Group Policy When the remote user has established the VPN, he or she will be unable to access anything on the Internet…only the remote network is reachable. For security reasons this is a good practice as it forces you to send all traffic through the ASA. If you don’t want this then you can enable split tunneling.
Full Answer
How does the ASA select the connection profile for a VPN?
In addition, for L2TP/IPsec clients only, when you specify the strip-group command the ASA selects the connection profile (tunnel group) for user connections by obtaining the group name from the username presented by the VPN client.
How to configure PPP for ASA 5505 in client mode?
For ASA 5505 in client mode, the URL must be of the form tftp://. To configure the authentication protocols permitted for a PPP connection using this IKEv1 Connection Profile, open Configuration > Remote Access VPN > Network (Client) Access > IPsec (IKEv1) Connection Profiles > Add/Edit > Advanced > PPP.
How do I configure a group policy for remote access VPN?
On the Configuration > Remote Access VPN > Network (Client) Access > Group Policies pane, the Add or Edit Group Policy dialog box lets you specify tunneling protocols, filters, connection settings, and servers for the group policy being added or modified.
How do I configure a VPN Group Policy in ASDM?
Start ASDM and choose Configuration > Remote Access VPN > AAA/Local Users > Local Users. Select the user you want configure and click Edit. In the left-hand pane, click VPN Policy. Specify a group policy for the user.
What is group policy in Cisco ASA?
Summary. The Cisco ASA firewall includes the ability to assign a user to a group policy based on their OU group. This is achieved via the use of the IETF RADIUS Attribute 25. This attribute contains the users OU and is sent by the Radius server (to the ASA) during the RADIUS Authentication and Authorization process.
How to check tunnel group from ASA?
Understanding how ASA Firewall matches Tunnel-Group Names Using the IKE ID presented by the remote peer. ... Using the OU (Organization Unit) field from the DN found in digital certificate presented by the peer OR by using the certificate mapping rules. ... Using the remote endpoint's IP address.
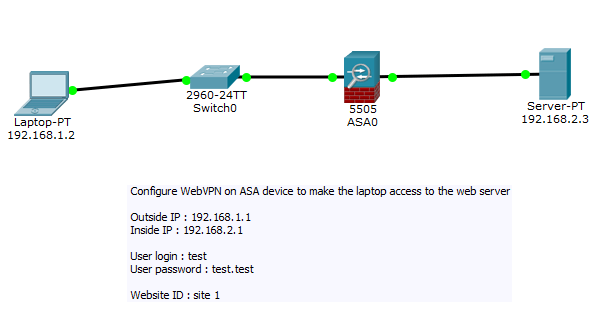
How do I enable WebVPN in Asa?
Now we can enable client WebVPN on the outside interface: ASA1(config-webvpn)# enable outside INFO: WebVPN and DTLS are enabled on 'OUTSIDE'. Remote users will get an IP address from the pool above, we'll use IP address range 192.168. 10.100 – 200.
How do I add a profile to AnyConnect secure mobility client?
Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile. Choose Add. Give the profile a name. Choose the Umbrella Security Roaming Client type from the Profile Usage drop-down list.
How do I check my VPN traffic on ASA?
First the I run the command: “show crypto isakmp sa”. This will give me a list of all the VPN tunnels and their peer IP address. The main lines that we are looking at are the “packets encaps” and “packets decaps”. The packets encapsulated are the packets you are pushing into the VPN.
What is VPN tunnel group?
Tunnel groups are the part of EzVPN technology. When you configure your VPN this way you are allways providing group-name/password or certificate with mapping data to group. At the site to site (or lan to lan) VPN usually uses a crypto maps with IPSec profiles without tunnel groups.
What is WebVPN on ASA?
WebVPN (or often called SSL VPN) (or sometimes called clientless VPN) is used when someone needs to access a web based application that is on the private network. A web browser is used for all the encryption and authentication.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is Sysopt connection permit VPN?
The sysopt connection permit-vpn command allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists, while a vpn-filter is applied to postdecrypted traffic after it exits a tunnel and to preencrypted traffic before it enters a tunnel.
How do I add VPN details to Cisco AnyConnect?
InstallUninstall any previous versions of Cisco AnyConnect.Install Cisco AnyConnect app from the Apple App Store or Google Play Store.Open the Cisco AnyConnect app.Select Add VPN Connection.Enter a Description, for example, CMU VPN and the Server Address vpn.cmu.edu.If prompted, allow the changes.Click Save.
How do I change my AnyConnect VPN profile?
Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles. Select the AnyConnect VPN profile in Connection Profiles and click Edit. The Edit AnyConnect Connection Profile window is displayed. Set the Method as AAA in the Authentication.
Where are the AnyConnect profiles stored?
