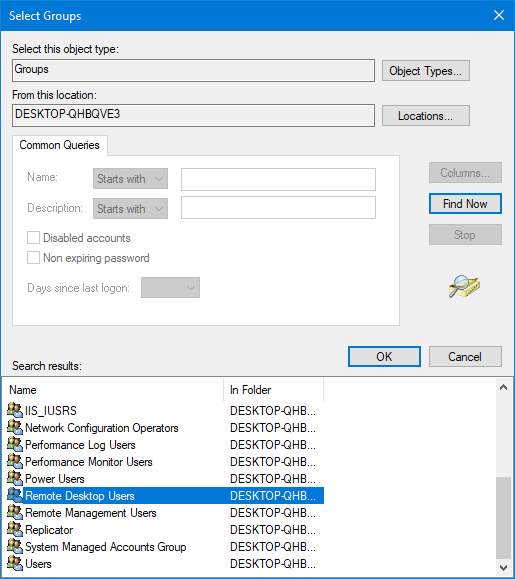
Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment. Find and double-click "Deny logon through Remote Desktop Services". Add the user and / or the group that you would like to deny access.
How do I grant or deny access to all local accounts?
These SIDs can grant access or deny access to all local accounts or all administrative local accounts. For example, you can use these SIDs in User Rights Assignments in Group Policy to "Deny access to this computer from the network" and "Deny log on through Remote Desktop Services."
How do I deny a user from logging in via RDP?
If you change the Windows Server 2008 server to Remote Desktop Services Application Mode by installing the role, this user won't be denied logon via RDP. To deny a user or a group logon via RDP, explicitly set the "Deny logon through Remote Desktop Services" privilege.
Why was my connection denied because the account is not authorized?
The error ‘The connection was denied because the user account is not authorized for remote login’ typically occurs when the user account that you are using to remotely connect to the target system doesn’t have sufficient permissions. This error has occurred to many users in the past as well and it seems like Windows 10 is no exception to it.
How do I restrict access to a user through Remote Desktop Services?
Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment. Find and double-click "Deny logon through Remote Desktop Services". Add the user and / or the group that you would like to deny access.

How do I deny remote access permissions?
Windows 8 and 7 InstructionsClick the Start button and then Control Panel.Open System and Security.Choose System in the right panel.Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab.Click Don't Allow Connections to This Computer and then click OK.More items...•
How do I disable remote login?
How to disable Remote Desktop Access for Administrators PrintPress Win+R.Type secpol.msc and hit Enter:Navigate to: Security Settings\Local Policies\User Rights Assignment. ... Click Add User or Group:Click Advanced:Click Find Now:Select the user you want to deny access via Remote Desktop and click OK:Click OK here:More items...•
How do I fix user is not authorized for remote login?
Now go to Local Policies > User Rights Assignment. On your right-hand side, you should find a policy named Allow log on through Remote Desktop Services. Double-click on this policy to open the Properties. If you cannot find Remote Desktop Users under Administrator, you need to add it.
How do I authorize a user for remote login?
Allow Access to Use Remote Desktop ConnectionClick the Start menu from your desktop, and then click Control Panel.Click System and Security once the Control Panel opens.Click Allow remote access, located under the System tab.Click Select Users, located in the Remote Desktop section of the Remote tab.More items...•
Can I disable Remote Access Connection Manager?
Double-click Remote Access Connection Manager. In the Startup type list, click Disabled. Click Stop, and then click OK.
What is remote accessing?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
How do I allow login through Terminal Services?
Start > Run > gpedit. msc. Expand: Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Management. Select: Allow log on through Remote Desktop Services.
Why Remote Desktop is not working?
Check firewalls, security certificates and more if a remote desktop is not working. When the remote desktop connection between a Windows desktop and its host fails, it's time to do some remote desktop troubleshooting by checking firewalls, security certificates and more.
Can't connect to VPN the remote connection was denied?
Can't connect to VPN the remote connection was denied? The most common fix when using a VPN connection is to change the settings on your VPN connection to allow Microsoft CHAP Version 2. This setting is found in Properties panel of the VPN connection. Go to Security tab and check the box.
What permissions do remote desktop users have?
By default, the Remote Desktop Users group is assigned the following permissions: Query Information, Logon, and Connect.
How do I get remote access to my computer?
How Can I Remotely Access Another Computer For Free?the Start Window.Type in and enter remote settings into the Cortana search box.Select Allow Remote PC access to your computer.Click the Remote tab on the System Properties window.Click Allow remote desktop connection Manager to this computer.More items...•
Is my phone being remotely accessed?
