Methods To Access CRIS: There are two ways to log onto the NIH network remotely (outside the NIH campus): 1. PIV card Prerequisite: PIV reader and software Insert your PIV card into the card reader. You will need to enter your NIH username and PIV password Go to CC Citrix Access
Full Answer
What is cis critical security control 6 access control?
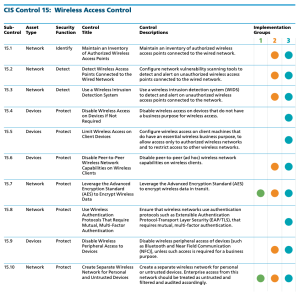
CIS Critical Security Control 6: Access Control Management Overview Use processes and tools to create, assign, manage, and revoke access credentials and privileges for user, administrator, and service accounts for enterprise assets and software. CIS Controls v8 and Resources
What are the available remote desktop applications for CS?
For Linux there are a few Remote Desktop Applications, including KRDC and Remmina, which are both installed on the CS Systems. Remote Linux Access CS users have access to the department's public Linux shell server form anywhere, on- or off-campus.
What is included in the Citrix remote access links?
Included are links to read your email remotely, get technical support, medical staff links, and more. DMC employees and partners can use these links to access their email, Citrix platforms, etc. Use these links to get technical support, at work or remotely.
How to access Cris from anywhere?
II. Methods To Access CRIS: There are two ways to log onto the NIH network remotely (outside the NIH campus): 1. PIV card. Prerequisite: PIV reader and software; Insert your PIV card into the card reader. You will need to enter your NIH username and PIV password; Go to the "CCCasper Citrix Access" website; 2. Virtual Private Network (VPN) Access
What is Citrix for SPU?
What is remote desktop connection?
What is VPN-PRIVDATA?
What is SPU VPN?
What is Fortinet VPN?
About this website
What is CIS stands for in IoT?
CIS Critical Security Controls (Version 6): IoT Security.
Is CIS control free?
Yes, the CIS Controls are free to use by anyone to improve their own cybersecurity.
What does CIS stand for compliance?
The Center for Internet Security (CIS) benchmarks are a set of best-practice cybersecurity standards for a range of IT systems and products. CIS Benchmarks provide the baseline configurations to ensure compliance with industry-agreed cybersecurity standards.
Is CIS cyber security?
Contents. The CIS Critical Security Controls are a prioritized set of actions for cybersecurity that form a defense-in-depth set of specific and actionable best practices to mitigate the most common cyber attacks.
Should I use CIS or NIST?
NIST CSF and CIS V8 frameworks are complementary. The core difference is that CIS V8 is more prescriptive, whereas NIST CSF provides more security objectives that you can reach at your own pace (compared to CIS-specific implementation groups).
Who uses CIS Controls?
Who uses CIS Controls? Thousands of organizations of all sizes use CIS Controls, which have been downloaded more than 70,000 times as of May 1, 2017. The state governments of Arizona, Colorado and Idaho have officially adopted them, as have the cities of Oklahoma City, Portland and San Diego among many others.
What is the purpose of CIS Controls?
The CIS Controls (formerly known as Critical Security Controls) are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today's most pervasive and dangerous attacks.
What are the top 20 CIS Controls?
The Center for Internet Security (CIS) Top 20 Critical Security Controls (previously known as the SANS Top 20 Critical Security Controls), is a prioritized set of best practices created to stop the most pervasive and dangerous threats of today.
What are the basic CIS Controls?
What Are the 6 Basic CIS Controls?Inventory and Control of Hardware Assets. ... Continuous Vulnerability Management. ... Controlled Use of Administrative Privileges. ... Configuration for Hardware and Software on Mobile Devices, Laptops and Servers. ... Maintenance, Monitoring and Analysis of Audit Logs.
Who owns CIS security?
Disclaimer: The views in this interview are those of Ken Palmer, and are not representative of Infologue or associated businesses. CIS is on the brink of an impressive 50 years in the security business.
Is CIS a control framework?
For businesses, leveraging a framework like CIS Controls makes sure your company and customer data stay safe. You want to use trusted security and privacy frameworks for your business and we think the controls in the CIS framework are an excellent fit for many businesses or even startups.
Why is CIS important?
CIS benchmarks provide a clear set of standards for configuring common digital assets — everything from operating systems to cloud infrastructure. This removes the need for each organization to 'reinvent the wheel' and provides organizations with a clear path to minimizing their attack surface.
What are CIS Controls?
The CIS Controls (formerly known as Critical Security Controls) are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today's most pervasive and dangerous attacks.
How do I use CIS Controls?
Step 1: Take inventory of your assets. ... Step 2: Measure asset controls. ... Step 3: Perimeter defenses. ... Step 4: Detect and respond to incidents. ... Step 5: Evaluate the most critical gaps. ... Step 6: Plan and implement your controls. ... Train and monitor users. ... Test your controls.
How many CIS Controls exist?
Formerly the SANS Critical Security Controls (SANS Top 20) these are now officially called the CIS Critical Security Controls (CIS Controls). CIS Controls Version 8 combines and consolidates the CIS Controls by activities, rather than by who manages the devices.
Why are there 20 controls in CIS?