Resolution:Operating SystemLocationWindows 8%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileWindows 10%ProgramData%\Cisco\Cisco AnyConnect Secure Mobility Client\ProfileMac OS X/opt/cisco/anyconnect/profileLinux/opt/cisco/anyconnect/profile3 more rows•Apr 27, 2022
What is WebVPN account?
Previous page. WebVPN is an evolving method to establish remote-access VPN tunnels without having to install the Cisco VPN Client. A VPN user establishes the secure connection to the Cisco ASA by using a web browser such as Internet Explorer, Netscape, or FireFox.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
What is a group VPN?
Groups and users are core concepts in managing the security of virtual private networks (VPNs) and in configuring the ASA. They specify attributes that determine user access to and use of the VPN. A group is a collection of users treated as a single entity. Users get their attributes from group policies. A connection profile identifies the group policy for a specific connection. If you do not assign a particular ✪ group policy to a user, the default group policy for the connection applies.
How do external group policies work?
External group policies take their attribute values from the external server that you specify. For an external group policy, you must identify the AAA server group that the ASA can query for attributes and specify the password to use when retrieving attributes from the external AAA server group. If you are using an external authentication server, and if your external group-policy attributes exist in the same RADIUS server as the users that you plan to authenticate, you have to make sure that there is no name duplication between them.
What is IPsec over UDP?
IPsec over UDP, sometimes called IPsec through NAT , lets a Cisco VPN client or hardware client connect via UDP to a ASA that is running NAT. It is disabled by default. IPsec over UDP is proprietary; it applies only to remote-access connections, and it requires mode configuration. The ASA exchanges configuration parameters with the client while negotiating SAs. Using IPsec over UDP may slightly degrade system performance.
What is LAN to LAN VPN?
An IPsec LAN-to-LAN VPN connection profile applies only to LAN-to-LAN IPsec client connections. While many of the parameters that you configure are the same as for IPsec remote-access connection profiles, LAN-to-LAN tunnels have fewer parameters. The following sections show you how to configure a LAN-to-LAN connection profile:
How does a firewall protect a computer?
firewall isolates and protects a computer from the Internet by inspecting each inbound and outbound individual packet of data to determine whether to allow or drop it . Firewalls provide extra security if remote users in a group have split tunneling configured. In this case, the firewall protects the user’s PC, and thereby the corporate network, from intrusions by way of the Internet or the user’s local LAN. Remote users connecting to the ASA with the VPN client can choose the appropriate firewall option.
What is double authentication?
Double authentication is an optional feature that requires a user to enter an additional authentication credential, such as a second username and password, on the login screen. Specify the following commands to configure double authentication.
What is a connection profile?
connection profile consists of a set of records that determines tunnel connection policies. These records identify the servers to which the tunnel user is authenticated, as well as the accounting servers, if any, to which connection information is sent. They also identify a default group policy for the connection, and they contain protocol-specific connection parameters. Connection profiles include a small number of attributes that pertain to creating the tunnel itself. Connection profiles include a pointer to a group policy that defines user-oriented attributes.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Is Mobike available on ASA?
Mobike is available by default on ASAs since version 9.8 (1), meaning Mobike is “always on.” Mobike is enabled for each SA only when the client proposes it and the ASA accepts it. This negotiation occurs as part of the IKE_AUTH exchange.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What version of ASA is AnyConnect?
The ASA supports the AnyConnect client firewall feature with ASA version 8.3 (1) or later, and ASDM version 6.3 (1) or later. This section describes how to configure the client firewall to allow access to local printers, and how to configure the client profile to use the firewall when the VPN connection fails.
What is DPD in ASA?
Dead Peer Detection (DPD) ensures that the ASA (gateway) or the client can quickly detect a condition where the peer is not responding, and the connection has failed. To enable dead peer detection (DPD) and set the frequency with which either the AnyConnect client or the ASA gateway performs DPD, do the following:
What is ACL AnyConnect_Client_Local_Print?
The ACL AnyConnect_Client_Local_Print is provided with ASDM to make it easy to configure the client firewall. When you choose that ACL for Public Network Rule in the Client Firewall pane of a group policy, that list contains the following ACEs:
How long do you have to notify ASDM before password expiration?
The range is 1 through 180 days.
How to configure customization for a group policy?
To configure customization for a group policy, choose a preconfigured portal customization object, or accept the customization provided in the default group policy. You can also configure a URL to display.
What is external group policy?
External group policies retrieve attribute values authorization and authentication from an external server. The group policy identifies the RADIUS or LDAP server group that the ASA can query for attributes, and specifies the password to use when retrieving those attributes.
What is a group policy?