How to Tell Someone Is Accessing Your Phone Remotely. Here are some signs that someone might have unauthorized access to your smartphone: Unknown apps are running in the background. Your phone has an increased closing time and is slower overall.
How do I stop Remote Assistance session?
Note: Although you relinquish control of your computer temporarily, you retain control over the Remote Assistance session itself. You can end the session immediately by clicking the Stop Control button (or pressing the ESC key).
How do I disable remote desktop in Chrome?
Remove Chrome Remote DesktopGo to Control Panel Programs Add/Remove Programs.Find the "Chrome Remote Desktop" application.Click Remove.
How can deactivate remote configuration in Mobile?
0:351:32Samsung Galaxy S9: How to Enable / Disable Remote Controls (Find My ...YouTubeStart of suggested clipEnd of suggested clipAnd then tap on the ok button right. Here once you put in the password for that account you can thenMoreAnd then tap on the ok button right. Here once you put in the password for that account you can then tell a little control to turn it on or off.
What is Deny Log On through Remote Desktop Services Policy?
The Deny log on through Remote Desktop Services policy allows specifying users and groups that are explicitly denied to logon to a computer remotely via Remote Desktop. We can deny RDP access to the computer for local and domain accounts.
How to deny remote desktop access?
Deny Remote Desktop (RDP) Access for Local Users and Administrators 1 First, we open the local GPO editor gpedit.msc (if we want to apply these settings on computers in the Active Directory domain, use the domain Group Policy Editor – gpmc.msc). 2 Then we go to the GPO section User Rights Assignment and edit the Deny log on through Remote Desktop Services policy.
How to block remote access to a network?
For that, we use the settings from the GPO section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment.
Who can access RDP?
By default, RDP access on Windows is allowed for the administrators and members of the local Remote Desktop User group.
When are groups added to access token?
These groups are added to the user’s access token during logon to the computer under a local account.
Can administrators rename the default local Windows administrator account?
To reduce the risk, administrators can rename the default local Windows Administrator account.
What account was denied remote access on all domain computers through a GPO?
In our example, the account named USER01 was denied remote access on all domain computers through a GPO.
How to link a GPO to a group policy?
On the Group policy management screen, you need to right-click the Organizational Unit desired and select the option to link an existent GPO.
Why should user ID be enabled on an untrusted zone?
If User-ID and WMI probing are enabled on an external untrusted zone (such as the Internet), probes could be sent outside your protected network, resulting in an information disclosure of the User-ID Agent service account name, domain name, and encrypted password hash . This information has the potential to be cracked and exploited by an attacker to gain unauthorized access to protected resources. For this important reason, User-ID should never be enabled on an untrusted zone.
How to prevent unwanted traffic?
Prevent any unwanted traffic (including potentially unwanted User-ID Agent traffic) from leaving your protected networks out to the Internet by implementing egress filtering on perimeter firewalls. In sensitive environments, white listing trusted and business essential applications diminishes the possibility of allowing unwanted traffic, and also helps reduce possible vectors that could be used to exfiltrate data.
Can a service account be a member of a security group?
Typically, service accounts should not be members of any security groups that are used to grant remote access. If the User-ID service account credentials were to be compromised, this would prevent the attacker from using the account to gain access to your network from the outside using a VPN.
Symptoms
You may notice that the behavior of the Deny this user permissions to logon to a Remote Desktop Session Host Server is different between Windows Server 2003 and Windows Server 2008. In Windows Server 2003, this setting is called Deny this user permission to logon to any Terminal Server.
Cause
This behavior is by design. In Windows Server 2003, this setting is checked no matter whether the server is in Remote Administration Terminal Server mode or Application Terminal Server mode. However, in Windows Server 2008 this setting is checked on a machine that has Remote Desktop Services in Application Mode only.
Resolution
To deny a user or a group logon via RDP, explicitly set the "Deny logon through Remote Desktop Services" privilege. To do this, access a group policy editor (either local to the server or from a OU) and set this privilege:
Why is my connection denied?
The error ‘ The connection was denied because the user account is not authorized for remote login ’ typically occurs when the user account that you are using to remotely connect to the target system doesn’t have sufficient permissions. This error has occurred to many users in the past as well and it seems like Windows 10 is no exception to it. Upon trying to establish a connection, users have reported that they are prompted with the said error message.
How to restart a service?
Restart the service by right-clicking the service and selecting Restart.
