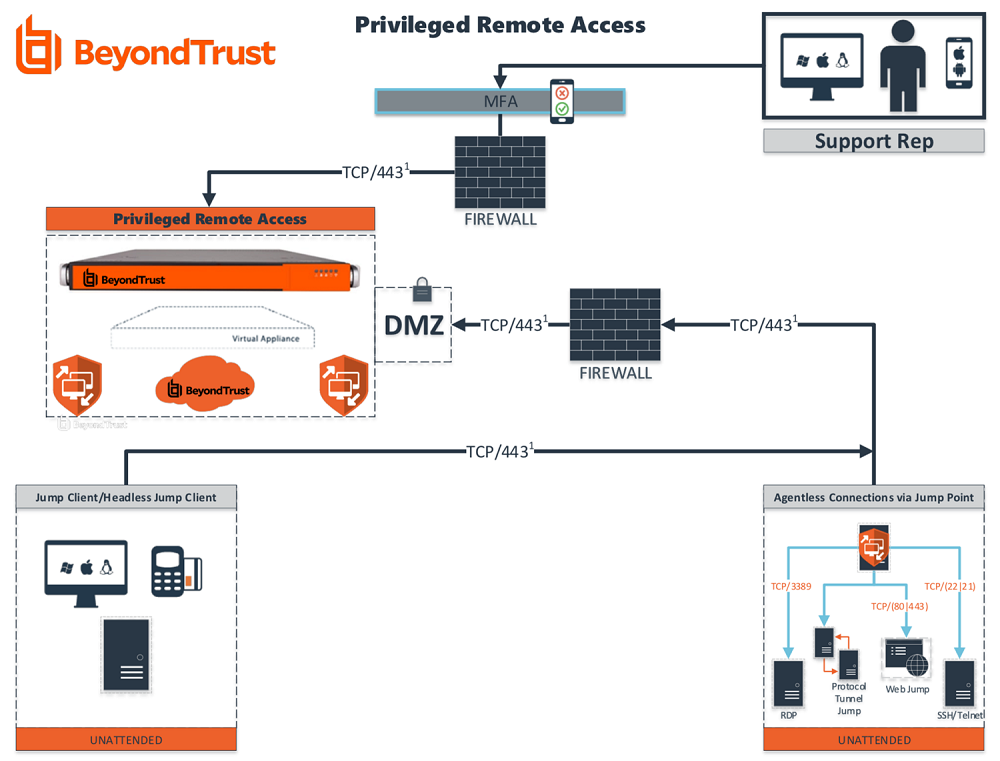
What are potential risks associated with remote access?
Remote work challenges for teams
- Managing projects. Starting right at the top, the biggest challenge with remote working is managing projects when your team is spread out across multiple locations.
- Remote collaboration. The most common challenge remote teams report in studies is collaborating from different locations. ...
- Tracking tasks and productivity. ...
How to mitigate risk with remote access?
- Ensure your employees have all they need to securely work from home and know who to contact if they face an IT or security issue.
- Schedule basic security awareness training for your employees. ...
- Take key data protection measures including switching on password protection, encrypting work devices and ensuring data is backed up.
How to protect remote access?
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address. ...
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
What are the risk of remote access?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
What are the security risks of remote working?
Top Security Risks of Remote WorkingGDPR and remote working. Remote work means an employer has less control and visibility over employees' data security. ... Phishing Emails. ... Weak Passwords. ... Unsecured Home Devices. ... Unencrypted File Sharing. ... Open Home WiFi Networks.
What is the greatest risk that remote access poses to an organization?
The overriding risk of remote access services and software is a hacker gaining deeper access to your organization, exposing you to a host of IT security threats. Once they gain privileged access to your system, it will be difficult to prevent data loss, prevent phishing, protect against ransomware, etc.
What can we do in order to limit or prevent remote access?
Firewalls can be your first line of defense in network security by limiting those who have remote access. You should set up firewalls to restrict access using software or hardware or both. Update your software regularly. Make sure your software updates automatically so you're working with the latest security fixes.
How do you keep security when employees work remotely?
Remote Work Security Best PracticesEstablish and enforce a data security policy. ... Equip your employees with the right tools and technology. ... Frequently update your network security systems. ... Regulate the use of personal devices. ... Institute a “Zero Trust” approach. ... Make sure all internet connections are secure.More items...
How do you protect and secure data while working remotely?
How to promote data security while working remotelyConnect to a hotspot or use a VPN. ... Use strong passwords and a password manager. ... Keep work and personal separate. ... Stay alert for phishing or other attacks. ... Participate in routine cybersecurity training.
How do you secure remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What are remote access attacks?
A remote attack is a malicious action that targets one or a network of computers. The remote attack does not affect the computer the attacker is using. Instead, the attacker will find vulnerable points in a computer or network's security software to access the machine or system.
Does working remote increases cyber security risks?
One of the most significant security risks of remote working is using personal devices to connect to corporate networks and systems. These devices often do not have the same level of cybersecurity as a corporate computer or laptop.
Which of these is the most important security precaution you should take when working remotely?
Here are a few security best practices your remote employees should follow.Run software updates regularly. ... Secure video meetings. ... Watch out for email phishing. ... Create strong passwords. ... Never leave your bag, briefcase or laptop unattended. ... Use caution with wireless networks. ... Keep your work separate.
What is the first risk in network security?
The first risk is a lack of information about traditional network security technologies, such as firewalls and intrusion prevention systems, as those systems may be largely out of the equation now.
What is the essence of an organization's network security challenge?