The CIS CSC is a set of 20 controls (sometimes called the SANS Top 20) designed to help organizations safeguard their systems and data from known attack vectors. It can also be an effective guide for companies that do yet not have a coherent security program.
CIS Controls Navigator
Use this page to learn more about the Controls and Safeguards and see how they map to other security standards. Click on a row to see all related, applicable standards.
Mappings - (0)
AC.1.001 Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
What is remote desktop connection?
Remote Desktop Connections allow employees to login to on-campus desktop devices from home or other remote locations. This must be enabled individual per user and computer. Please read here for more details: Remote Desktop Connection.
What is Citrix for SPU?
Citrix is an online service for Faculty and Staff that allows you to access your SPU My Documents, Departmental File Shares, and other SPU specific applications from a personal device with internet access. Citrix can also be used to connect to your on-campus desktop device.
What is CIS Control 6?
CIS Control 6 merges some aspects of CIS Control 4 (admin privileges) and CIS Control 14 (access based on need to know) into a single access control management group. Access control management is a critical component in maintaining information and system security, restricting access to assets based on role and need. It is important to grant, refuse, and remove access in a standardized, timely, and repeatable way across an entire organization. Privileged accounts, such as administrators, should be protected with multi-factor authentication. Enforcing and maintaining access control policies can be made significantly less painful with automated tools. In the same vein as protecting data assets, users and service accounts are also assets that need to be protected.
What is CIS benchmark?
CIS Benchmarks, which are available for many product families, are best-practice security configuration guides that are mapped to the controls and walk you through configuration remediation step-by-step.
What is role based access control?
Description: Define and maintain role-based access control, through determining and documenting the access rights necessary for each role within the enterprise to successfully carry out its assigned duties. Perform access control reviews of enterprise assets to validate that all privileges are authorized on a recurring schedule at a minimum annually, or more frequently.
What is a disabling account?
Description: Establish and follow a process, preferably automated, for revoking access to enterprise assets through disabling accounts immediately upon termination, rights revocation, or role change of a user. Disabling accounts instead of deleting accounts may be necessary to preserve audit trails.
How to login to remote desktop?
To login to Remote Desktop, you must use your eID and your eID password ( This is the same password used for KSIS and Webmail). You also must add the USERS domain as a prefix for username, USERSyour_eID. There is no longer a distinction between CS users and Non-CS users, all users must use the eID password to log in.
What ports does KSU guestwireless allow?
This network only allows web traffic on ports 80 & 443 (http/https) and nothing else.
What is remote desktop?
Remote Desktop Programs. Microsoft has a remote desktop application that has support on Windows, Mac, ChromeOS, iOS, and Android, that can be found in the respective store or Here . For Linux there are a few Remote Desktop Applications, including KRDC and Remmina, which are both installed on the CS Systems.
What is the host name for remote Mac?
After opening one of these applications you will just need to enter the the host name, which is remote-mac.cs.ksu .eduand your CS username and password.
Do you need a VPN to connect to remote desktop?
If you are connecting from off-campus, you must be connected to the campus VPN before you can connect to the Remote Desktop servers. See the KSU VPN page for details on how to obtain and use the VPN client.
Where is the go button on Mac?
At the top right of the Mac Desktop the word to the right of the apple should say "Finder", from there select the "Go" button.
Does CS have remote desktop access?
The CS Department maintains a server for Remote Desktop access, to which you may connect from anywhere on- or off-campus.
Do you need to log into the intranet to access Detroit Medical Center?
For Detroit Medical Center employees who are on the road or working from home, the following is a list of resources available on the Internet. You do not need to be logged into the intranet in order to access them.
Can DMC employees access Citrix?
DMC employees and partners can use these links to access their email, Citrix platforms, etc.
What is the DCRI for Citrix?
For NIH Clinical Center users, the Department of Clinical Research Informatics (DCRI) User Support Team will provide assistance to update your workstation if needed so it is able to access the new Citrix web site. Please contact the CC Service Center at 301-496-8400 for assistance.
Do you need to be on the NIH network to access CRIS?
Note: You must be on the NIH network to access CRIS.
What is Citrix for SPU?
Citrix is an online service for Faculty and Staff that allows you to access your SPU My Documents, Departmental File Shares, and other SPU specific applications from a personal device with internet access. Citrix can also be used to connect to your on-campus desktop device.
What is remote desktop connection?
Remote Desktop Connections allow employees to login to on-campus desktop devices from home or other remote locations. This must be enabled individual per user and computer. Please read here for more details: Remote Desktop Connection.
What is VPN-PRIVDATA?
The VPN-PRIVDATA and VPN-CIS are available to CIS staff and other users with privileged system access (see Privileged System Access Policy ). These VPNs grant all the same access as the SPU VPN and additional access appropriate for these roles.
What is SPU VPN?
The SPU VPN is the legacy VPN solution for faculty and staff. It is currently being phased out and new installations are not encouraged. For more details, including instructions on how to connect: SPU VPN.
What is Fortinet VPN?
The Fortinet VPN is the new VPN solution for faculty and staff being launched during Fall 2020. It is available to Seattle Pacific University faculty and staff using SPU managed devices. The Fortinet VPN provides a secure tunnel to the campus network from client computers connected to the Internet. For more details, including instructions on how to connect: Fortinet VPN.