What to do if you are installing Windows based user ID agent on a supported server?
If you are installing the Windows-based User-ID agent on a supported Windows server, Configure a Service Account for the Windows User-ID Agent .
What is a user ID agent?
The User-ID agent maps users based on logs for security events. To ensure that the User-ID agent can successfully map users, verify that the source for your mappings generates logs for Audit Logon, Audit Kerberos Authentication Service, and Audit Kerberos Service Ticket Operations events. At a minimum, the source must generate logs for the following events:
What are the required permissions for a service account?
The required permissions for the service account depend on the user mapping methods and settings you plan to use. For example, if you are using the PAN-OS integrated User-ID agent, the service account requires Server Operator privileges to monitor user sessions. If you are using the Windows-based User-ID agent, the service account does not require Server Operator privileges to monitor user sessions. To reduce the risk of compromising the User-ID service account, always configure the account with the minimum set of permissions necessary for the agent.
How to use Server Monitoring to identify users?
If you want to use Server Monitoring to identify users, add the service account to the Event Log Reader builtin group to allow the service account to read the security log events.
Why can only Vsys1 join a domain?
For a firewall with multiple virtual systems, only vsys1 can join the domain because of AD restrictions on virtual systems running on the same host. The PAN-OS integrated agent requires privileged operations to join the domain, which poses a security threat if the account is compromised.
What is the purpose of ensuring that the User-ID service account has the minimum set of account privileges?
By ensuring that the User-ID service account has the minimum set of account privileges, you can reduce the attack surface should the account be compromised.
Where is the permission to log on as a service needed?
The permission to log on as a service is only needed locally on the Windows server that is the agent host.
Why is it suspicious to have a service account logged in?
Because service accounts are often left alone to run services without the need of an end user, it becomes highly suspicious when a service account is logged in by a human user. This creates an insider threat from a trusted credential used by many different services and applications.
What happens if an attacker accesses a service account?
If attackers access a service account, they can indirectly access all the resources to which that service account has access to. Users given the role of a service account user can use those credentials to access all resources tied to the account, and potentially impersonating the service account to perform many tasks using those elevated roles and permissions. Essentially, an attacker can go completely unnoticed within your network and steal or manipulate your Active Directory (AD) domain — the metaphorical keys to the kingdom.
How to protect against service account insider threat?
One way to protect against service account insider threat via interactive logins is through the AD group policy. You can create a special security group (GPO) in AD to identify users that you want to run services but not allow any interactive login to a machine in your domain. Creating a group that prevents direct access to a system is one way to mitigate the problem, but unfortunately does not provide enough restrictions to fully protect against interactive logins.
What is the difference between a service account and an end user account?
Service accounts differ from end-user accounts in that they usually have higher privileges that are used to control or call applications, APIs and services. As a result, looking for key indicators of compromise (IOCs) among your service accounts should be at the forefront of your network security strategy. Service accounts, when compromised, can become the most dangerous insider threat of all.
How to do interactive login?
Interactive login is authentication to a computer through the usage of their local user account or by their domain account, usually by pressing the CTRL+ALT+DEL keys (on a Windows machine). When the user is logged in, Windows will run applications on behalf of the user and the user can interact with those applications. Interactive login is usually performed locally where the user has direct physical access to the machine or through Terminal Services, which the user can perform a remote login, often called “remote interactive login.” This page describes Microsoft local and domain interactive login.
How to know if your service account is vulnerable to compromise?
The best way to understand if your service accounts are vulnerable to compromise is simply to understand where all of your service accounts are in your network and limiting those accounts from performing an interactive login.
Why are service accounts important?
Service accounts are especially important because they are often installed under the intrinsic local system account and essentially have local administrator privileges. These privileges could potentially give account access to domain credentials and allow them to laterally move within your network.
Why is UAC not allowed on WinRM?
Because of User Account Control (UAC), the remote account must be a domain account and a member of the remote computer Administrators group. If the account is a local computer member of the Administrators group, then UAC does not allow access to the WinRM service.
Is default administrator account a workaround?
Using default Administrator account is a workaround, but not a solution.
Can a password be blank?
As others have mentioned, you must set a password for Administrator and it cannot be blank.
Does UAC allow access to WinRM?
If the account is a local computer member of the Administrators group, then UAC does not allow access to the WinRM service. To access a remote WinRM service in a workgroup, UAC filtering for local accounts must be disabled by creating the following DWORD registry entry and setting its value to 1: ...