Full Answer
What is a remote access trojan (RAT)?
A remote access trojan (RAT), also called creepware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim.
What is the zuorat remote access trojan?
Dubbed ZuoRAT, the remote access Trojan is part of a broader hacking campaign that has existed since at least the fourth quarter of 2020 and continues to operate. The discovery of custom-built malware written for the MIPS architecture and compiled for small-office and home-office routers is significant, particularly given its range of capabilities.
Which is the Best Antivirus for remote access trojan detection?
Remote Access Trojan Detection 1 Avast 2 AVG 3 Avira 4 Bitdefender 5 Kaspersky 6 Malwarebytes 7 McAfee 8 Microsoft Windows Defender 9 Norton 10 PC Matic 11 Sophos 12 Trend Micro More ...
How do I link to myasus remote desktop using Windows 10 Pro?
*Link to MyASUS Remote Desktop function currently only supports Windows 10 Pro version* 1. In Link to MyASUS side please click the ① [Information] (" " symbol) icon to enter the ② [Password] interface in the system settings and add an account password. (If you have already set the account password, please ignore this step) 2.

Is remote access a malware?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is ZuoRAT malware?
ZuoRAT is a remote access trojan (RAT) that attacks small office/home office (SOHO) routers. On June 29, 2022, Black Lotus Labs, the threat intelligence arm of Lumen Technologies, revealed the existence of this vulnerability. The code appears to be a heavily modified version of the code behind the Mirai botnet.
What is Cyclops Blink malware?
Cyclops Blink is a botnet attributed to Sandworm, a Russian nation-state threat group previously credited with the VPNFilter botnet, as well as the destructive NotPetya attacks in 2017 and the BlackEnergy Trojan used in Ukrainian critical infrastructure attacks in 2016.
Are Asus routers secure?
With WPA2 encryption and TLS protocols, the connections between ASUS Router and your connected devices, as well as between ASUS Router and the external Internet are both private and protected.
What is sandworm virus?
Sandworm is an experienced cyber-espionage threat group that has been associated with the Russian Military Unit 74455 of the Main Intelligence Directorate (GRU). CERT-UA has shared indicators of compromise (Yara rules, file hashes, hosts, network) to help prevent new attacks from this threat actor.
What do botnets steal?
Financial breach– includes botnets specifically designed for the direct theft of funds from enterprises and credit card information. Financial botnets, like the ZeuS botnet, have been responsible for attacks involving millions of dollars stolen directly from multiple enterprises over very short periods of time.
How does VPNFilter work?
VPNFilter operates in multiple stages that include initial infection, command-and-control (C&C) communications, and the third stage, in which the payloads are deployed. These payloads perform the tasks that the malware has been intended to do. This is also where the Modbus portion of the malware is found.
How do I secure my ASUS wireless router?
[Wireless] How to make my router more secure?Set up separate passwords for your wireless network and Web GUI. ... Use long and more complex passwords. ... Update your router to the latest firmware. ... Enable the firewall. ... Enable AiProtection. ... Disable the access from WAN. ... Disable Telnet and SSH.More items...•
Why is ASUS router login not secure?
The default certificate in the router is self-signed and doesn't fulfill the default SSL policy of the browser. Then your connection status will show Not Secure in the front of the URL bar. Follow the steps to download certification and update to your Browser.
Should I disable web access from WAN?
You should keep that setting disabled, unless you are willing to put your router at risk. You cannot completely disable the web interface, and the LAN port over http cannot be changed. If you really need to free up port 80, you could switch it to HTTPS-only - https allows you to select which port to use.
What is Cyclops blink WatchGuard?
You can use the WatchGuard System Manager Cyclops Blink Detector to determine if your Firebox is affected by Cyclops Blink. The tool can scan single locally-managed and cloud-managed Fireboxes, as well as scan single or multiple Fireboxes managed by WSM Management Server.
Who killed Cyclops Greek mythology?
The Cyclops also forged a trident for Poseidon and the Helmet of Darkness for Hades. The god Apollo slew the Cyclops after they struck his son (or were wrongly blamed for) striking his son Aesculapius with lightning.
