
What is third-party remote access?
Third-party remote access is the system in which external users are able to connect with a defined network. The best third-party remote access platform will make sure that the connection is secure, controlled, and monitored at all times. Sadly, many enterprises still give their third-party vendors credentials that often provide privileged access.
Why do companies allow remote access to vendors and services providers?
But many organizations are also allowing access to vendors and services providers because offices remain closed or they are restricting physical access to the office. Additionally, this third-party remote access is happening through organizations outsourcing specific tasks so that they can focus on their core business functions.
What are remote access utilities and how do they work?
These are exactly the scenarios that remote access utilities are made to handle. Remote access apps let you either access your home or office computer from another location, or allow others to have access to some or all of your files, as if they were actually sitting in front of your PC instead of somewhere else entirely.
What are remote access apps and how do they work?
Remote access apps let you either access your home or office computer from another location, or allow others to have access to some or all of your files, as if they were actually sitting in front of your PC instead of somewhere else entirely.
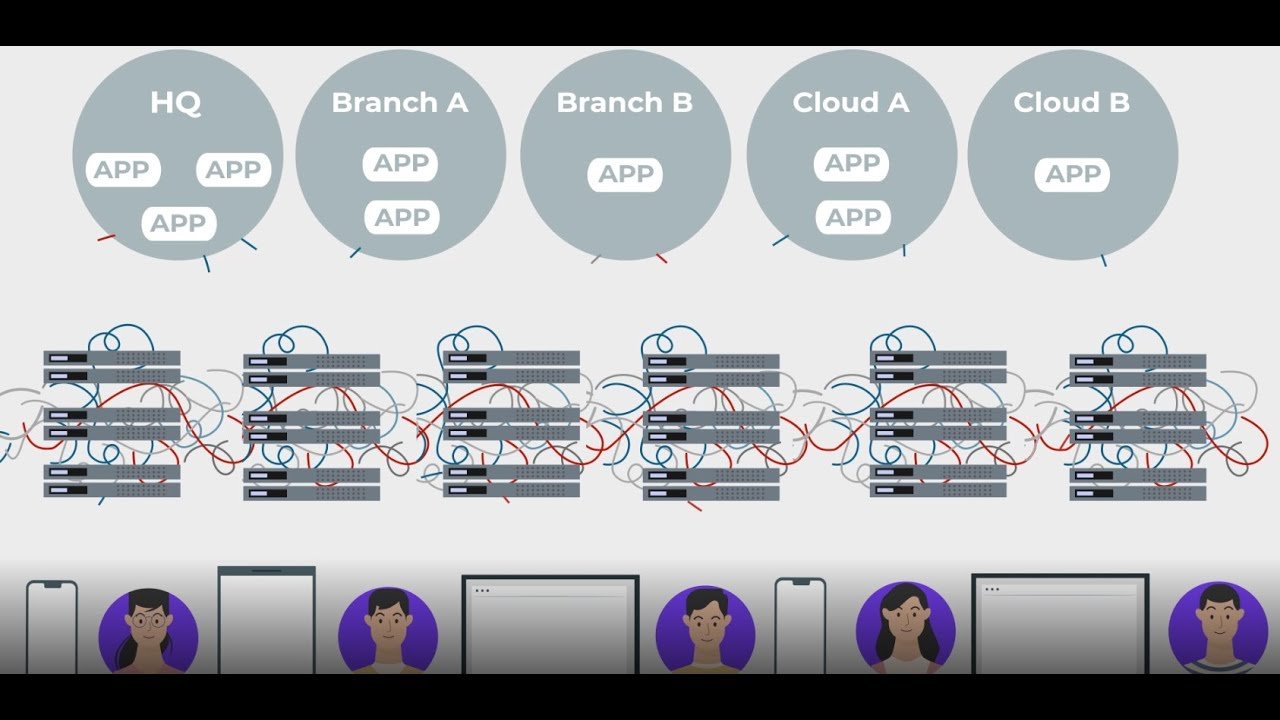
What is a remote access system?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What are third party connections?
Third Party Connection A direct connection to a party external to the Board. Examples of third party connections include connections to customers, vendors, partners, or suppliers.
What is third party VPN?
Third-party VPN services work by installing software, a browser plugin or a security hardware appliance between end devices and the internet. A VPN tunnel is then established between the end-user device and the service provider's VPN endpoint on the internet.