A group policy is a collection of user-oriented attribute/value pairs stored either internally on the ASA or externally on a RADIUS or LDAP server. A group policy assigns attributes to a client when the establish a VPN connection. By default, VPN users have no group policy association.
What is a VPN group?
Groups and users are core concepts in managing the security of virtual private networks (VPNs) and in configuring the security appliance. They specify attributes that determine user access to and use of the VPN. A group is a collection of users treated as a single entity. Users get their attributes from group policies. Tunnel groups identify the group policy for a specific connection. If you do not assign a particular group policy to a user, the default group policy for the connection applies.
How do external group policies work?
External group policies take their attribute values from the external server that you specify. For an external group policy, you must identify the AAA server group that the security appliance can query for attributes and specify the password to use when retrieving attributes from the external AAA server group. If you are using an external authentication server, and if your external group-policy attributes exist in the same RADIUS server as the users that you plan to authenticate, you have to make sure that there is no name duplication between them.
How does WebVPN work?
WebVPN lets users establish a secure, remote-access VPN tunnel to the security appliance using a web browser. There is no need for either a software or hardware client. WebVPN provides easy access to a broad range of web resources and web-enabled applications from almost any computer that can reach HTTPS Internet sites. WebVPN uses SSL and its successor, TLS1, to provide a secure connection between remote users and specific, supported internal resources that you configure at a central site. The security appliance recognizes connections that need to be proxied, and the HTTP server interacts with the authentication subsystem to authenticate users. By default, WebVPN is disabled.
What is LAN to LAN VPN?
An IPSec LAN-to-LAN VPN tunnel group applies only to LAN-to-LAN IPSec client connections. While many of the parameters that you configure are the same as for IPSec remote-access tunnel groups, LAN-to-LAN tunnels have fewer parameters. To configure a LAN-to-LAN tunnel group, follow the steps in this section.
What is IPSec over UDP?
IPSec over UDP, sometimes called IPSec through NAT, lets a Cisco VPN client or hardware client connect via UDP to a security appliance that is running NAT. It is disabled by default. IPSec over UDP is proprietary; it applies only to remote-access connections, and it requires mode configuration. The security appliance exchanges configuration parameters with the client while negotiating SAs. Using IPSec over UDP may slightly degrade system performance.
How does a firewall protect a computer?
A firewall isolates and protects a computer from the Internet by inspecting each inbound and outbound individual packet of data to determine whether to allow or drop it. Firewalls provide extra security if remote users in a group have split tunneling configured. In this case, the firewall protects the user's PC, and thereby the corporate network, from intrusions by way of the Internet or the user's local LAN. Remote users connecting to the security appliance with the VPN client can choose the appropriate firewall option.
What command enforces complex passwords?
To enforce complex passwords—for example, to require that a password contain upper- and lowercase letters, numbers, and special characters—specify the password-management command in tunnel-group general-attributes configuration mode on the security appliance and do the following steps under Active Directory:
What is a group VPN?
Groups and users are core concepts in managing the security of virtual private networks (VPNs) and in configuring the ASA. They specify attributes that determine user access to and use of the VPN. A group is a collection of users treated as a single entity. Users get their attributes from group policies. A connection profile identifies the group policy for a specific connection. If you do not assign a particular group policy to a user, the default group policy for the connection applies.
What is a realm in ASA?
A realm is an administrative domain. If you strip the realm, the ASA uses the username and the group (if present) authentication. If you strip the group, the ASA uses the username and the realm (if present) for authentication. Enter the strip-realm command to remove the realm qualifier, and use the strip-group command to remove the group qualilfier from the username during authentication. If you remove both qualifiers, authentication is based on the username alone. Otherwise, authentication is based on the full username@realm or username <delimiter> group string. You must specify strip-realm if your server is unable to parse delimiters.
How long can a group policy name be?
The name of the group policy can be up to 64 characters long. The following example sets DfltGrpPolicy as the name of the default group policy:
What is double authentication?
Double authentication is an optional feature that requires a user to enter an additional authentication credential, such as a second username and password, on the login screen. Specify the following commands to configure double authentication.
How long can an accounting server name be?
The name of the accounting server group can be up to 16 characters long. For example, the following command specifies the use of the accounting-server group named comptroller:
How long can a server name be?
The name of the authorization server group can be up to 16 characters long. For example, the following command specifies the use of the authorization-server group FinGroup:
What is a connection profile?
A connection profile consists of a set of records that determines tunnel connection policies. These records identify the servers to which the tunnel user is authenticated, as well as the accounting servers, if any, to which connection information is sent. They also identify a default group policy for the connection, and they contain protocol-specific connection parameters. Connection profiles include a small number of attributes that pertain to creating the tunnel itself. Connection profiles include a pointer to a group policy that defines user-oriented attributes.