The essence of an organization's network security challenge is users are now, more than ever, making security decisions on the network team's behalf. Teams should think about what they can do to minimize such decisions or at least minimize their effect on the business. Consider the following methods.
Is there a tangible risk to security?
Unless and until technical staff, employees and management are working toward the same goals in terms of security standards, policies and expectations, there will be tangible risks. Most people have already established their baseline in this new normal. However, from what I'm seeing and hearing from clients and colleagues, there are still lots of opportunities to properly mitigate certain threats and vulnerabilities.
Is it time to do more of the same with network security?
Now is not the time to do more of the same with network security. Instead, you've got to figure out how to get your users working for you rather than against you. The same boring messages and dictates are not going to work. You'll have to get creative as you address remote access security.
Why Are Remote Workers More Vulnerable?
Remote workers come in many different forms. Some remote workers work for a dedicated employer that provides them with the tech they need and others make use of their own equipment.
Insecure Wifi
Remote workers that work outside of a home office typically need a network connection to perform their duties. This need for a connection can cause temptations for remote workers to use potentially insecure public wifi hotspots.
Cloud-Based Environment
Remote workers often require a technology stack that is heavily reliant on cloud computing. The use of cloud computing provides an advantage by saving the costs of implementing a custom solution for key services, however, the use of cloud computing comes with its own unique set of cybersecurity risks.
Remote Worker Bad Habits
Let’s face it, nobody is perfect. Unfortunately, the bad habits that we often manage to get away with in our personal lives can have serious cybersecurity implications in the corporate world.
Traveling
One of the benefits of remote working is the flexibility of movement that comes with mobile devices. No longer bound to dedicated office space, remote workers have the opportunity to work in planes, trains, hotels, airports, and more. Unfortunately, location independence also comes with its own unique set of risks.
What is the risk of using the same password on multiple devices?
According to a survey by Google in 2019, 65 percent of people reuse the same password across multiple platforms. This explains why the Verizon Data Breach Investigations Report found that compromised passwords directly cause 81 percent of hacking-related breaches. In addition, personal devices cannot be controlled and audited for frequent updates, security software and access to potentially harmful content.
Why is it important to have access to company owned devices?
Having access to devices utilized through the provision of company-owned devices is a guaranteed way to mitigate risk and improve private information security. If you’re also in an industry that relies on mobile devices to accomplish work-related tasks on the go, it’s advisable to implement a mobile device management solution to prevent data breaches should a smartphone or tablet ever be lost or stolen.
What is Remote Access, and Why Is It Important?
Remote access is any technology that enables users to access a device, system, or network from outside locations or locations that they typically cannot access. Companies often use a local area network (LAN), a wide area network (WAN), or a virtual private network (VPN) to establish such remote connections.
What is remote access technology?
Remote Access Technology gives businesses and their employees a means to connect with employees. The technology, however, is not without its challenges. Security, in particular, became a noticeable issue in this remote setup. Cyber security teams now face unique challenges to protect the mobile workforce from pernicious attacks.
Why should you establish strong remote access policies and send out informational materials about phishing scams and the like?
It also helps to hold online security training to increase the team’s awareness about remote access risks.
What are the most commonly exploited applications worldwide?
Office applications were the most commonly exploited applications worldwide. Remote access risks can lead to hackers accessing your company’s files and exposing you to serious IT security threats.
Why do companies use remote desktops?
With the spread of the COVID-19 pandemic, more and more businesses have sought remote work to prevent employees from risking their lives going to the office. It forced companies to adapt to the times using digital means. It brought the emergence of many remote desktop software that allows teams to stay connected wherever they are in the globe.
How much will the remote access market grow in 2025?
Remote access is especially important given the growing number of employees working from home. The Remote Access Software market is expected to grow by 15.71% from 2020 to 2025.
Why are mobile phones so vulnerable to security breaches?
Mobile phones are especially prone to security breaches as we frequently install different applications with them . An article by Symantec revealed that 1 in 36 mobile phones had high-risk apps. The article said that mobile ransomware infections also increased by 33% in 2018.
What happens when remote staff connect to the internet?
When remote staff connect to business systems over their home WiFi or public internet it can create a breeding ground for cybersecurity attacks. Phishers and cyber-criminals target these types of connections, looking for ways to infiltrate a business network through these weakened connections.
What is remote work?
The shift in remote work means a rise in the number of unsecured, personal devices connecting to your network from outside of the office. Employees are using the same laptops, mobile devices, and tablets for work and personal use, opening up the possibility for malware and viruses to enter your private network.
Why is email important for remote staff?
Because remote staff no longer have the ability to communicate with their coworkers in person, the need for alternative methods of communication increases significantly. The use of email becomes an increasingly important method of communication for remote staff, opening up the likelihood of phishing scams and the spread of malware.
Do employees forget to connect to VPN?
Of course, there will be times when employees simply forget to connect through the VPN before accessing business tools, like email. After all, they’re only human! While they may understand that cybersecurity is an important part of remote work, they may not realize the true impact.
Is remote work the norm?
Remote work is quickly becoming the norm for many businesses across the globe. Whether it be a strategic decision to cut costs on office space or due to the global COVID-19 pandemic, more businesses are opting to break the ties of cubicle life and moving to a remote strategy.
Are Your Remote Staff Protected?
Enabling your workforce with remote capabilities doesn’t have to be a nightmare. Our team at Custom Computer Specialists understands the shortcomings of remote infrastructure and what to do to protect your critical business assets from cyber-criminals.