What are the different types of remote access methods?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
How can you tell if a app is third party?
Review what a third party can access Go to the Security section of your Google Account. Under “Third-party apps with account access,” select Manage third-party access. Select the app or service you want to review.
How do you use third party data?
Third-party data is information collected by an entity that isn't directly connected to the user the data is being collected on....Here are some ways to use third-party data in your digital marketing strategy.Show Ads to Refined Audiences. ... Drill Down Insights. ... Refine Your Own Audience. ... Personalize the User Experience.
What are the risks of third-party VPN services?
The Not-So-Good VPN Security RisksThird-party VPNs can't create or enforce policies that protect credentials. ... More secure VPN = Less productive workforce. ... High VPN support costs = Higher cost of doing business. ... All or nothing = VPNs create security risks. ... Lack of accountability creates third-party VPN risks.More items...•
Is a VPN a third-party app?
And one of the easiest ways to do that is using a third-party virtual private network, or VPN. As we've previously mentioned, a VPN is a service that allows users to connect to the internet via a third-party server which in-turn encrypts all of the user's data.
Can my employer track my location through VPN?
Using VPN software will ensure that no one can know your real location by checking your IP address (internet address), whether it's your boss, clients, or IT department. You do need to get a subscription to a VPN service to do this.
What are two types of remote access servers?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
Which technology is used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are three examples of remote access locations?
What Is Remote Access?Queens College.Harvard University Extension School.
How do I download a free VPN for Windows 10?
Download Vpn Free For Windows 10 - Best Software & AppsHamachi. 2.3.0.78. 3.4. (41290 votes) ... IPVanish. 3.7.5.7. 4.2. (521 votes) ... Free VPN. 3.2. 3.3. (3552 votes) ... Avast Secure Browser. (551 votes) Free Download for Windows. ... Chedot. 86.0.4240.932. 4.5. ... iTop VPN. 1.3.0.967. 4.3. ... VyprVPN for Windows. 4.3.1.10763. 3.7. ... Windscribe. 2.4.10. 4.2.More items...
How can incorrectly configuring VPN clients lead to a security breach?
How can incorrectly configuring VPN clients lead to a security breach? A virtual private network (VPN) operates pretty much in binary mode: Either the secure connection is established or it isn't. If the secure connection does not successfully complete, it is not possible to send traffic to the secured resources.
What is a third party service?
Third parties provide services like IT/IS, HR, software support, sales, and other related support and business operations services depending on the type of organization. Nonetheless, it does not matter the type of access it is; what matters is how the third-party access is managed, and how the business assures the access is secure. The organization must manage the risk from third-party activity.
When can controls be put in place to manage the access accordingly?
Once the full picture is visible and understood , controls can be put in place to manage the access accordingly.
What does reporting access do?
By reporting the access, the organization has visibility and can determine if the access is still required. For instance, if there has been no access for several months, an informed decision can be made regarding if the third-party access is still required going forward. Some organizations have policies in place to shut the access if it’s not used for 60 days, and this is made visible through reporting. The access can be reapproved when it’s requested again. By doing this, the attack surface area is reduced.
What is a matrix once access has been mapped?
Once the access has been mapped, a matrix can be created of who is accessing what from where and when (then links can be defined). At this point, consideration of systems that monitor access is undertaken to decide on an effective system to implement.
Vendor Privileged Access Manager Demo Video
CyberArk Vendor PAM gives the ability to invite, provision and give vendors privileged access. In this video, we'll show how to invite and give a vendor specific privileged access to a target system.
Vendor PAM Datasheet
Learn more about CyberArk Vendor PAM, a born in the cloud SaaS solution that helps organizations secure external vendor access to critical internal systems.
Vendor Privilege Access Management
Listen here for a 45 minute session on CyberArk Vendor PAM to provide external vendors with fast and secure access to critical systems managed within CyberArk PAM.
Remote Access Datasheet
CyberArk Remote Access helps organizations secure external vendor access to critical systems without the need for VPNs, agents or passwords.
Securing Remote Infrastructure: Keep Friends Close & Enemies Closer – Session 2 of 3
2020 has intensified demands around supply chains and external cloud services provision. This session looks at the IT Administration and Support teams, who continue to perform their duties remotely.
Enable New Ways of Work: Simplified Remote User Privileged Access with SaaS
Organizations everywhere are undertaking major digital transformation initiatives. Whether moving critical resources to the cloud, or investing in greater automation capabilities, COVID-19 has...