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
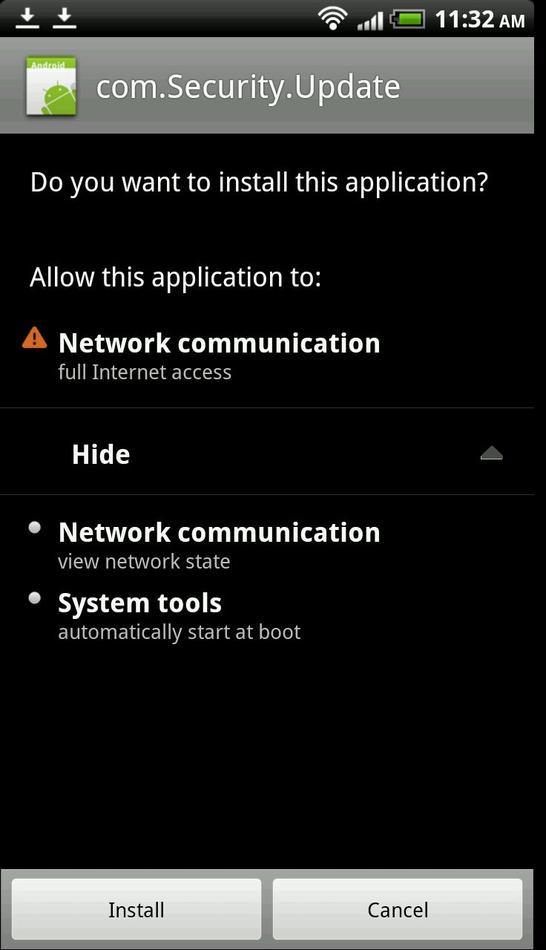
How are Remote Access Trojans Useful to Hackers?
Attackers using remote control malware cut power to 80,000 people by remotely accessing a computer authenticated into SCADA (supervisor y control and data acquisition) machines that controlled the country’s utility infrastructure. RAT software made it possible for the attacker to access sensitive resources through bypassing the authenticated user's elevated privileges on the network. Having access to critical machines that control city resources and infrastructure is one of the biggest dangers of RAT malware.
Why do attackers use remote devices?
Instead of storing the content on their own servers and cloud devices, attackers use targeted stolen devices so that they can avoid having accounts and servers shut down for illegal content.
What is remote control software?
Legitimate remote-control software exists to enable an administrator to control a device remotely. For example, administrators use Remote Desktop Protocol (RDP) configured on a Windows server to remotely manage a system physically located at another site such as a data center. Physical access to the data center isn’t available to administrators, so RDP gives them access to configure the server and manage it for corporate productivity.
How to install a RAT?
An attacker must convince the user to install a RAT either by downloading malicious software from the web or running an executable from a malicious email attachment or message. RATs can also be installed using macros in Microsoft Word or Excel documents. When a user allows the macro to run on a device, the macro silently downloads RAT malware and installs it. With the RAT installed, an attacker can now remotely control the desktop, including mouse movement, mouse clicks, camera controls, keyboard actions, and any configured peripherals.
How do remote access Trojans work?
The Remote Access Trojans get themselves downloaded on a device if the victims click on any attachment in an email or from a game. It enables the attacker to get control over the device and monitor the activities or gaining remote access. This RAT makes itself undetected on the device, and they remain in the device for a longer period of time for getting data that may be confidential.
What is the most powerful Trojan?
One of the most powerful Trojans that are popularly used by the attacker or hacker is Remote Access Trojan. This is mostly used for malicious purposes. This Trojan ensures the stealthy way of accumulating data by making itself undetected. Now, these Trojans have the capacity to perform various functions that damages the victim.
What is the advantage of remote access?
Advantage of Remote Access Trojans : It can be used to capture screenshots. The attacker can activate the webcam, or they can record video. The RAT can be used to delete the files or alter files in the system. It can also be used to capture screenshots.