
Routing and remote access service (RRAS
RRAS
Ras-related protein R-Ras is a protein that in humans is encoded by the RRAS gene.
What is the routing and remote access service?
The Routing and Remote Access (RemoteAccess) service provides multiprotocol LAN-to-LAN, LAN-to-WAN, VPN, and NAT routing services. This service also provides dial-up and VPN remote access services.
What are the benefits of remote access?
This secure connection provides access to all internal network resources, such as messaging, file and print sharing, and Web server access. The remote character of this connection is transparent to the user, so the overall experience of using remote access is similar to that of working at a workstation on a local network.
How do I enable routing and remote access in Windows Server 2003?
Installing the Routing and Remote Access Service By default, the Routing and Remote Access service is installed automatically during the Windows Server 2003 installation, but it is disabled. To Enable the Routing and Remote Access Service Click Start, point to Administrative Tools, and then click Routing and Remote Access.
What types of routing services does it offer?
It offers routing services to businesses in local area network (LAN) and wide area network (WAN) environments or over the Internet by using secure VPN connections. Routing is used for multiprotocol LAN-to-LAN, LAN-to-WAN, VPN, and network address translation (NAT) routing services.

What is the purpose of routing and remote access?
Routing and Remote Access Service (RRAS) is a Microsoft API and server software that makes it possible to create applications to administer the routing and remote access service capabilities of the operating system, to function as a network router. Developers can also use RRAS to implement routing protocols.
Which network service is commonly used to remotely access routers?
Techopedia Explains Routing and Remote Access Service (RRAS) RRAS provides a remote user with access to an internal network via a secured virtual private network (VPN) connection. This connectivity can be deployed using typical IP-based VPN over the Internet.
What is the difference between RAS and RRAS?
Microsoft Remote Access Server (RAS) is the predecessor to Microsoft Routing and Remote Access Server (RRAS). RRAS is a Microsoft Windows Server feature that allows Microsoft Windows clients to remotely access a Microsoft Windows network.
How do I access routing and remote access?
Click Start, point to Administrative Tools, and then click Routing and Remote Access. In the console tree, expand Routing and Remote Access, expand the server name, and then click Remote Access Policies.
What is remote accessing?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
What is Routing and Remote Access service in Windows 10?
RRAS is a software router and an open platform for routing and networking. It offers routing services to businesses in local area network (LAN) and wide area network (WAN) environments or over the Internet by using secure VPN connections.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
Is RAS secure?
NT 4.0's Remote Access Service (RAS) offers much more than encrypted authentication. Microsoft claims that using NT RAS to dial in remotely is even more secure than logging on to a LAN file server.
Which authentication methods does NPS use?
NPS supports both password-based and certificate-based authentication methods. However, not all network access servers support the same authentication methods. In some cases, you might want to deploy a different authentication method based on the type of network access.
Can DHCP support Remote Access?
When you enable Dynamic Host Configuration Protocol (DHCP) to assign a static IP address to an onboard network interface during first-time setup, you can complete the configuration remotely by using an SSH client. If your system includes an e0M interface, the system broadcasts a DHCP request through it.
How do I remotely access another computer from intranet?
Setup a Remote Desktop Connection for LAN / WAN AccessEnable Remote Desktop Connection on the Host Computer. Windows Remote Desktop Properties. ... Launch Remote Desktop Connection utility on the client computer (laptop, etc.) Launch Application. ... Connect to the host computer. ... Set Options for Remote Desktop Connection.