Time to Re-examine Remote Access After VPN Password Leak
Just days ago, a list of plaintext usernames, passwords and IP addresses for more than 900 Pulse Secure VPN servers was published online along with SSH keys for each server, a list of all local...
What is privileged credentials?
These should never be handed to vendors. Restricted controls are the only way to securely manage third-party remote access. While some third-parties may need privileged permissions to support their technology on an enterprise network, sweeping access should not be given. Ensure user accounts aren’t shared and every action is tied to an individual – helping ensure accountability and compliance.
What is the first step in two factor authentication?
The first step is making sure the user attempting to access your network is authorized and authenticated. Two-factor authentication should be baked into your access management systems. It demands two independent identity checks that will stifle intruders holding stolen passwords. You want the two factors to authenticate the identity of the user as well as confirm the user has authorized access. Requiring a simple username and password does neither of these.
What Is Remote Access Software?
Remote access software lets one computer view or control another computer, not merely across a network, but from anywhere in the world. You might use it to log into your customers' computers and show them how to run a program, or sort out their technical troubles. Or you can even use it to invite friends or clients to view your desktop while you run a demo for them. You can use the screen as a temporary whiteboard, drawing lines and circles that help friends or clients understand what you're doing on your machine or theirs.
What is remote PC?
RemotePC is one of the best low-frills remote-access apps, offering identical features on PCs and Macs, fast performance, and a minimal, but intuitive, interface .
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
Does GoToMyPC work with TeamViewer?
GoToMyPC and LogMeIn add the ability to drag and drop files between the local desktop and the viewer window that displays the desktop of the remote machine, but this feature works only when connecting to and from Windows computers. TeamViewer has a FileBox window into which you can drag files that will be accessible to both machines. LogMeIn, TeamViewer, and VNC Connect include whiteboard features for drawing lines in the viewer. For more on each remote access apps individual features, see the individual reviews, which are linked to below.
What is remote PC?
RemotePC is a hugely-popular remote computer access application that’s suitable for both home and—in particular—for business users. It uses cloud technology to deliver class-leading remote access solutions through an intuitive web application and native desktop and mobile apps. It also includes collaboration features such as voice chat.
How long does it take to set up a remote access?
Using remote access software is simple. They generally take no more than a few minutes to set up, and you will usually have to install the software on the computer or other device you want to access the remote computer with.
What is the best remote desktop software?
RemotePC is the best remote desktop software right now. RemotePC is another stellar product from the team at iDrive (we also recommend its excellent cloud storage solution). RemotePC uses top-notch cloud tech to deliver class-leading remote access. Web, desktop, and mobile apps provide the access.
What is remote desktop manager?
Remote Desktop Manager is a powerful remote computer access program offering scalable solutions for large businesses. It’s compatible with both Android and iOS devices and comes with a selection of impressive security features.
What is Zoho Assist?
Cloud-based Zoho Assist is one of our favorite remote access tools because it enables you to access almost any device. It provides specialized remote support and unattended access plans designed to streamline workflow processes.
What is Connectwise Control?
ConnectWise Control provides highly specialized remote access solutions targeted at specific users. Its three Support plans come with some remote access features, and include powerful tools to help IT staff and support technicians solve problems remotely. The Access plan caters for 25 devices and is aimed at those who want to connect with numerous remote devices.
How many computers can splashtop support?
Prices for Splashtop Business Access enables remote access to a specified number of computers. Remote Support plans cater for up to 25 computers, and SOS on-demand support is the highest end plan.

Third-Party Remote Access Definition
- Third-party remote access is the system in which external users are able to connect with a defined network. The best third-party remote access platformwill make sure that the connection is secure, controlled, and monitored at all times. Sadly, many enterprises still give their third-party vendors credentials that often provide privileged access. Fr...
Third-Party Best Practices: Securing Your Access Points
- Now is the time to get your vendors and platform aligned. The best way to protect your most valuable assets and make sure your vendors stay safe in case of a breach is to practice critical access management. Made up of three pillars (access governance, access control, and access monitoring), employing the best techniques to practice third-party access management is the be…
Third-Party Access Control
- Access control, or having precision and control over when and how a person can exercise their access rights, can apply to both internal and external users. It’s especially important to apply types of access control to third parties, as they carry with them the biggest risk. Access control is an additional layer of security on top of access governance that helps protect those assets that …