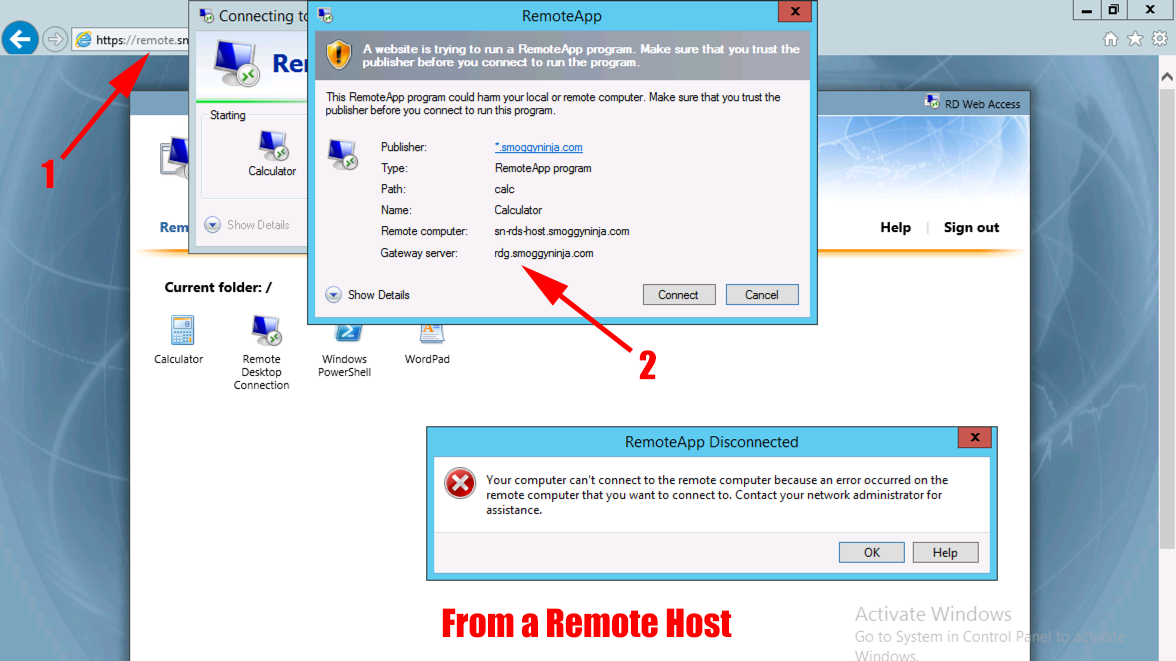
What is a DMZ in remote desktop?
In the Enterprise, we’d most likely see RDS deployed using a “DMZ” or “Demilitarized Zone,” which is a special type of network, that usually contains some internet-accessible resources, ...
How to activate RDS user cal?
The first step will be activating the server. From Server Manager, go to Tools > Remote Desktop Licensing Manager. Right-click on the server and go to Activate Server. Complete the Wizard.
How to deploy RDS?
To deploy RDS in either manner, you will be able to start with the Windows Server Remote Desktop Services “Quick Start” deployment. The server should already have a static IP address, be named and joined to the domain. From Server Manager > Add Roles and Features . Select Remote Desktop Services installation. Then choose Quick Start.
What is the role of web access?
The first is the Web Access role. Using the Web Access page, you can publish applications (some will be published by default) that will be launched via RemoteApp (these apps run from the Remote Desktop server, but do not require a full Desktop to be presented).
How to rename remote web access?
Typically the link in the Remote Web Access page will take on the name of your collection, so I usually rename my collection to something like “ Desktop ” ( Properties > Tasks > Edit Properties ). If you do go into that Edit Properties area, you will have an opportunity to configure a bunch of other options such as Idle session limits, and others.
Can you leave remote apps published?
It is also possible to leave the RemoteApps published, publish additional apps, and also maintain full desktop access using this method. Tweak all the session collection settings, install whatever RemoteApps you need, and test everything out before releasing to the end-users.
Can a client restrict access to a specific network resource?
Furthermore, we have the ability to restrict clients to specific network resources, or even specify different resources by group memberships. When clients connect, they receive an IP address in a specified range, and that range can be treated a lot like a DMZ, with very specific access granted/denied to the internal (trusted) network.