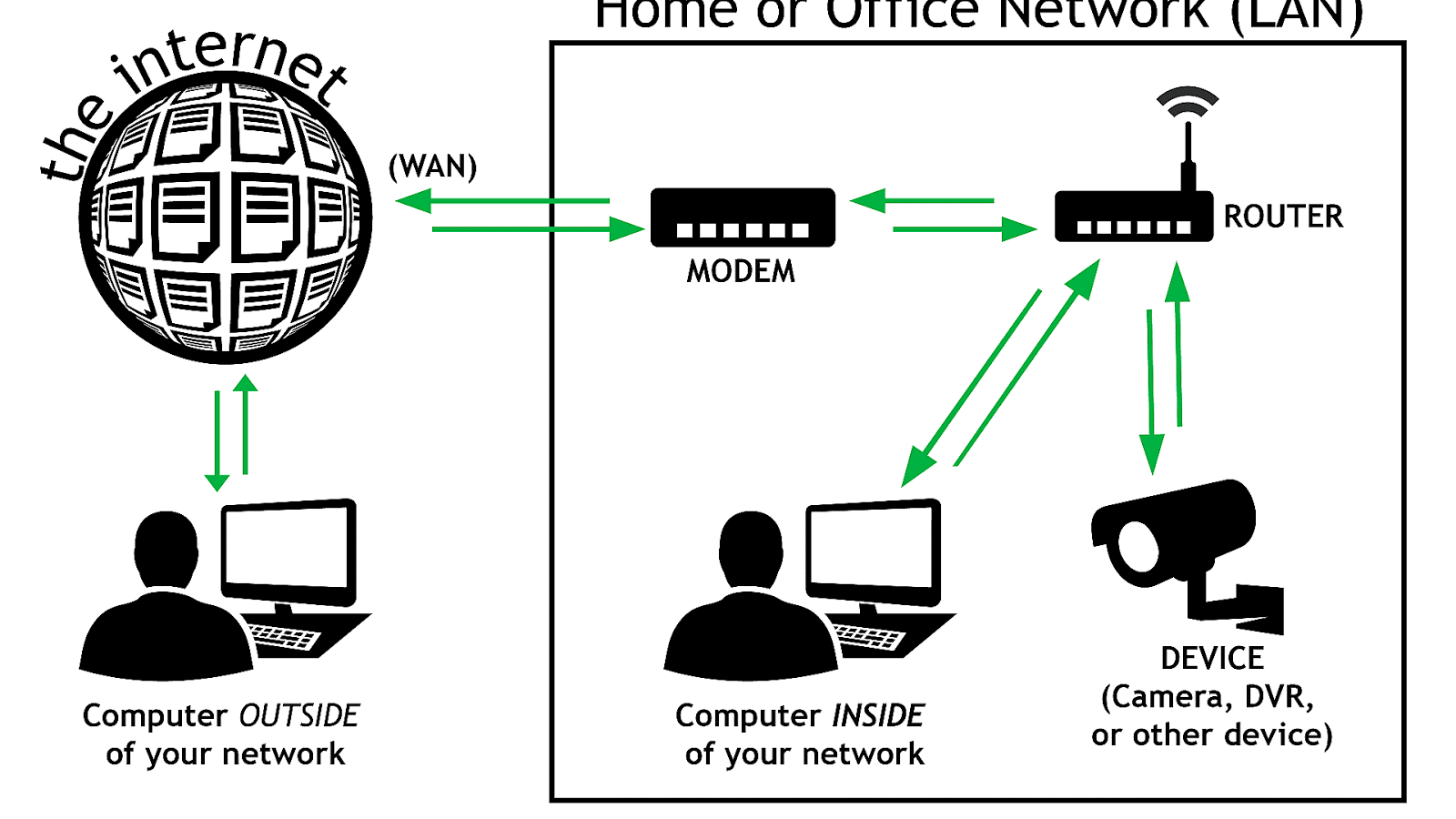
What is SOHO LAN?
SOHO LANs. One of the most common local-area deployments is the Small-Office / Home-Office LAN (SOHO). It is a small computer network usually built of one Ethernet switch, one router, and one wireless access point. The LAN uses Ethernet cables to connect different end-devices to one of the switch ports.
How do I VPN to my home network?
To setup your home router as a VPN server:Open up your preferred browser.Enter your router's LAN (internal) IP address into the search bar. ... Enter the router's username and password. ... Go into Settings (or Advanced Settings) > VPN Service.Enable the VPN Service.More items...•
How do I setup a wireless router as an access point?
0:461:55How to Set Up a Wireless Access Point | Internet Setup - YouTubeYouTubeStart of suggested clipEnd of suggested clipBut other times all you have to do is just open your web browser. And. The access point shouldMoreBut other times all you have to do is just open your web browser. And. The access point should automatically. Take you to the setup page just.
What network device is needed in order to have the type connection?
The primary piece of hardware you need is a modem. The type of Internet access you choose will determine the type of modem you need. Dial-up access uses a telephone modem, DSL service uses a DSL modem, cable access uses a cable modem, and satellite service uses a satellite adapter.
What is a RRAS?
If you are using Hyper-V Network Virtualization or you have VM networks deployed with VLANs, you can deploy RRAS as a virtual machine (VM)-based software gateway and router that allows Cloud Service Providers (CSPs) and Enterprises to enable datacenter and cloud network traffic routing between virtual and physical networks, including the Internet.
Is RRAS available in Server 2012?
The RRAS Multitenant Gateway is available only in Windows Server 2012 R2. It is not available in Windows Server® 2012.
How does RRAS work?
RRAS also supports direct or site-to-site connectivity between two different remote servers.
What is a rras?
Routing and remote access service (RRAS) is a suite of network services in the Windows Server family that enables a server to perform the services of a conventional router.
Remote Access Workforce Benefits
Since the history of remote access software, one of the major benefits of this approach is that a large on-site IT staff presence is not necessary, and therefore most of the routine maintenance work can be farmed out to outside vendors.
Remote Access Benefiting Company Performance
Efficiency can be greatly increased for some employees such as sales people and others that may work largely outside the workplace with their clients. Often, these people spend large amounts of time shuttling back and forth between the office and client locations, but with a remote access solution most of this wasted time can be eliminated.
What is remote access?
Remote access is a double-edged sword when it comes to system security. You see, although it comes with data encryption, access controls, and activity logging, it happens to introduce additional vulnerabilities that could be used as attack points.
Can anyone remotely access a network?
A fully remotely accessible network is not something that anyone can randomly set up. Even seasoned experts and managed service providers take days to piece together all the infrastructure resources and, ultimately, have everything working seamlessly.
How to enable remote access to a server?
Right-click the server, and then click Configure and Enable Routing and Remote Accessto start the Routing and Remote Access Server Setup Wizard. Click Next.
How to connect to a dial up network?
If they are, see your product documentation to complete these steps. Click Start, click Control Panel, and then double-click Network Connections. Under Network Tasks, click Create a new connection, and then click Next. Click Connect to the network at my workplace to create the dial-up connection, and then click Next.
What are the two types of users that need privileged accounts?
Many organizations need to provide privileged accounts to two types of users: internal users (employees) and external users (technology vendors and contractors). However, organizations that use vendors or contractors must protect themselves against potential threats from these sources.
Why do companies use VPNs?
For all these reasons, VPNs have become a popular option for companies who need to give their employees remote access, but want to provide online security and privacy.
Why is VPN important?
To fully achieve its goals, a VPN must accomplish two important tasks: Protect that connection, so that your files (and your company’s network) won’t be compromised. VPNs achieve this second step by encrypting data, these encryption and masking features help protect your online activities and keep them anonymous.
What are some applications that can be shared on desktop?
There are many applications made possible by desktop sharing including remote support, webinars, and online conferences with audio and visual content (presentation sharing), and real-time global collaboration on projects.
Is desktop sharing good for enterprise?
Second, desktop sharing tools are not the best solution for supporting enterprise environments. While these tools can be utilized to provide desktop support and handle helpdesk tasks, they typically don’t have the security and functionality required for complex enterprise remote support such as server or application maintenance. They often lack the strict security controls ( logging and audit) that enterprises in highly-regulated industries need. Also, while desktop sharing can be useful for end-user support, there are additional tools and protocols needed when supporting servers, databases, and other enterprise applications.
Can anyone log into a desktop sharing tool?
Anyone, anywhere, can log into a desktop sharing tool if they have the credentials, meaning they have access to the whole network as if they are in the building. During a remote support session, if an employee surrenders control of their machine to a remote rep whose account has been compromised, your company’s internal sensitive files could become visible to bad actors and used for nefarious purposes.
Is VPN good for remote access?
VPNs may be good for internal employees, but are not optimal for third-party vendors. Desktop sharing tools may be useful for desktop support and helpdesk, but are not good for complex enterprise remote support. PAM provides improvements over VPN and desktop sharing, but there is only one solution that combines the best of all these types of remote access technologies into one and is purpose-built for vendors and doesn’t include any of the drawbacks: VPAM.
What is remote access technology?
A common remote access technology in use today is the IPsec VPN. A piece of software called a VPN client is installed on the end user’s computer and is configured with details about the target network, such as the gateway IP address and a pre-shared security key. Each time the user wants to connect to the corporate network, they start the VPN client, which creates a secure connection to the corporate firewall.
Is VPN required for telecommuting?
Being able to connect securely to your corporate network from a remote location using a Virtual Private Network (VPN) is important, and it may be required by your job if you are a telecommuter. There are some remote access technologies that are widely used, but some new methods have recently emerged that have the ability to change how we work.
Is DirectAccess going to be widespread?
DirectAccess is not going to gain widespread adoption until the OS licensing requirements are revised and the networking is reworked to be more straightforward. While IPv6 is the future of networking, we currently live and work in an IPv4 world, especially on the LAN (as of May 2014, IPv4 still carried more than 96% of Internet traffic worldwide, according to Google ). Setting up a new remote access technology should not require one or more potentially expensive projects before it can be deployed.
Benefits of Remote Access
- The benefits of remote access are fairly obvious. That being said, it's important to have an understanding of them and how to communicate these benefits. These benefits apply to full-time network administrators and managed service providers alike.
Scripting
- Remote control doesn't mean just active administration. Network technicians can automate administration with a number of different tools. Some of these tools, such as WSUS, Group Policy, and Powershell, are embedded within operating systems. In other cases, third-party tools can be used. To know which tool is best to use, administrators must understand the situation that they …
Remote Access Best Practices
- Allowing remote access into a PC or server opens any system up to privacy issues. While it is important for the end-users to be concerned about their own privacy, it's also necessary for network professionals and MSPs to follow a set of best practices to protect the rights of their clients.
Security
- Similar to privacy concerns, enabling remote access on your network increases your potential surface for attack from would-be hackers. It’s crucial to take a second look at all of your firewall configurations to be sure that nothing is opened up unnecessarily. User authentication practices should be reviewed, locked down and enforced appropriately.